

Recently, I have encountered a situation in an environment where a user was prompted with the BitLocker recovery screen on their Intune-managed Windows device. There could be several reasons that trigger BitLocker recovery.
In normal circumstances, when BitLocker policy is applied and enabled via Microsoft Intune, the recovery key is automatically backed up to Azure AD / Entra ID as part of the policy. However, in this case, when the user accessed the self-service portal, such as company portal or https://myaccount.microsoft.com/ for BitLocker recovery, there was no recovery key found for the Intune managed device.
This created an issue for the user to access the computer, especially since the device was encrypted and the user couldn’t proceed past the recovery screen. The lack of a recovery key in Azure AD not only affected user productivity but raised important questions about device compliance and data recovery readiness across the fleet.
Intune BitLocker Recovery Key Missing – Root Cause Analysis
Upon further investigation, it was discovered that:
The device was indeed managed by Microsoft Intune, and BitLocker policy was applied.
However, the BitLocker recovery key was never escrowed (saved) to Azure AD /Entra ID.
- The device was also managed by other endpoint tools, such as SCCM / other tools.
Using SCCM scripts, I could run the following PowerShell script to retrieve the recovery key from the device locally and then escrow it to Azure AD/Entra ID.
BackupToAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId ((Get-BitLockerVolume -MountPoint $env:SystemDrive ).KeyProtector | where {$_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorIdWhile this fixed the immediate issue, it raised a broader concern about how many such devices could exist that are missing the BitLocker recovery key and are Intune managed.
️ The Solution: PowerShell to Identify Devices Without Recovery Keys
To address this, there are PowerShell cmdlets that could help to scan all Intune-managed devices and identify those missing a BitLocker recovery key in Azure AD/Entra ID.
The script performs the following:
Connects to Microsoft Graph API using delegated permissions.
Retrieves all Intune-managed devices
Cross-checks for the presence of a BitLocker key (latest date) under the device object in Entra ID.
Outputs a list of devices that are missing recovery keys.
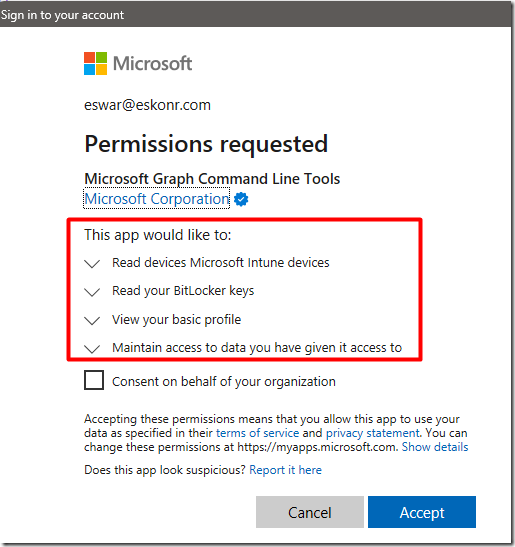
When the script is runs, make sure you grant get the consent to the following permissions for ‘Microsoft Graph Command line Tools’ through Graph Explorer https://developer.microsoft.com/en-us/graph/graph-explorer
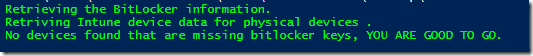
6. If the script cannot find any devices missing Bitlocker recovery keys in Entra ID, the script returns the following output.
Why This Matters
In an environment where BitLocker is enforced via Intune, it’s assumed that recovery keys are automatically stored in Entra ID. However, due to various reasons, some of the devices could be missing their recovery keys hence, it is always important to validate and take action on missing devices.
Download the PowerShell
The script can be downloaded from the Github repository.
Depending on the number of devices managed by Intune, it takes time to complete for all devices. In my case, for about 20K devices, it took almost 30 min or so. so please be patient when the script runs.
At a high level, this PowerShell script does the following:
Checks required PowerShell modules
Verifies and installs
Microsoft.Graph.DeviceManagementandMicrosoft.Graph.Identity.SignInsif missing , install and Imports the modules into the session.
Connects to Microsoft Graph API
Authenticates using delegated permissions:
DeviceManagementManagedDevices.Read.All andBitLockerKey.Read.All
Retrieves BitLocker recovery key data
Gets all BitLocker recovery keys from Microsoft Graph (Entra ID).
Groups them by
DeviceIdand keeps only the latest key per device.
Fetches Intune-managed device list
Filters out:
Devices older than 30 days since last sync.
Devices not managed via Intune (
MDM) or co-managed (configurationManagerClientMdm) Tenant attachedNon-Windows OS.
Devices that are likely virtual machines (e.g., VMware).
Compares devices with recovery keys
Finds devices in Intune without an associated BitLocker recovery key.
Outputs results
How to Remediate – Intune BitLocker Recovery Key Missing
For any device that is missing the BitLocker recovery key (validate one or two devices from the script out), then you can create a remediation script with the following PowerShell command line and apply to the device group (list of devices returned via the PowerShell script)
BackupToAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId ((Get-BitLockerVolume -MountPoint $env:SystemDrive ).KeyProtector | where {$_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorId Related Resources
Microsoft Docs – Back up BitLocker keys to Azure AD
Azure AD BitLocker Recovery Key Portal













Ambi_Indi
01.19.2026 AT 02:10 PM