
BitLocker Management, also known previously as Microsoft BitLocker Administration and Monitoring(MBAM), has been around MECM for a little while now. Whether a move from an old stand-alone MBAM server, hosted on a Windows Server 2012 R2 for example, or simply a wish to go the extra mile compared to BitLocker with AD backup, it is still a good idea up to today to implement it. In this blog post, we will configure SCCM MBAM Integration with SCCM with detailed steps.
SCCM MBAM Integration Prerequisites
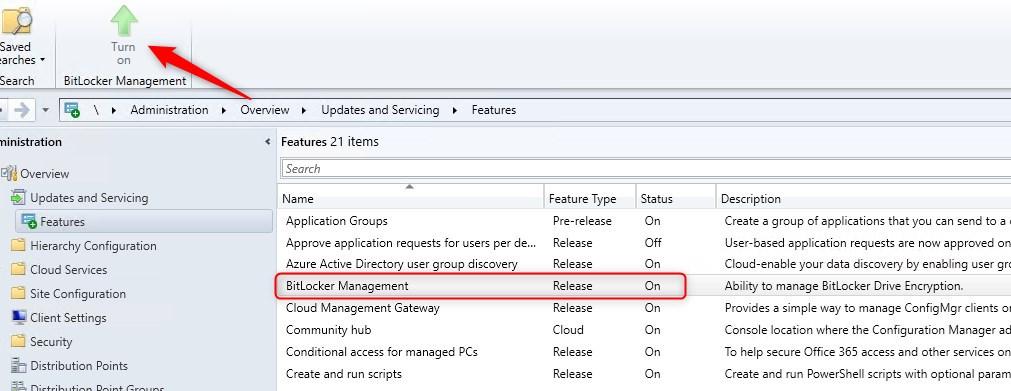
- SCCM should be at minimum version 2103 since the integration is much easier.
- Activate the MECM feature under Administration/Updates and Servicing/Features
- Restart the console to see BitLocker Management under Assets and Compliance/Endpoint Protection
