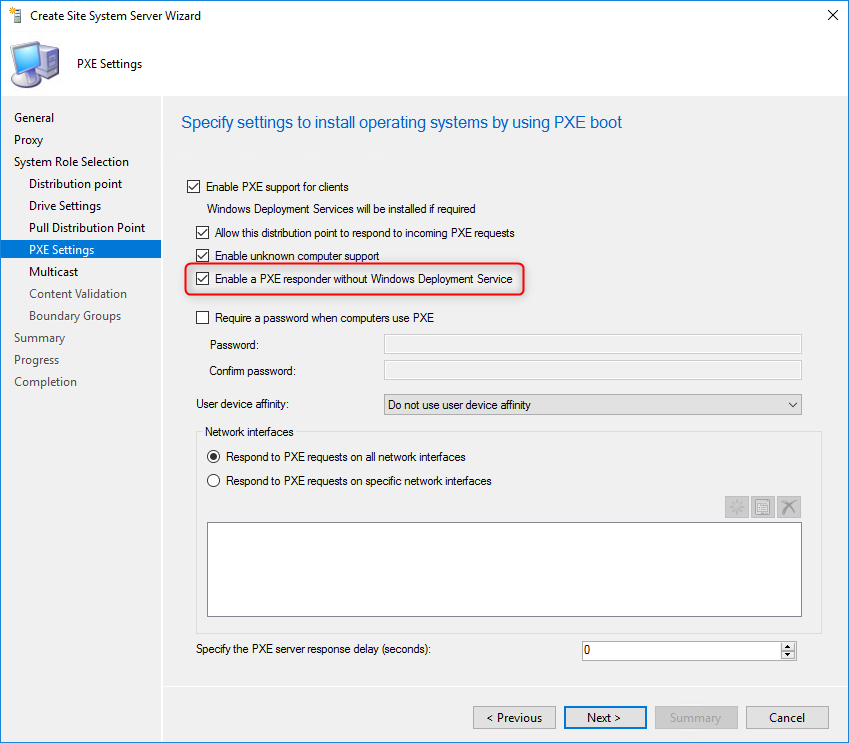

SCCM 1806 bring a new exciting feature that will change the design and planning of SCCM sites. Before 1806, if you had a remote site with only 1 distribution point and wanted to do PXE boot and imaging, you’d have to use a server OS because Windows Deployment Service (WDS) was required. You could also use third party solution with additional cost. Now you can use a client OS (Windows 7,8,10) to respond to PXE request without WDS. This is a game changer as you could basically remove any server OS from remote sites if they were just acting as a distribution point.
SCCM PXE Without WDS Limitation
Note that there’s 1 limitation with SCCM PXE Without WDS. It doesn’t support Multicast, if you need multicast, you need to stick with Windows Deployment Service (WDS).
Existing Distribution Point
You can use the Enable a PXE responder without Windows Deployment Service option on a server OS that that’s already PXE-enabled, SCCM will suspend the Windows Deployment (WDS) Service and enable the new ConfigMgr PXE Responder Service. If you later disable this option but still Enable PXE support for clients, then the distribution point enables Windows Deployment Service (WDS) again.
It’s pretty simple, all you have to do is enable the new Enable a PXE responder without Windows Deployment Service in the Distribution Point Properties option :
