
First announced at MS Ignite 2022 as Cloud LAPS , the now rebranded Windows LAPS Enables local admin password management for Azure Ad and Hybrid-joined devices to store those passwords in Azure Ad instead of the on-prem AD. This is a big win for remote users that are not connected to the VPN. You can also use Windows LAPS to backup the key to on-prem Active Directory instead of using the GPO, making the old LAPS obsolete. This blog post will only focus on doing the Windows LAPS backup to Azure AD.
For more context on LAPS (Local Administrator Password Solution), this was introduced by Microsoft in May 2015 and does just what the name suggests, allows the management of the password of the Local Administrator Account on workstations, allowing all Windows PCs to have their own unique local admin password by storing it in the computer’s Active Directory object. The password is then retrieved with a LAPS client by someone who has the proper permissions in AD.
Pre-requisites for Windows LAPS Azure AD
- You will need an Intune license.
- Your computers need to be on Windows 10/11 with the April 2023 CU installed.
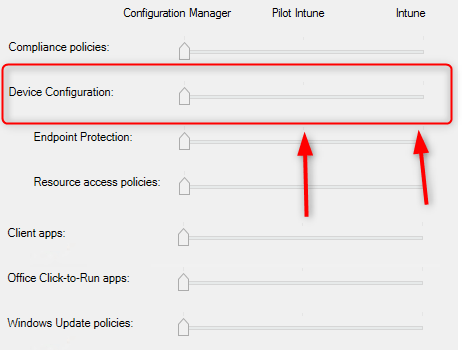
- For Co-managed devices, make sure the Device Configuration slider in SCCM’s Co-Management settings is set to Intune or Pilot Intune for the devices on which you want to deploy Windows LAPS
How to implement Windows LAPS
The first step is to enable the functionality in your Azure tenant. For that:
- Go to portal.azure.com and open the Azure AD app.
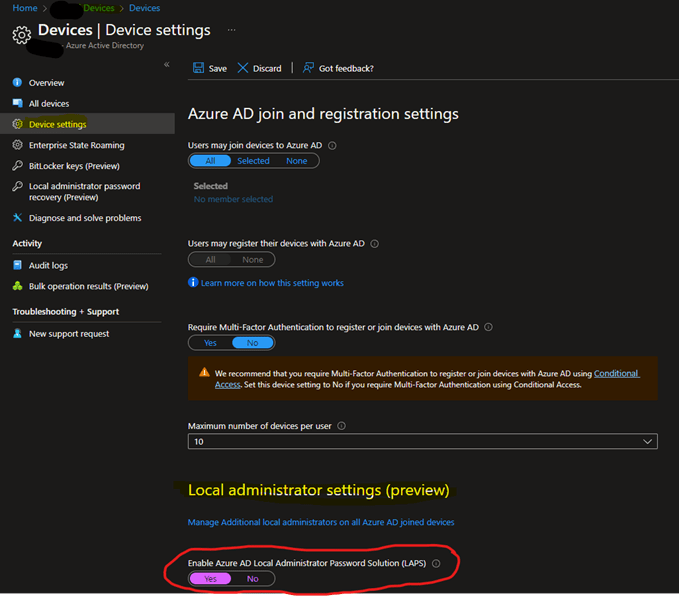
- Click on Devices, then Device settings
- Near the bottom of the page, make sure to Enable Azure AD LAPS:

- Don’t forget to click Save at the top to apply the setting.
Once this is done, you can then go to the Intune portal to configure the policy that will be applied to managed devices.
- From the Intune portal, go to Endpoint Security, then Account Protection.
- Click on Create Policy, select Windows 10 and later platform, then Windows LAPS profile
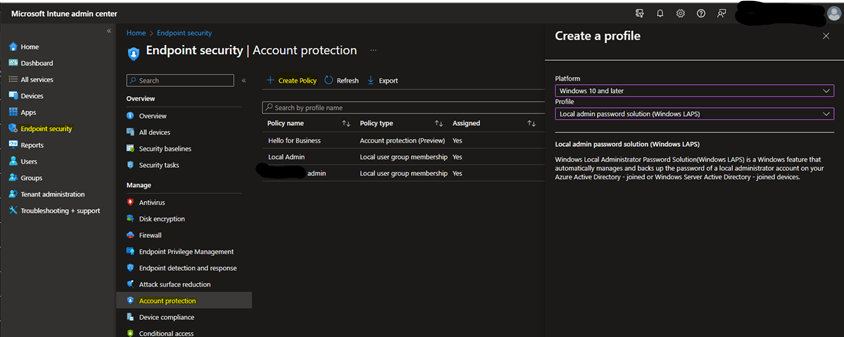
- Name your profile according to your naming convention and click Next.
Here is a breakdown of the different settings to configure in the policy:
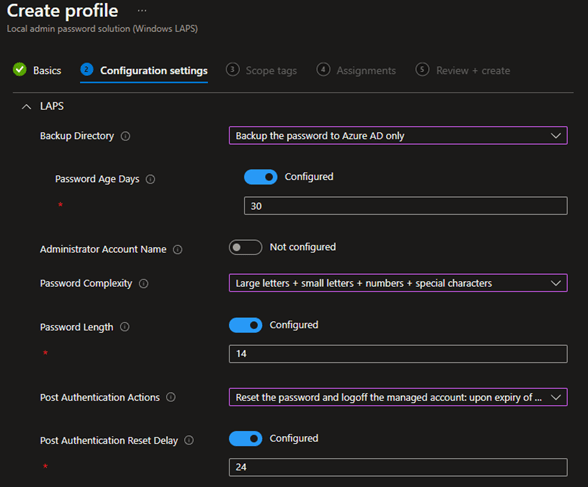
- Backup Directory: we will be using “Backup the password to Azure AD only”. If not configured, the default will be “Disabled”.