- ASP.NET MVC 4 installed on the server with the Self-service portal, if the Self-service portal is to be configured
For more details on the prerequisites, see Microsoft Docs.
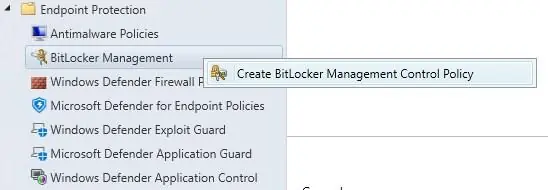
Create BitLocker Management in SCCM
- Once the feature is enabled and the console restarted, browse to Asset and Compliance/Endpoint Protection/BitLocker Management and right-click Create BitLocker Management Control Policy

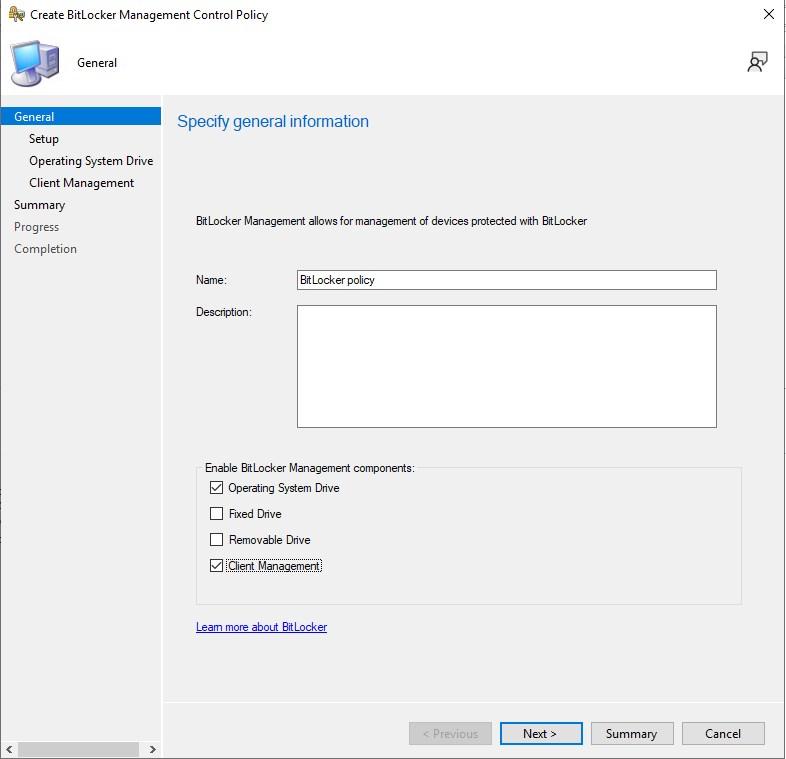
- Set the Name and at a minimum select Operating System Drive and Client Management
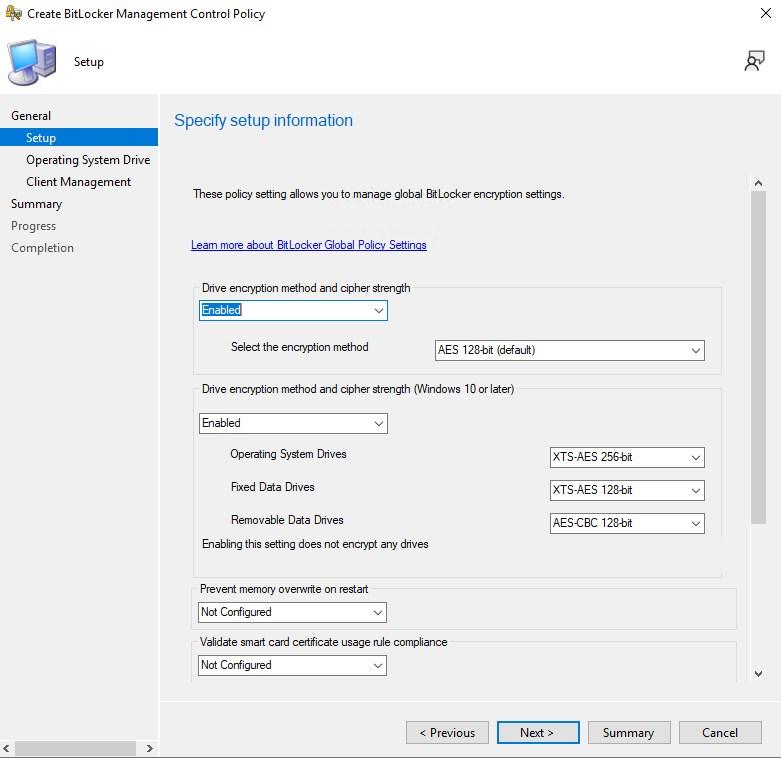
- Define the encryption method per drive type.
- Define TPM requirements for the OS drive
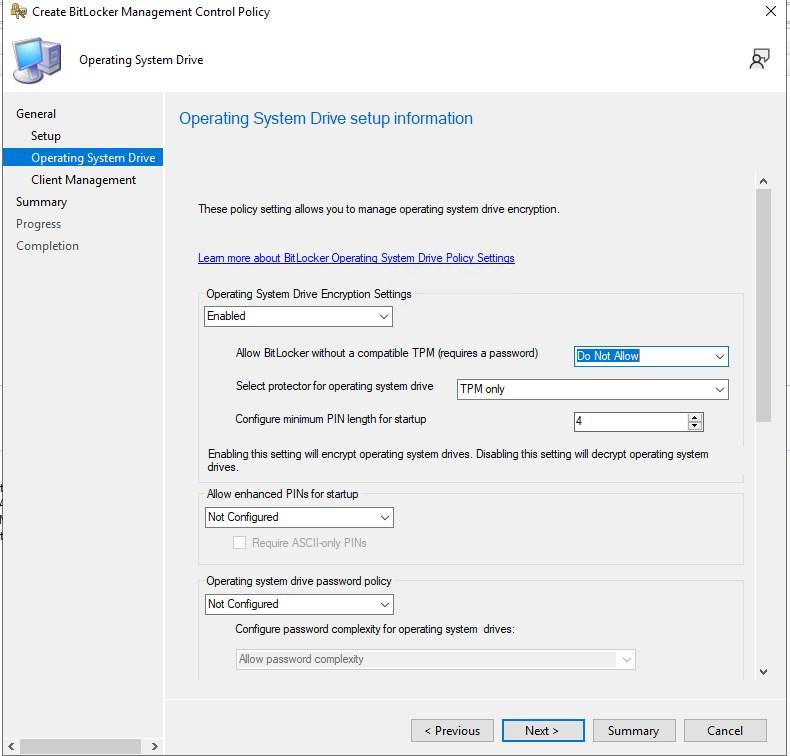
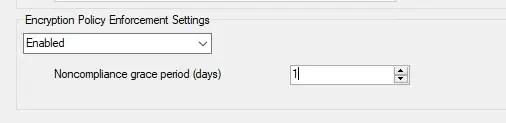
