
I was asked to restrict domain user access on a Windows 10 device managed by Intune. The computer was configured as a Single-App Kiosk mode so we needed to prevent a user to use CTRL-ALT-DEL and log on the computer using his domain credentials.
After searching through the Intune Device restrictions available for Windows 10, I couldn’t find any UI settings for that. I had to use a Custom Profile type for that. (Custom Profiles are also called OMA-URI Settings) This blog post will describe how to Create an Intune Device Profile Restriction User Login to restrict login rights
This post assumes that you have a valid Intune subscription and that your Windows 10 device is Intune Managed.
- Open the Endpoint Manager Console
- Go to Configuration Profile
- Then click Create Profile at the top
- Platform: Windows 10 and later
- Profile: Custom
- Click Create at the bottom

- In the Basics pane, enter a Name and Description, click Next
- On the Configuration Settings pane, click Add
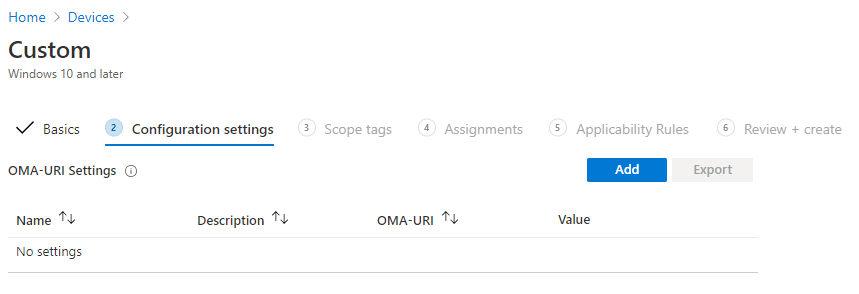
- Enter a Name and Description for your policy
- OMA-URI : ./Device/Vendor/MSFT/Policy/Config/UserRights/AllowLocalLogOn
- Data Type : String
- Value :
<![CDATA[*S-1-5-113]]>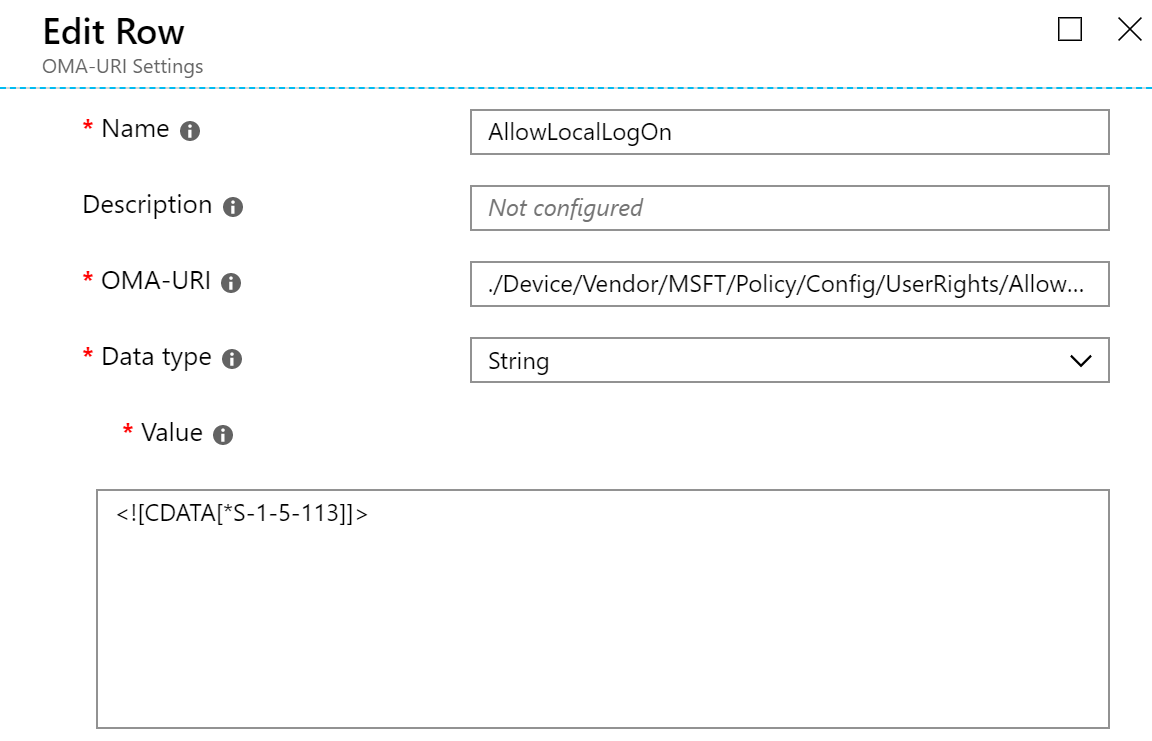
The challenge was to find the correct syntax of the CDATA value. The documentation is stating to use group names like “Administrator” or “Remote Desktop Users” but our testing revealed that is was not working in non-English Operating systems. As mentioned in the comment section of the article we decided to try using the account SID. Reading through the documentation we selected the S-1-5-113 (LOCAL_ACCOUNT). This ensure that only local accounts can log to the machine, preventing our domain user to use their account.
