
This blog post explains my finding when an Autopilot Trust Relationship Error for Hybrid AD Joined Device. Today I was testing Hybrid Azure AD Join Autopilot provisioning and every machine I tested with had the same issue; they would briefly flash the Enrollment Status Page (ESP) then show the Windows logon screen as if they had completed successfully and even appeared to be AD joined based on the logon page. When attempting to log in, however, the following message was displayed:
The security database on the server does not have a computer account for this trust relationship.
Generally, this or a similar error shows up when an Active Directory domain-joined device has been deleted from Active Directory or the account has been disabled. In the case of Windows Autopilot, the process for joining a device to Active Directory during Hybrid AD Join uses the Intune Active Directory Connector service to perform an offline domain join (ODJ) for the device.
Michael Niehaus has numerous blogs on these topics if you would like to learn more. Here are some of the ones that I used while troubleshooting.
https://oofhours.com/2020/07/19/troubleshooting-windows-autopilot-hybrid-azure-ad-join/
https://oofhours.com/2019/07/15/inside-windows-autopilot-user-driven-hybrid-azure-ad-join/
Autopilot Trust Relationship Error – Following the Breadcrumbs
Active Directory
Active Directory was my first stop and as I suspected, there was no AD computer object for the device. Not much to do there. If there’s no computer object, that certainly explains why the device can’t log into the domain.
Intune Connector for Active Directory
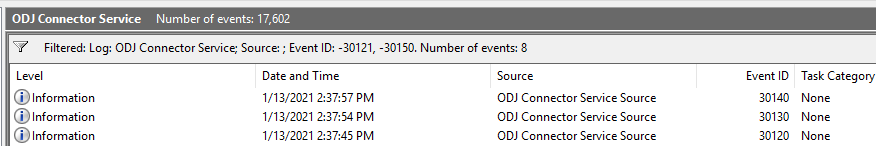
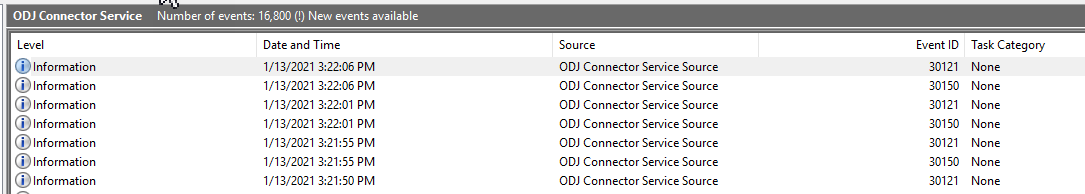
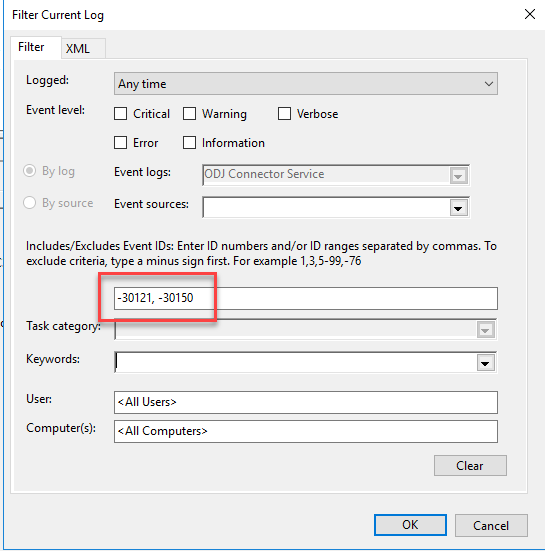
Next was checking my on-premises server with the Intune Connector for Active Directory or ODJ Connector Service installed. The ODJ Connector Service has its own event log so it’s pretty easy to check for issues. Every few seconds the service checks its health and checks for new requests. When healthy, the log ODJ Connector Service event log will be full of event id 30121 and 30150.