- Make sure to scroll down to select Encryption Policy Enforcment Settings -> Enabled
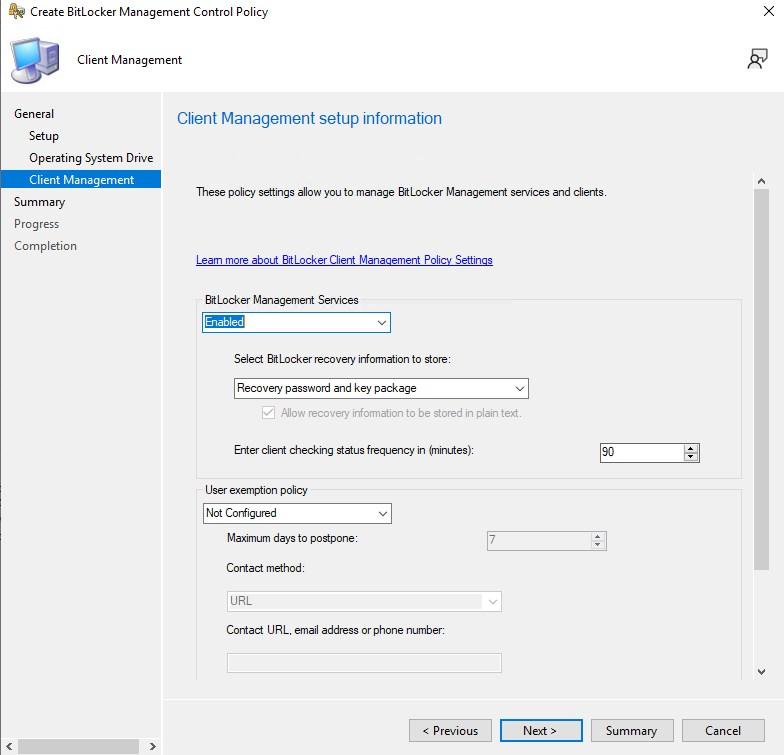
- Enable BitLocker Management Service
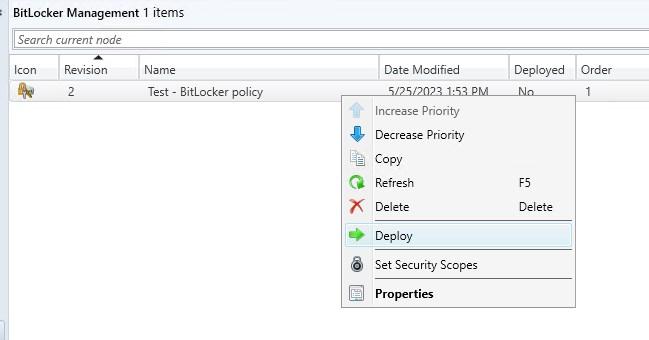
- Deploy the BitLocker Management policy to a collection, just like any other configuration. Testing is obviously recommended!
For more details on Creating the BitLockerment Management policy, see Microsoft Docs
Configure the BitLocker management web portals
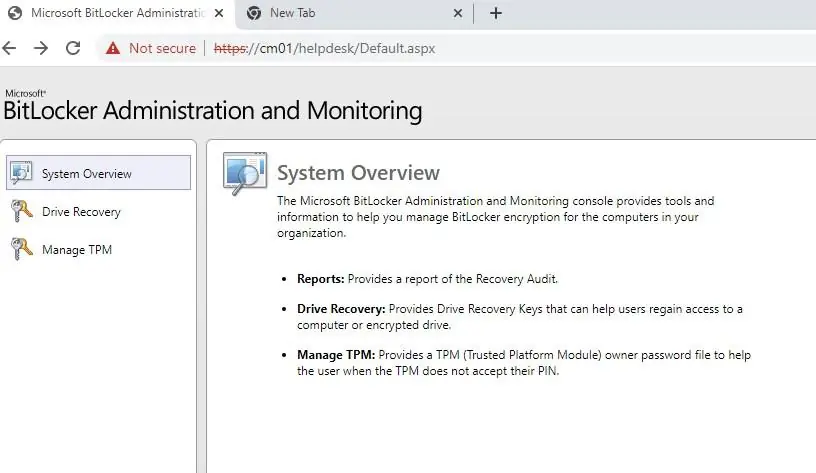
There are 2 portals that can be installed in support of BitLocker Management. Helpdesk Portal, is made for IT folks to request the recovery key after an end-user has an issue and the Self-Service portal, is made for users to request the recovery key. The self-service portal isn’t that much used in general.