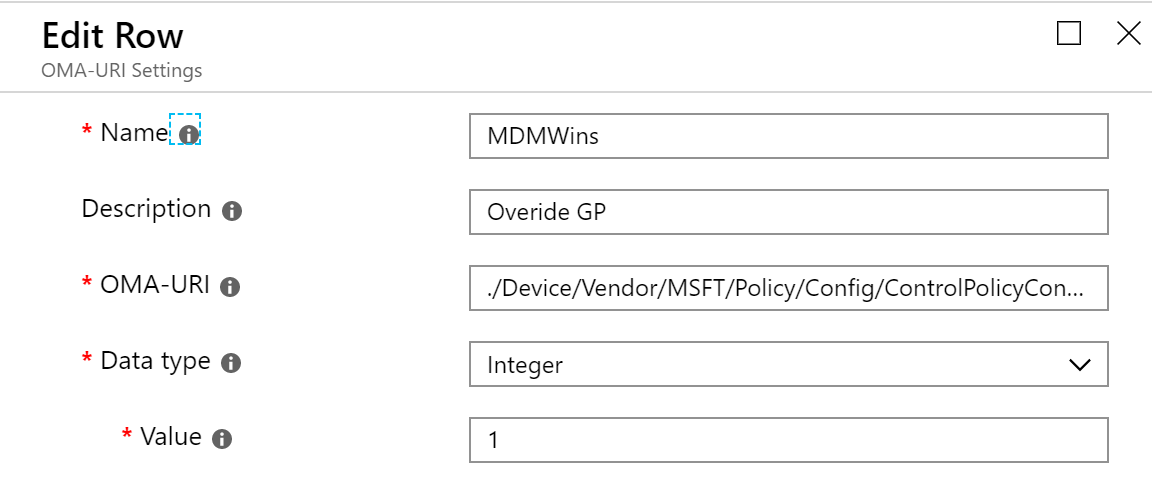
We also decide to add another setting to make sure that the MDM Policy wins over Group policy. Since Windows 1803 there’s a new Policy CSP setting called ControlPolicyConflict that includes the policy of MDMWinsOverGP. This ensures that the Intune policy wins if there’s a group policy with the same settings.
- To add the second settings, on the Custom OMA-URI Settings pane on the right, click Add
- Enter a Name and Description for your policy
- OMA-URI : ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP
- Data Type : Integer
- Value : 1
- Click Ok then Save
- Click on Next
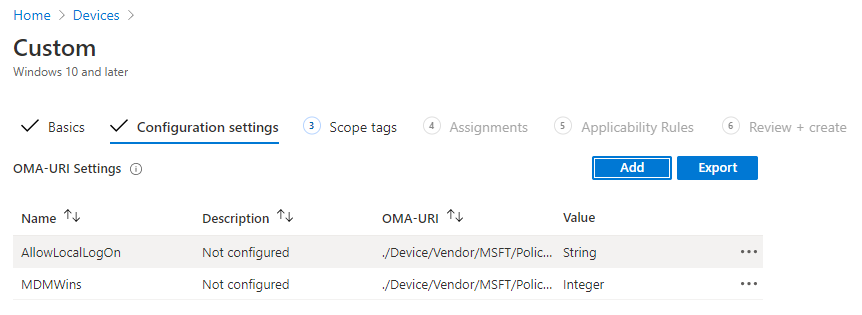
- On the Scope tab, assign a Scope if needed, click Next
- On the Assignments tab, assign your profile to a test device or test group
- In the Applicability Rules tab, assign a rule if needed. Click Next
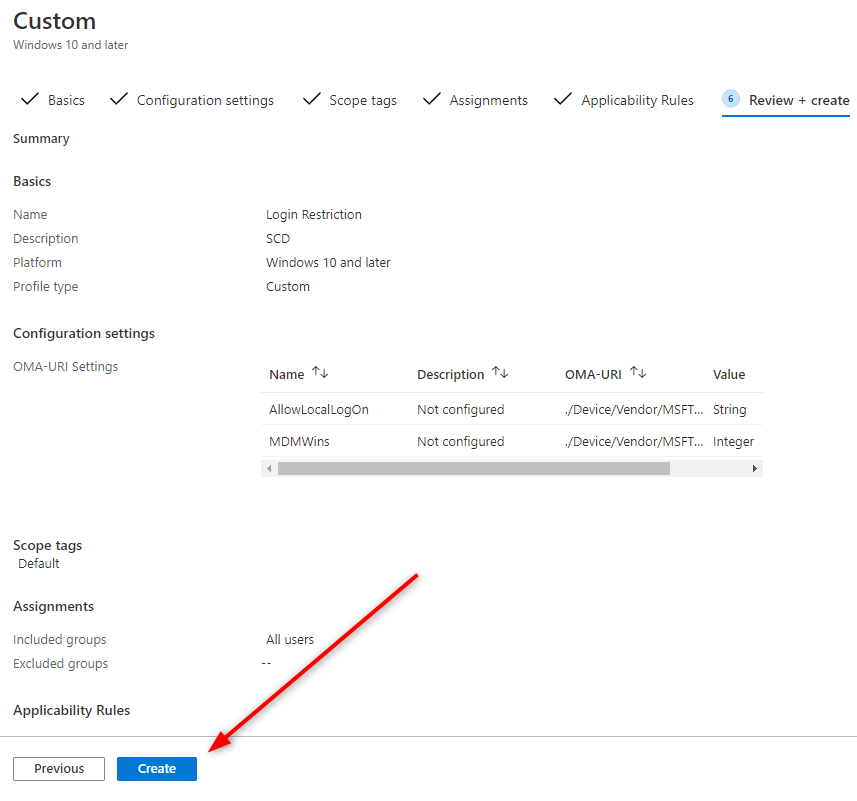
- Review your Configuration Profile and click Create
Intune Device Profile User Login Restriction Monitoring
To monitor the deployment of your Intune Profile :
- Click Device Status at the bottom of the Profile you just created
- The machine(s) that received the profile will be listed, click on it.