As Michael points out in his blog, filtering those event ids out helps greatly. In my case, when I filtered those ids, the log was empty.
The ODJ server never logged that it found any requests. We are looking for event id 30120 (RequestHandlingPipeline_DownloadSuccess) 30130 (RequestOfflineDomainJoinBlob_Success) and 3140 (RequestHandlingPipeline_UploadSuccess) events. Without these, the ODJ request from the Autopilot device isn’t being processed by the server so the new computer object won’t get created in AD.
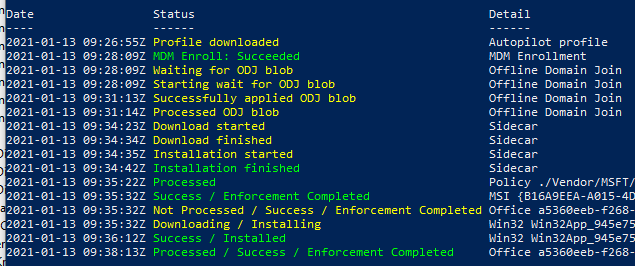
Windows 10 Autopilot Device
Next was back to the client for diagnostics. At this point, the client is sitting at a domain logon screen and the local Administrator account is disabled. I used Microsoft DART tools to unlock the local Administrator account and log in. Michael suggests using NET commands to unlock and reset the password while in OOBE but you have to do this before getting to the logon screen. (https://oofhours.com/2020/07/19/troubleshooting-windows-autopilot-hybrid-azure-ad-join/)
net user Troubleshoot P@ssword /add