- In the SCCM Console
- Go to Administration \ Site Configuration \ Servers and Site System Roles
- Select your Distribution Point and right-click Distribution Point in the roles, select Properties
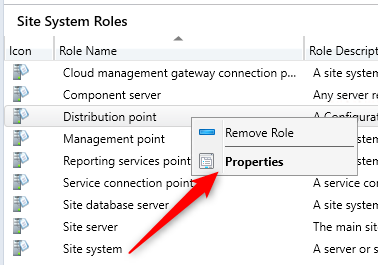
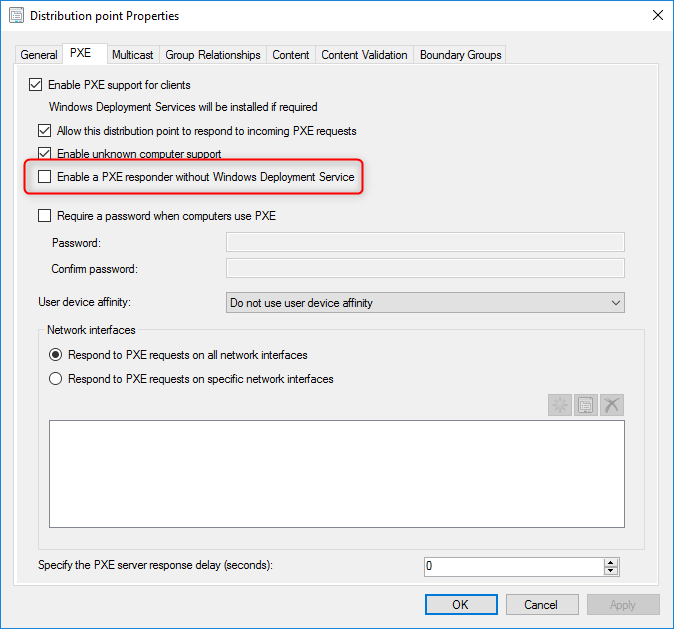
- In the PXE tab, select Enable a PXE responder without Windows Deployment Service
- Select Yes
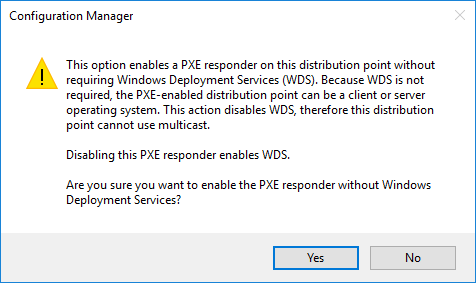
- Click Apply and Ok to close the Distribution Point Properties
Before :
- WDS RemoteInstall folder
- Windows Deployment Services Server running
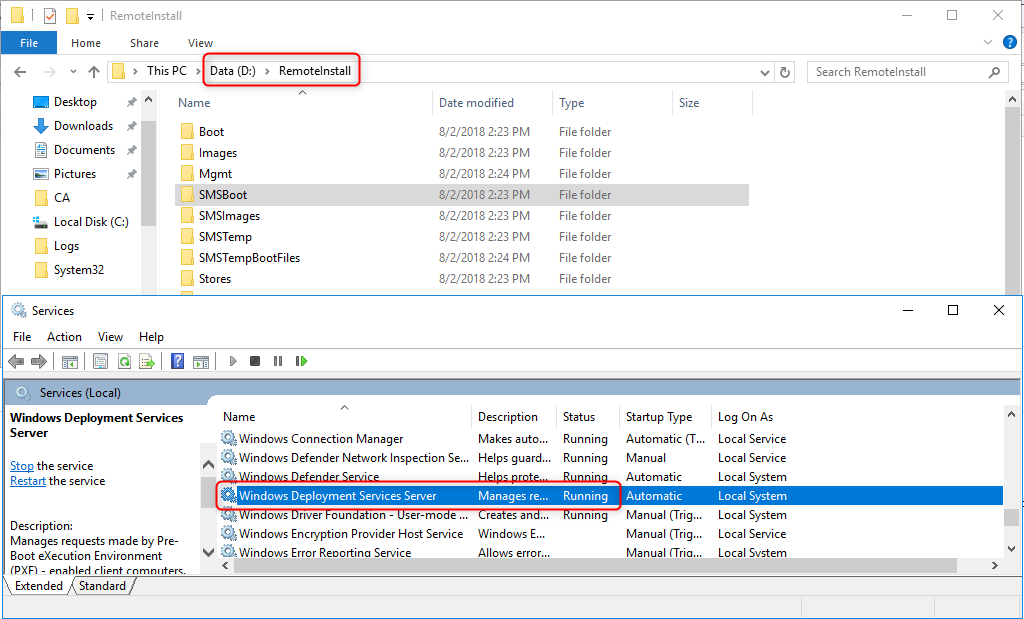
After :
- After a couple of minutes, the WDS Service will stop
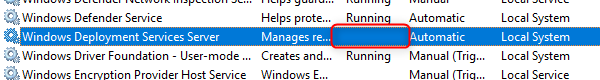
- The new ConfigMgr PXE Responder Service is created
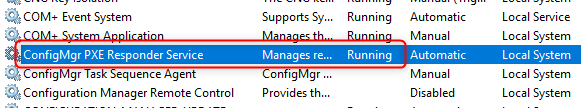
The existing distribution point is now ready to respond to request without WDS ! For more verification steps, jump to the Verification section of this post.
New Windows 10 Distribution Point
We will now add the PXE Service on a new Windows 10 DP which is the real value of this option.
Like any other distribution point installation, the prerequisites are the same. Review our post to know what are the requirement before continuing reading this post. (On Windows 10, adding the computer account as Administrator and open needed Firewall port should be enough).