- Browse to Program Files\Microsoft Configuration Manager\bin\X64 in a Powershell command ran as administrator

- To install both portals, Run the following command .\MBAMWebSiteInstaller.ps1 -SqlServerName CM01.SCDlab.org -SqlDatabaseName CM_SCD -ReportWebServiceUrl http://cm01/ReportServer -HelpdeskUsersGroupName “<domain\helpdesk>” -HelpdeskAdminsGroupName “<domain\MECM admins>” -MbamReportUsersGroupName “<domain\Report group>” -SiteInstall Both
- If you do not use the Self-Service portal, set the -SiteInstall to Helpdesk
- If you wish to use a custom website instead of the Default Web Site in IIS, first create the custom website in IIS, then use -IISWebsite <site name>
- For more details about all the script usage, see Microsoft Docs
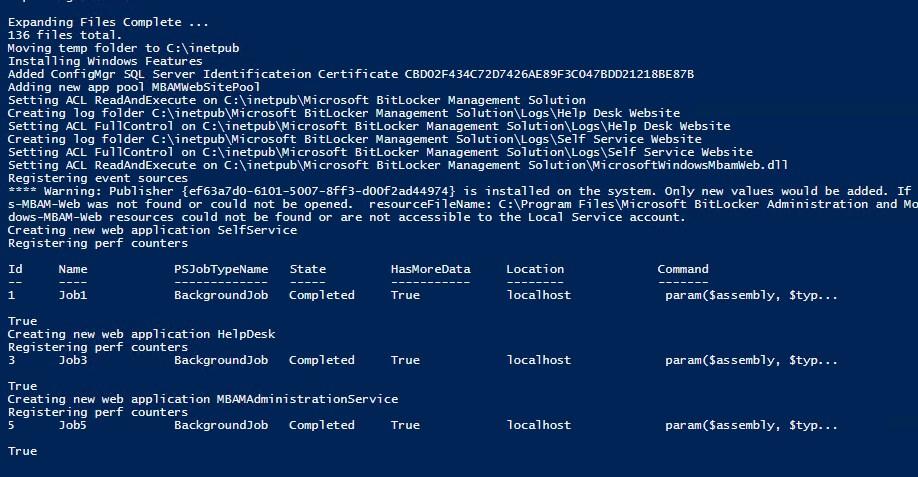
- Once the script is completed, test access to those sites
- http://cm01/selfservice
- http://cm01/helpdesk
By default, portals are supported in HTTP. They rely on IIS certificates binding. To convert them to HTTPS, follow these steps.
For more details about the BitLocker Management web portal, see Microsoft Docs
Additional information and considerations
Reporting
SCCM MBAM integration adds a few reports to the MECM reports.
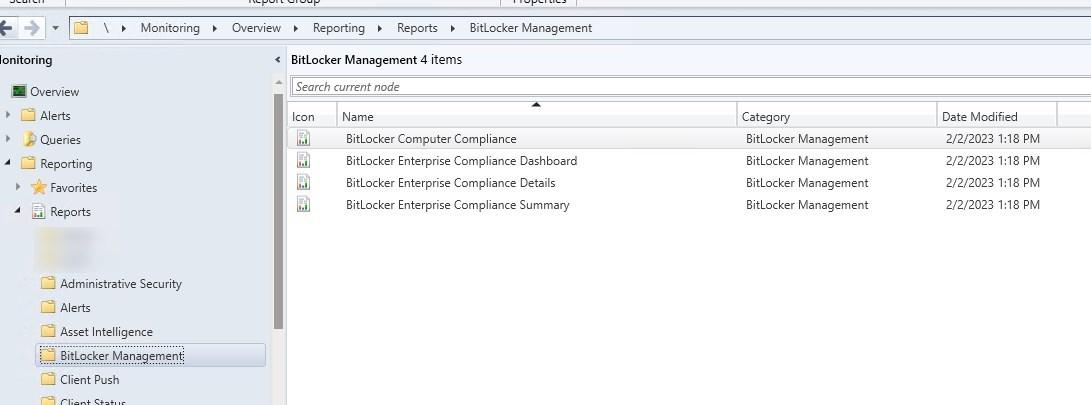
We also offer a free SSRS report and a PowerBi report for BitLocker. Note that following the change to integrate BitLocker Management to MEMC, they only work when a BitLocker Management policy is applied to a device. See our previous post for more details on those reports.