- Password age days: This will determine the delay before the password is refreshed to a new one. If you don’t configure that setting, the default is 30 days. You can adjust that to suit your needs, but here we’ll leave the default value.
- Administrator Account Name: This will allow you to manage the password of an account other than the built-in administrator account. If you are using the Built-in account, whether it was renamed or not, you do not need to configure this setting.
- Important note: If you configure Windows LAPS to manage a custom local administrator account, you must ensure that the account is created. Windows LAPS doesn’t create the account.
- Password Complexity: The default if not configured is “Large letters + small letters + numbers + special characters”. If you want password simpler, you can change the setting here.
- Password Length: The default setting if not configured is 14 characters. This setting can be set from 8 to 46 characters.
- Post Authentication Actions: This is used to set the action that will limit the amount of time that a LAPS password may be used before being reset. This prevents someone who acquired a LAPS password to use it indefinitely. The default here is to reset the password and log off the admin account. Here are all the options available explained:
- Reset password: upon expiry of the grace period, the managed account password will be reset.
- Reset the password and logoff the managed account: upon expiry of the grace period, the managed account password will be reset and any interactive logon sessions using the managed account will be terminated. (Default behavior)
- Reset the password and reboot: upon expiry of the grace period, the managed account password will be reset, and the managed device will be immediately rebooted.
- Post Authentication Reset Delay: Sets the delay in hours before the previous actions above is executed. The default is 24 hours.
Here is an example policy using the defaults, which for most environments will be perfectly suited.
From here, assign relevant scopes and deploy the rule to the Azure Ad group you want to manage with this policy.
Migrating from Legacy LAPS to Windows LAPS
If you previously had the now Legacy LAPS configured in your environment, you will need to uninstall the client from the computers for Windows LAPS to take over, otherwise the two will conflict and none of the 2 LAPS will work. This is a known issue since April’s CU and Microsoft is looking to address that in the future.
Regardless of this issue, you should remove the old LAPS GPO and MSI Client from computers that have new Windows LAPS policy applied.
To remove the MSI Client from computers, we cannot use a single MSI GUID as it changed every time Microsoft updated the MSI. Instead, you should use your existing package and run the uninstall on that MSI.
Note that existing password in legacy LAPS cannot be migrated to Azure Ad. There may be a transition period where the admins/techs will need to keep the old LAPS management client to fetch the legacy passwords until Windows LAPS kicks in and all passwords are uploaded to Azure Ad.
There is a pretty good conversation about this topic on a Reddit post if you want to dig further into this.
Retrieving the Windows LAPS password from Azure AD
There are 2 ways of retrieving the LAPS password. Same as BitLocker keys, you can either get it from Azure or Intune.
Azure: find your device in Azure Ad and click on it, then to the left click on “Local administrator password recovery”, then “Show local administrator password”, and Show to the right.
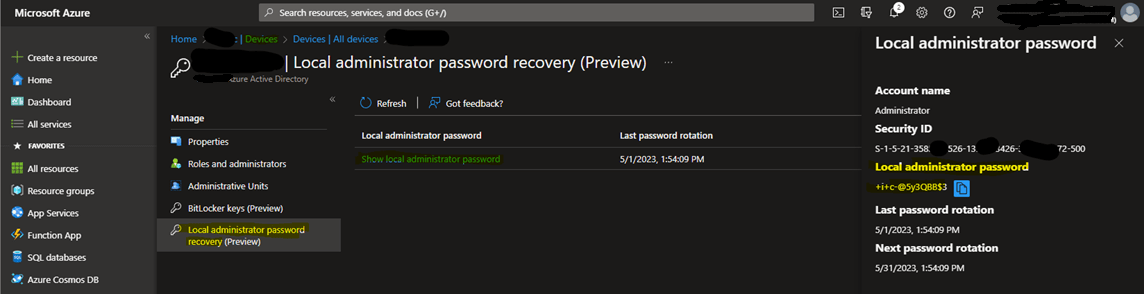
Intune: find your device in Intune and click on it, then to the left click on “Local admin password”, then “Show local administrator password”, and Show to the right.
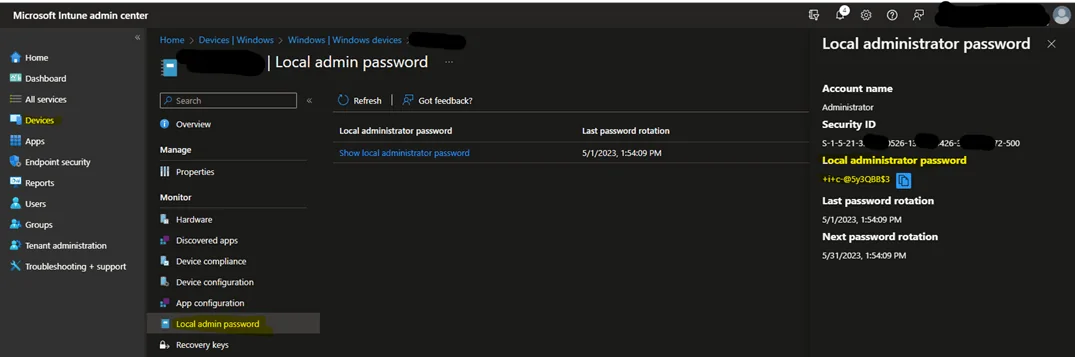
Congratulations, you’ve setup Windows LAPS with Azure AD!













Only authorized users can leave comments
Log In