- In the SCCM Console
- Go to Administration \ Site Configuration \ Servers and Site System Roles
- Right-click Servers and Site System Roles and select Create Site System Server
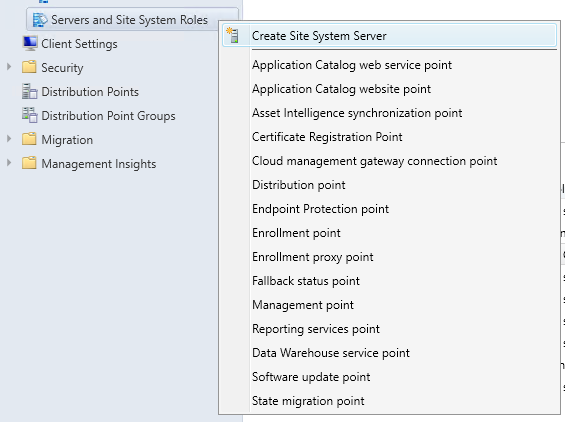
- On the General Pane, enter the FQDN of your site server, click Next
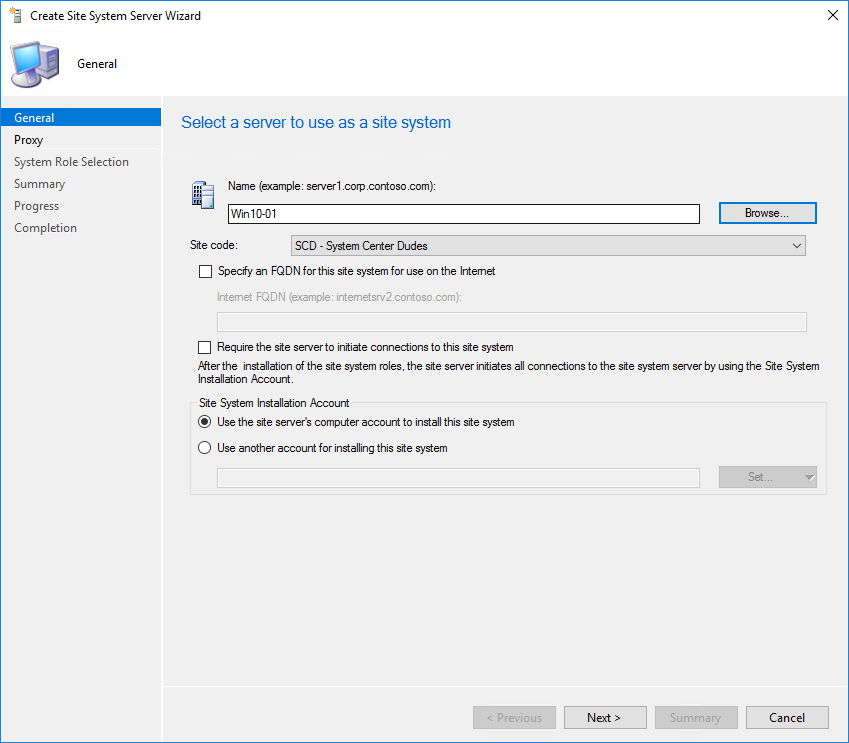
- On the Proxy pane, click Next
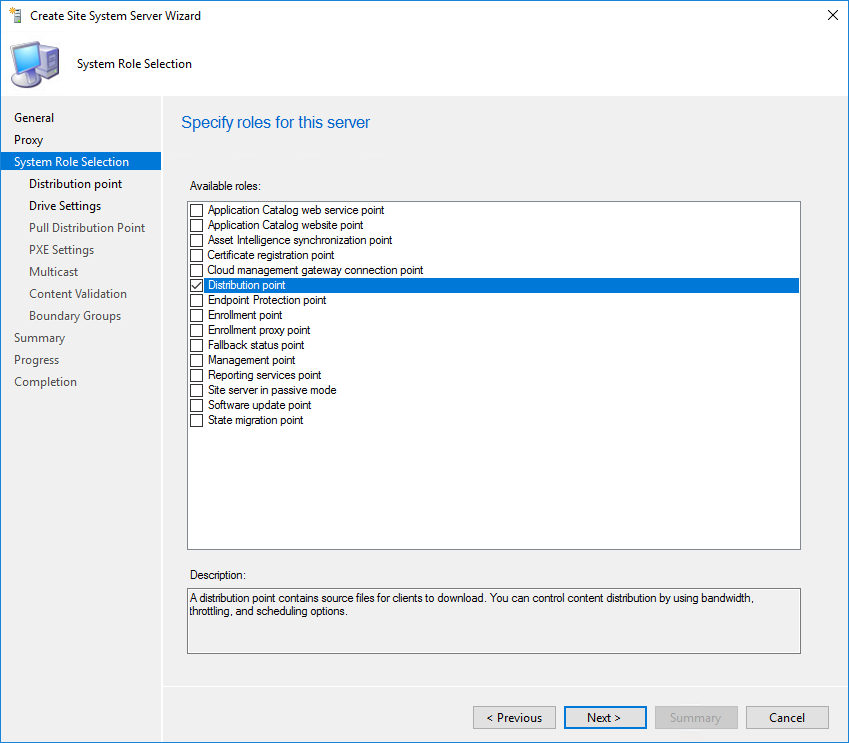
- On the Role Selection, select Distribution Point
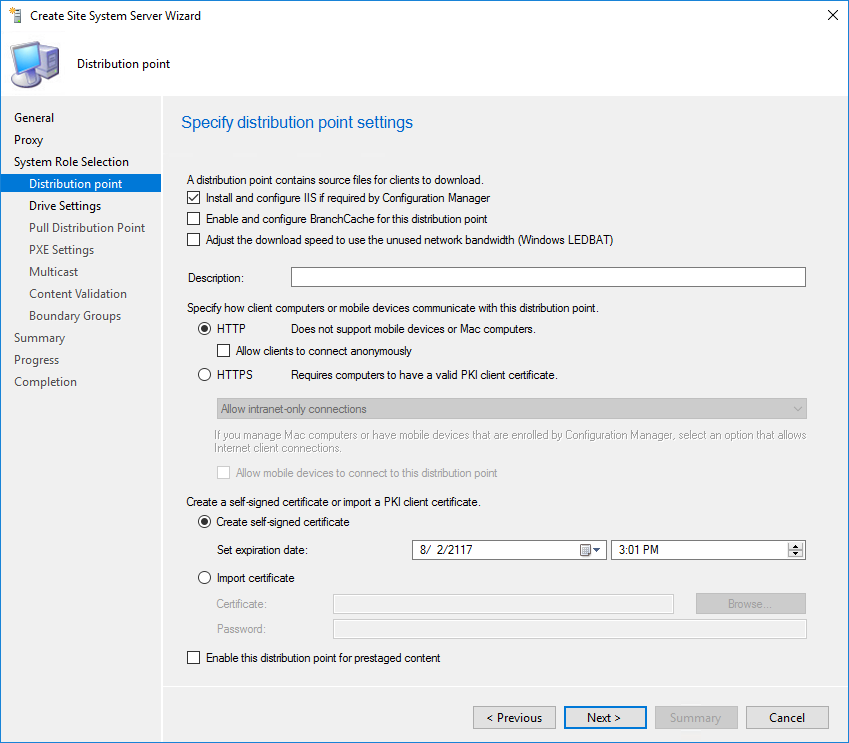
- In Distribution Point, select Install and Configure IIS and keep all other options default