SCCM MBAM Integration – Client logs and events
- Logs can be found under %WinDIR%\CCM\Logs
- BitLockerManagementHandler.log
- BitLockerManagement_GroupPolicyHandler.log
- Events are available under Applications and Services\Microsoft\Windows\MBAM
OS deployment with Task Sequence
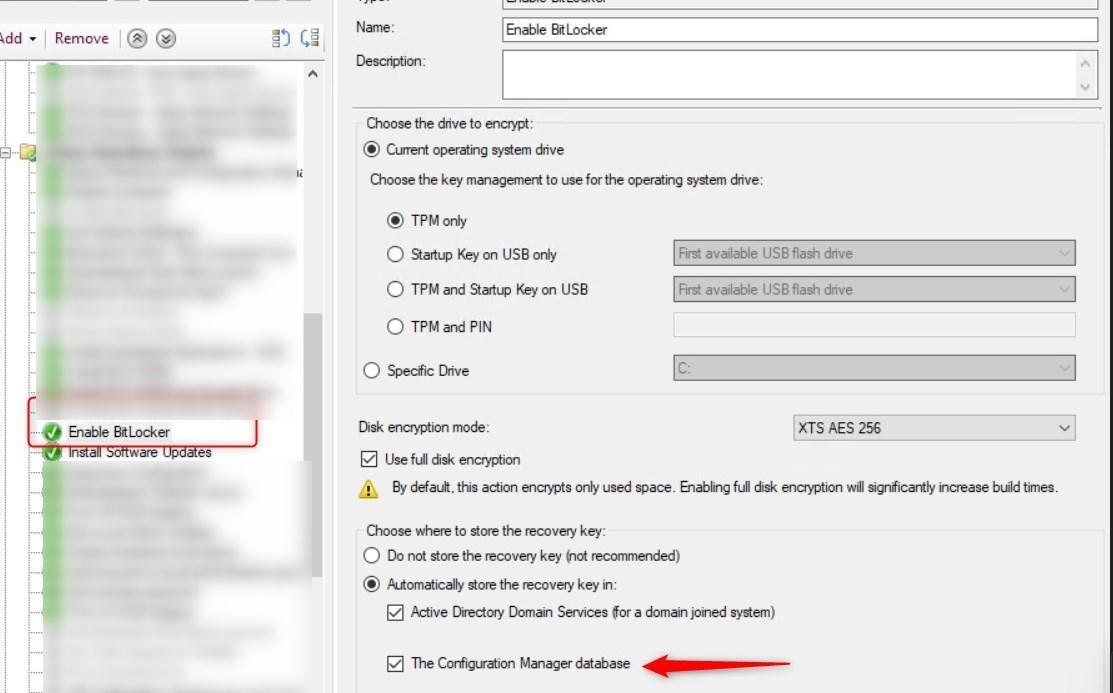
With the BitLocker Management capabilities turned on, it is no longer required to use scripts to enable BitLocker with MBAM. Simply check the box to store the recovery to Configuration Manager Database.
Intune BitLocker Management
Although the MECM integration works great and is fairly simple to integrate, our recommendation remains to use CoManagement and Intune to manage BitLocker.
See our previous post on Managing BitLocker with Intune.
Migration from standalone MBAM
Essentially, migrating from standalone MBAM to the integrated functionality in MECM is fully supported.
Key parts are :
- No re-encryption. If the encryption algorithm is not the same as it was configured for MBAM, MEMC will not re-encrypt the drive. The device will be flagged as non-compliant because of the different encryption algorithm
- MBAM GPO wins over local policies set by MECM. In order words, the GPO must be gone for MECM to take over.
- When a device processes the MECM BitLocker Management policy, it will automatically do a key rotation and upload the new key to MECM.
For more details about Migration from StandAlone MBAM, see Microsoft Docs
For more information on BitLocker Management with Configuration Manager, see Microsoft Docs.













Only authorized users can leave comments
Log In