- The Device overview pane will open, click on Device Configuration and click your policy on the right
- You can see the deployment status and the last status update, you can click on it to have more information

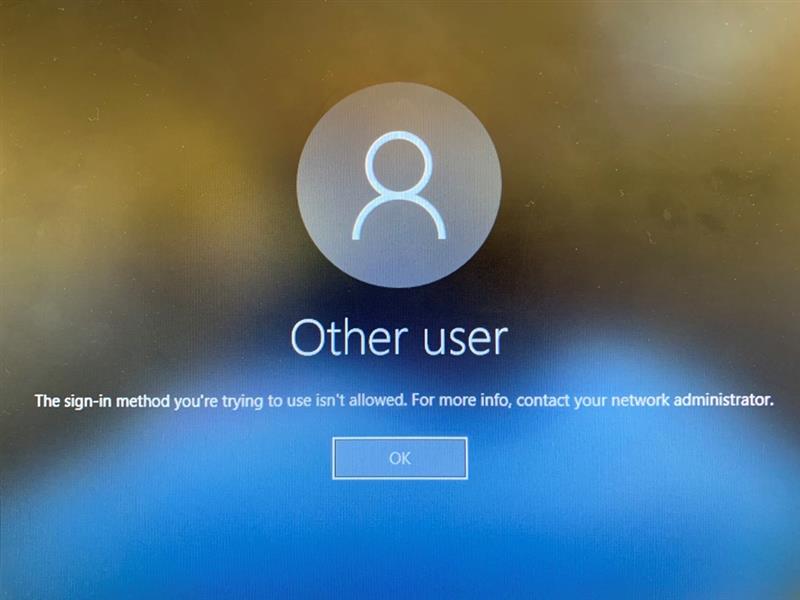
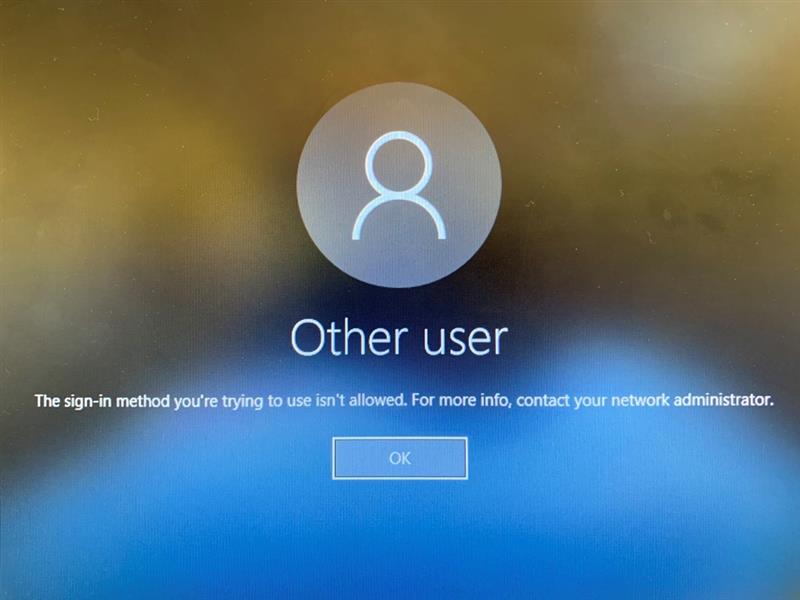
On the Device, when trying to log using a domain account, the users receive the following notification :













Martin J. Little
11.06.2023 AT 11:01 AMVijayakumar Reddy Vakati
04.06.2020 AT 08:09 AMJoe Proctor
02.18.2020 AT 04:43 PMTobias
01.02.2020 AT 06:21 PMPär N
09.26.2019 AT 01:52 AM