- Enter the desired drive settings
- Do not enable the Pull Distribution Point option
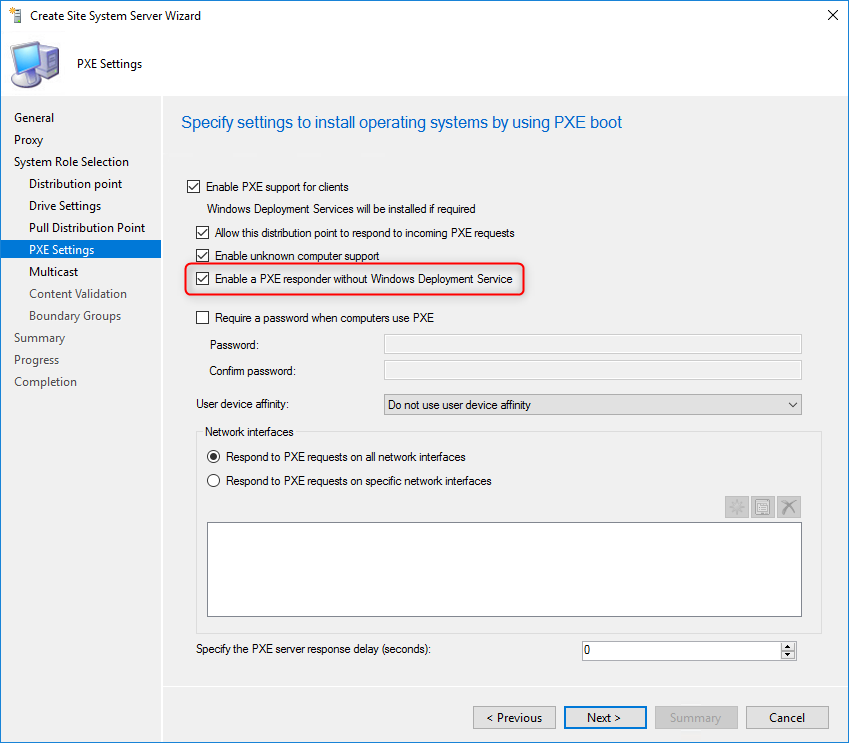
- In the PXE Settings pane, this is where the magic happens
- All four checkboxes, the important one is Enable a PXE responder without Windows Deployment Service
- If desired you can require a password
- The Multicast options are greyed out since it’s not supported on a client OS as stated in our introduction
- Enable Content Validation, click Next
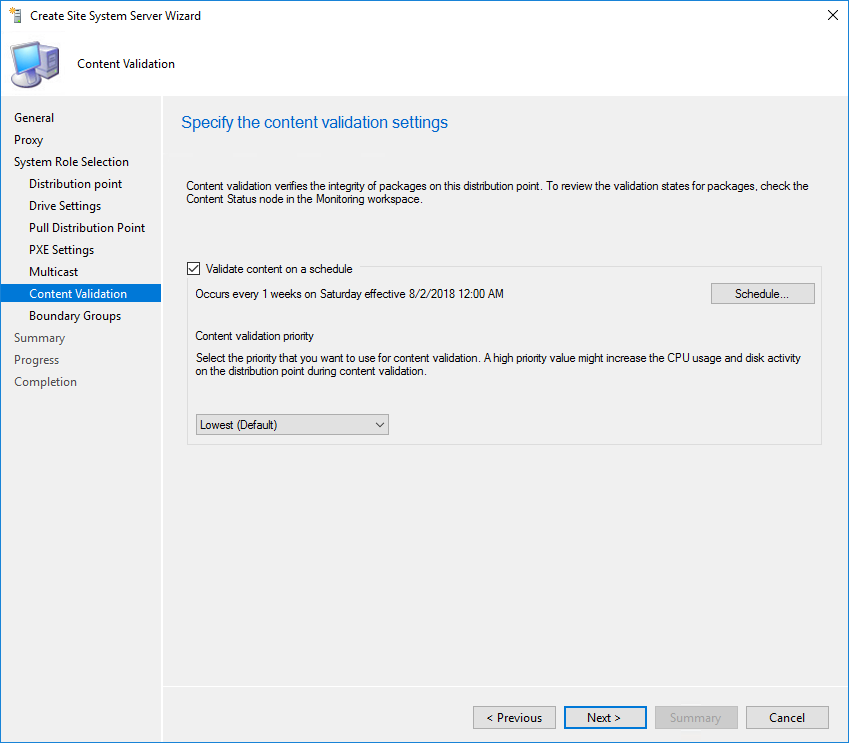