net localgroup Administrators Troubleshoot /add
Once I was on the device, I installed and ran the Get-AutopilotDiagnostics.ps1 script. To my surprise, the device showed that it had successfully applied the ODJ blob. But this didn’t make sense since the ODJ server wasn’t ever showing the request. (Tip: if you look in the script, you can see where these values are stored for easier manual troubleshooting)
The Light at the End of the Tunnel
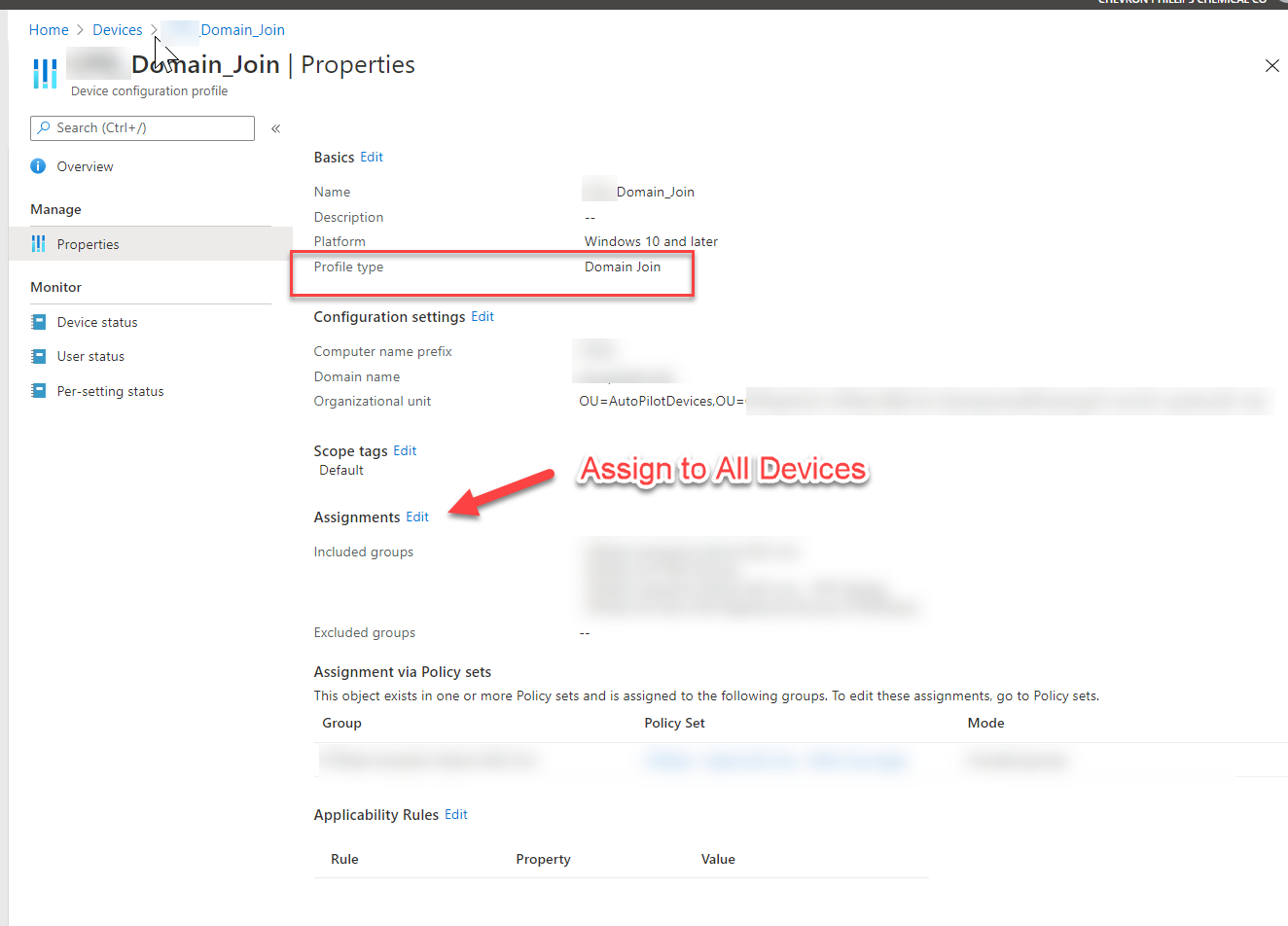
Everything sure was pointing to the ODJ Connector service, but as I dug around a bit more, I found a note in Michael’s post and a Tech Community post that helped me along. Basically, I was only targeting my Intune Domain Join profile to a specific Azure AD Group which only had my Autopilot devices in it but didn’t include the renamed Intune devices.
At this point as a quick test, I deleted the Intune Device object from within the Windows Autopilot devices node for the devices that were failing and tried again. They worked right away.
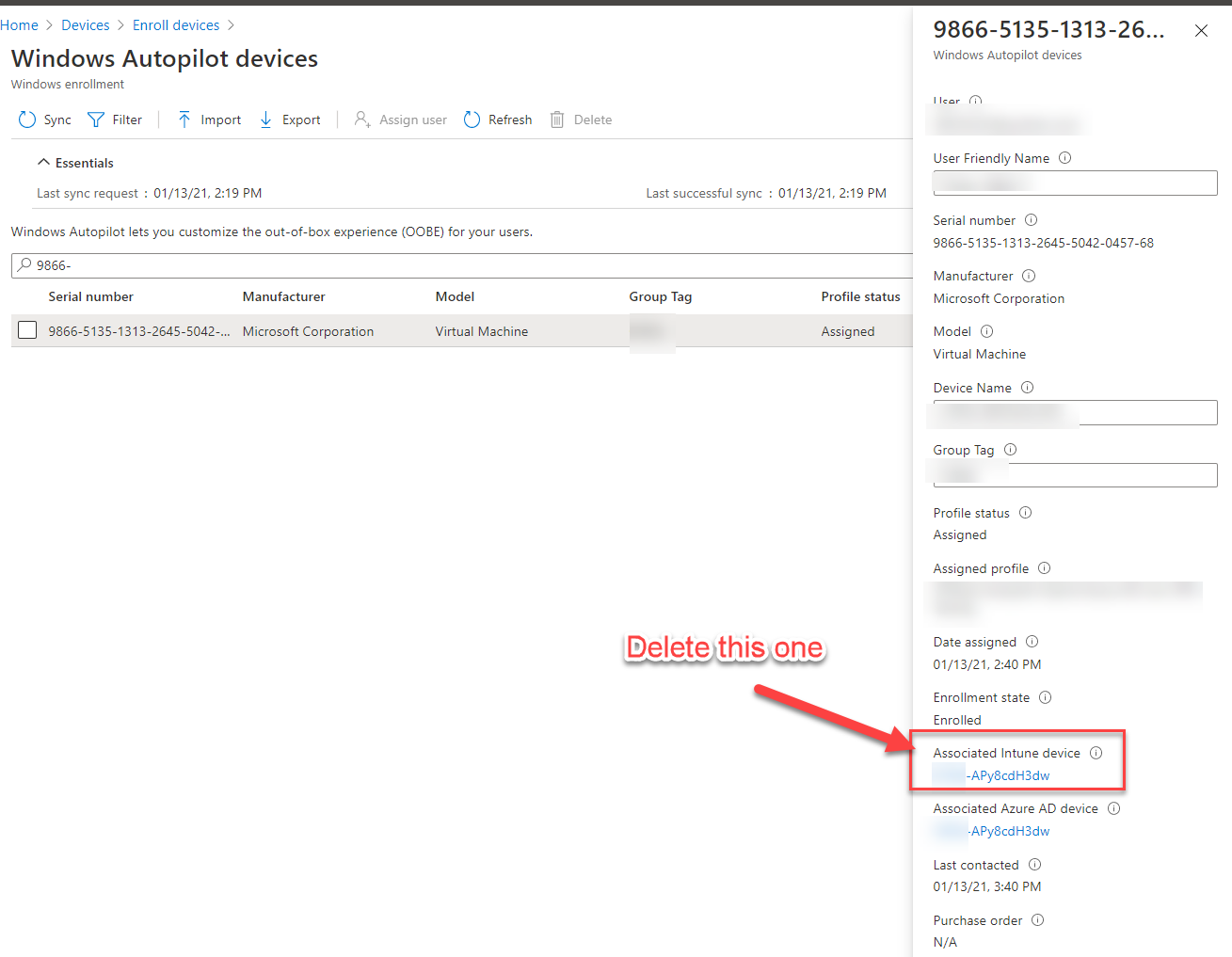
Autopilot Trust Relationship Error – Summary
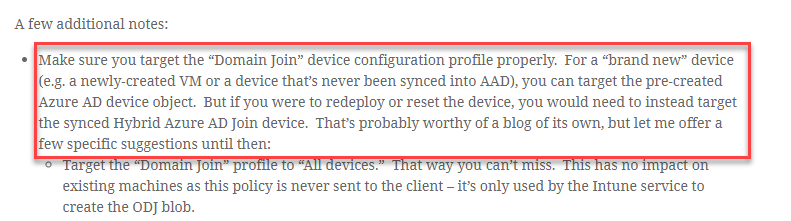
My next step is to do as Michael suggests and deploy the Domain Join profile to All devices to ensure that my Hybrid AD Join devices can be reset and Autopiloted again without this issue. In most cases, you won’t see this, but during testing, this is enough to cause some headaches and delays. Ultimately, Michael had given me the solution in his blog post, it just didn’t click for me until I had gone through the other troubleshooting steps.
Also, thanks to the folks on Twitter who gave me advice on troubleshooting. This community is amazing!
Extra Notes
Later I checked the Intune AutoPilot deployments report and found that the devices were reporting back as successfully completing Autopilot. I suspect that the Domain Join profile was what was breaking things, but that the other configurations didn’t apply to the devices either since they weren’t targeted to the existing Intune device objects, but instead to the Hybrid Autopilot device group. This would explain why it completed so quickly as well.













Dolas
01.14.2021 AT 01:39 PMJonathan Lefebvre
01.15.2021 AT 08:21 AM