- Add the desired boundary group, usually, you’ll add the boundary group of your remote site
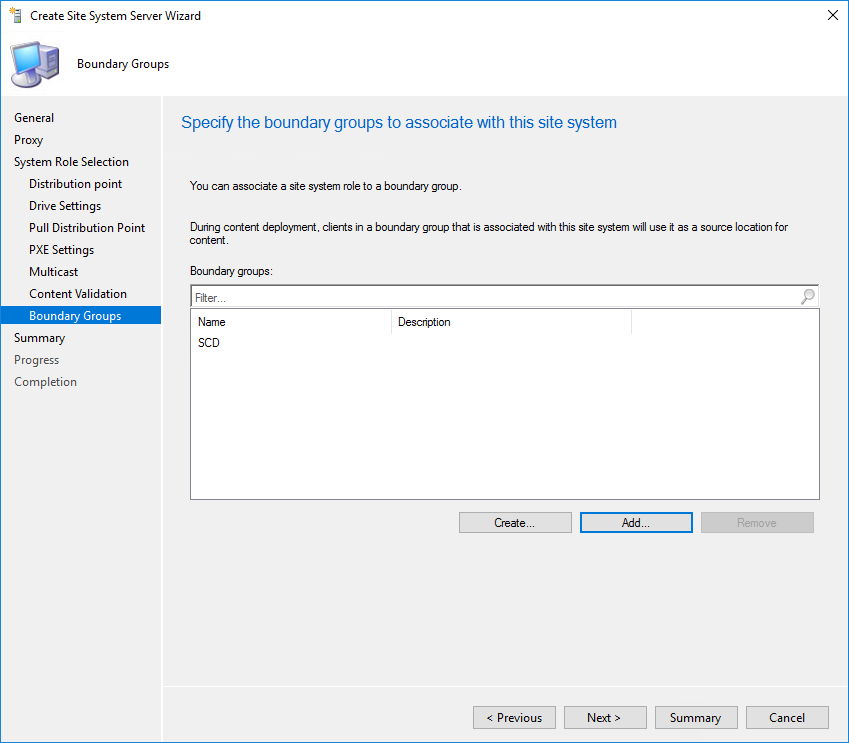
- Review your options and complete the wizard
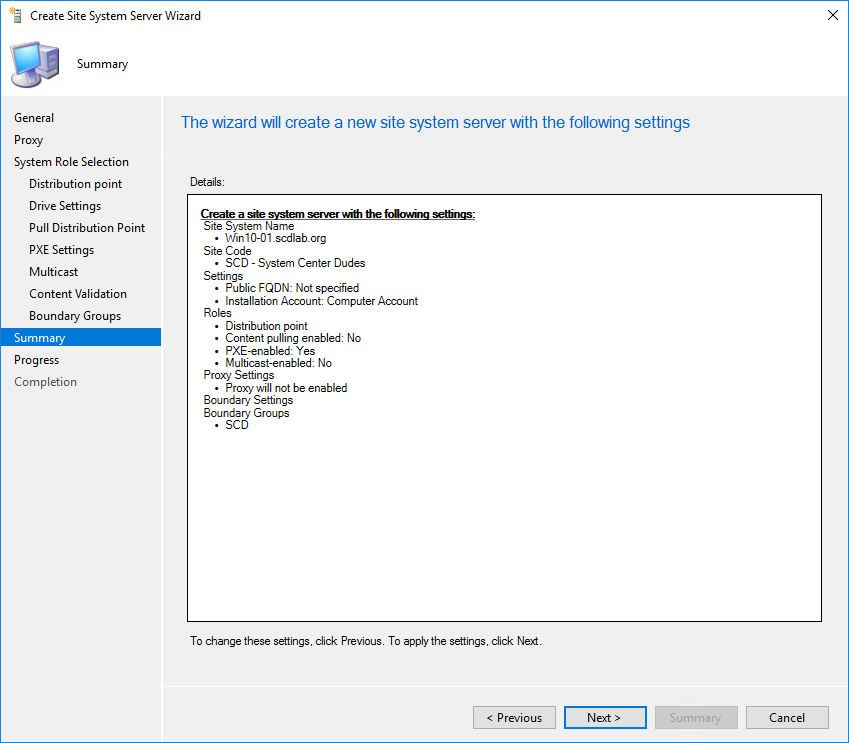
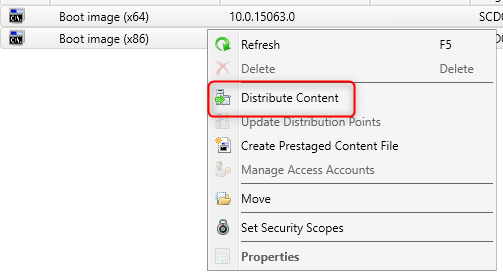
Distribute your boot Image and Content
The last step you need to do is to distribute the Boot Image and needed content for you Task Sequence to run on the Distribution Point.
- Go to Software Library \ Operating Systems \ Boot Images
- Right-click your Boot Image and select Distribute Content
- Select the newly created Distribution Point from your DP List.
Verification
Let see what happen under the hood on our Distribution Point.
- In the SCCM Console
- In Monitoring \ Distribution Status \ Distribution Point Configuration Status
- We can see that our Windows 10 Distribution Point is enabled for PXE
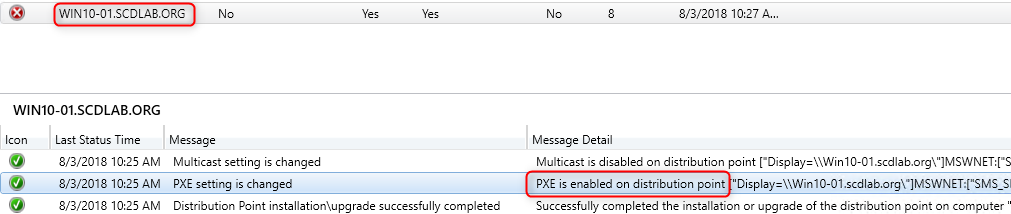
- On the Primary Site Server, log to check is Distmgr.log which will show detail about our Distribution Point Installation with PXE
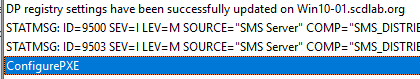
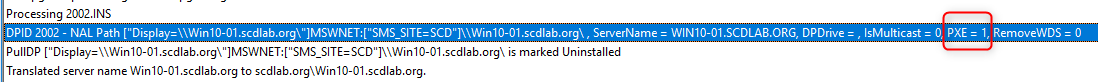
- Locally on the Distribution Point the SMSPXE.log is created and mentioned also that SCCM PXE is enabled
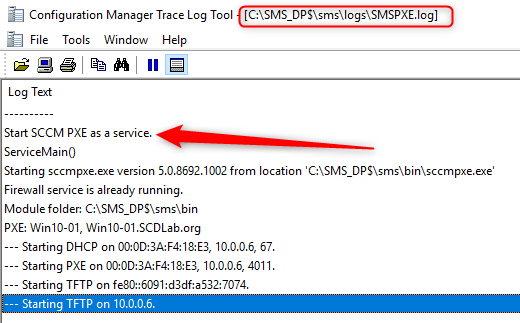
- In the Services window, the new ConfigMgr PXE Responder Service is created and running

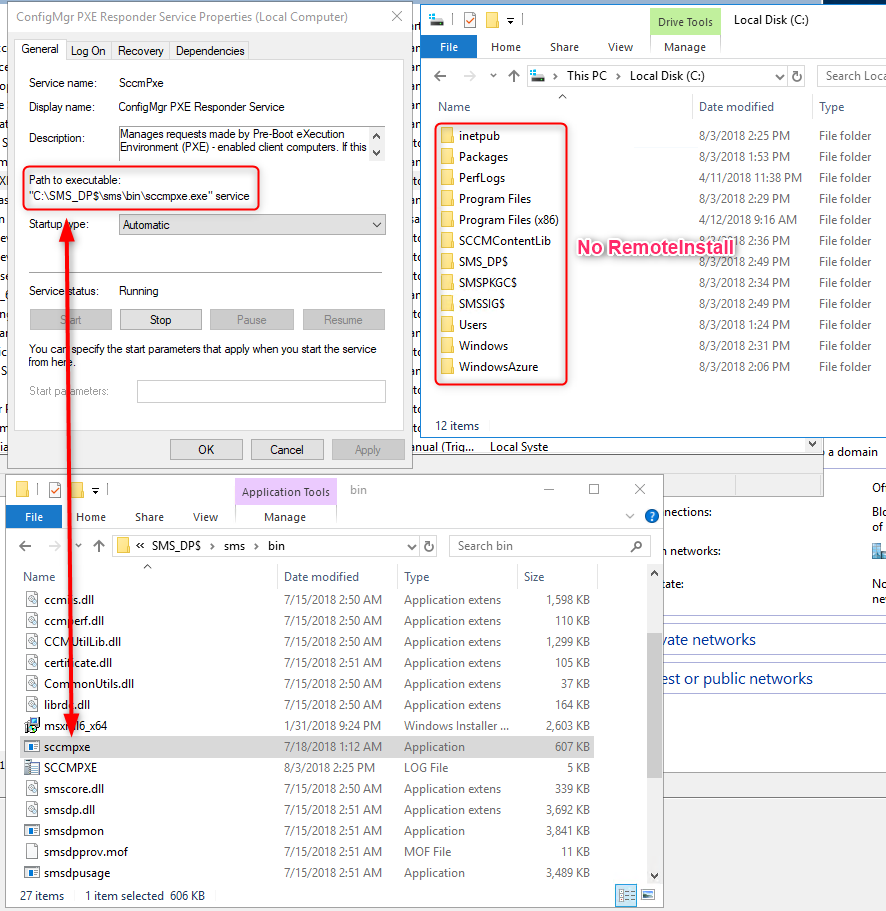
- A new executable is now responsible to respond to Pxe request – SCCMPxe.exe and there’s no RemoteInstall folder. In case you are wondering, the Boot Images and content are in the SCCMContentLib folder
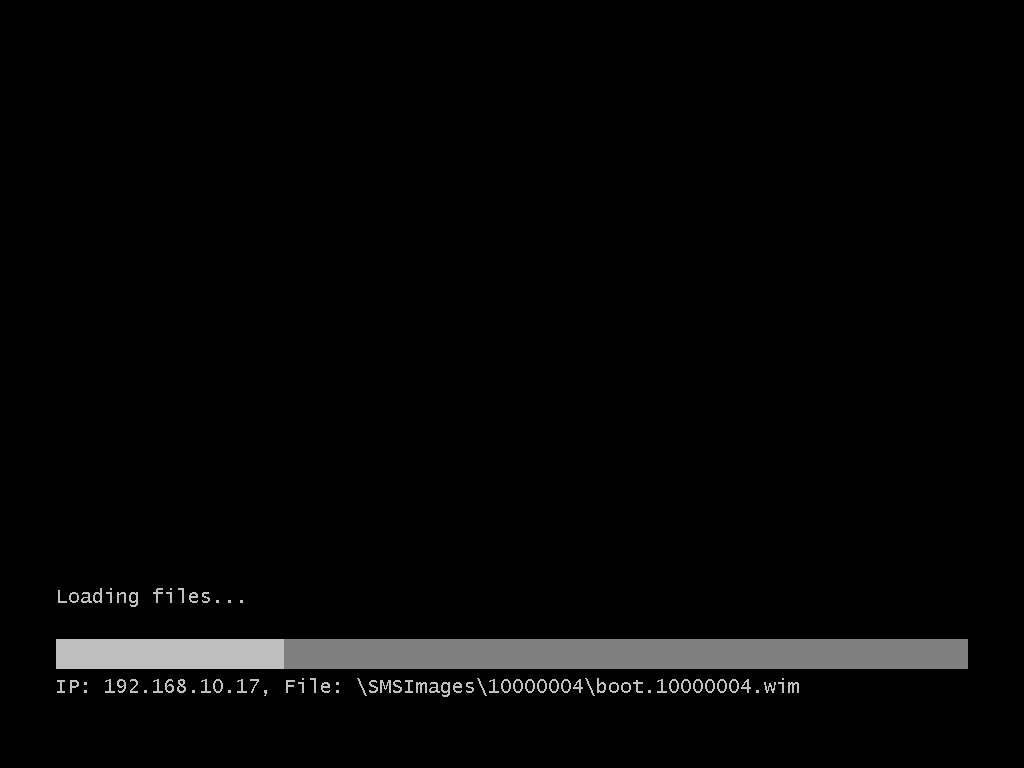
Now lets PXE boot a computer :
- Booting….

- Downloading…
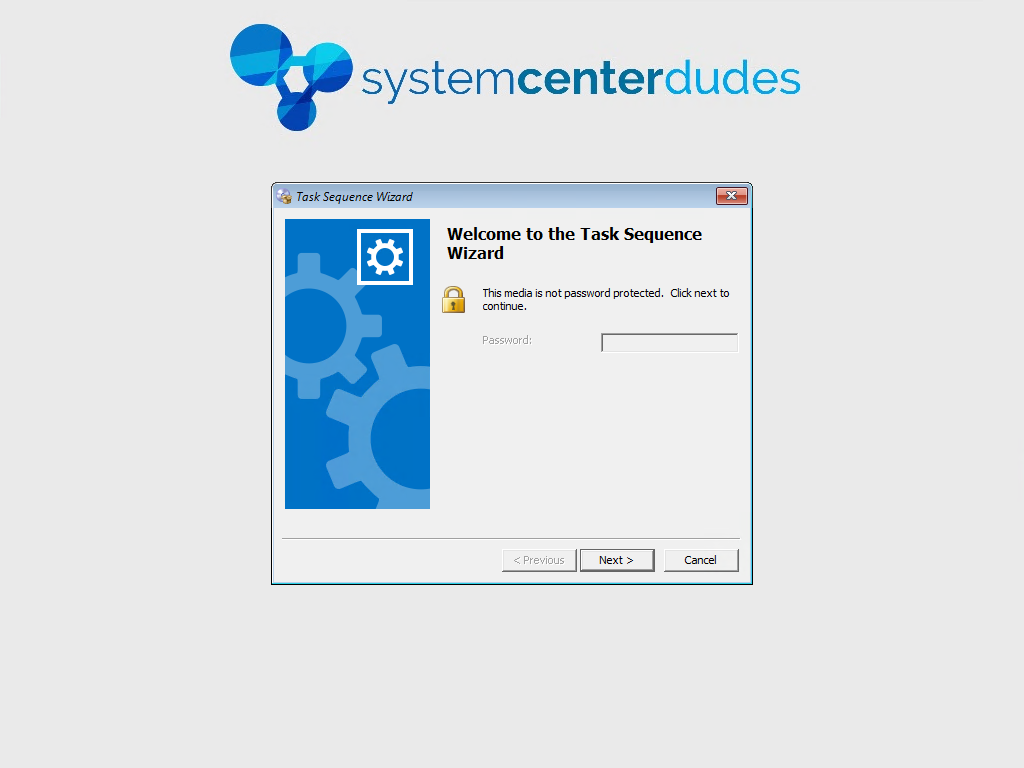
- Bingo !
- The PXE request log will be locally on the Distribution. In our case C:\SMS_DP$\bin\sms\Smspxe.log
- Keep also in mind that iphelpers/dhcp boot option (hint: use iphelpers not boot option!) are still required if you need to redirect traffic from other subnets.
This feature alone is a good reason to upgrade to SCCM 1806 as soon as possible. Great work to Kerwin and his team!
[ratings]













Andre
08.15.2019 AT 01:54 AMTom Baumann
05.28.2019 AT 02:10 PMZbrand
05.17.2019 AT 12:18 PMLouis
03.22.2019 AT 02:58 PMMichael Zucker
03.12.2019 AT 12:46 PMMichael Zucker
03.05.2019 AT 10:51 AMGert
02.28.2019 AT 06:13 AMTimothy
08.19.2019 AT 06:01 AMLeen Wouters
02.21.2019 AT 05:39 AMLeen Wouters
02.21.2019 AT 05:37 AMPaweł
01.29.2019 AT 10:36 AMTrowa B.
01.29.2019 AT 08:47 AMBenilde Benoit
01.21.2019 AT 02:44 AMAzzy
01.03.2019 AT 04:53 AMHOAREAU
11.20.2018 AT 12:17 PMMarek
10.08.2018 AT 10:41 AMMo
09.22.2018 AT 08:56 PMMarc
10.05.2018 AT 07:42 AMMarc
10.05.2018 AT 07:44 AMJonathan Breckel
09.19.2018 AT 03:11 PMPeter Johannsen
09.10.2018 AT 06:20 AMGuillaume Blain
08.16.2018 AT 08:14 AMRom_1
08.15.2018 AT 04:16 AMBasti
09.06.2018 AT 09:39 AM