
As an SCCM administrator, you use the SCCM console to access your primary site. Some of you may use the console locally on the SCCM server and some use the console on remote machines. Recently a customer ask for help because of an SCCM Console Access Denied problem. The SCCM console was working fine before and it was also working on another machine with the same user. I eventually found the solution and decided to document the whole troubleshooting process to fix SCCM Console Access Denied in this blog post.
Step 1 – Troubleshooting on affected machine
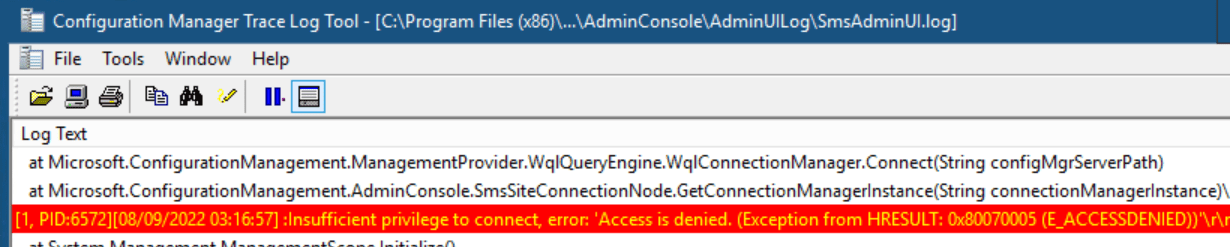
For any remote console troubleshooting issues, start with reading the SmsAdminUI.log file located on the client.
- This log file is located: C:\Program Files (x86)\Microsoft Endpoint Manager\AdminConsole\ AdminUILog
In my example, you can see the error: Insufficient privilege to connect, error: Access is Denied. (Exception from HRRESULT: 0x80070005 (E_ACCESSDENIED))

Step 2- Understand the needed permission
The first thing you need to know is that a remote SCCM console requires 2 things :
- Remote Activation DCOM permissions on:
- The site server computer
- Each computer that hosts an instance of the SMS provider
The SMS Admins group grants access to the SMS provider on a computer, and can also be used to give access to DCOM. This is a local group on the computer where SMS provider is installed.
The SCCM console uses WMI to connect to the SMS provider, and WMI internally uses DCOM. If the SCCM console runs on a computer other than the SMS provider computer, it requires permission to activate a DCOM server on the SMS provider computer. By default, Remote Activation is granted only to the members of the built-in Administrators group.
- Besides DCOM permission, the user using the SCCM console must have the right to access SCCM.
Step 3 – Verify SCCM permission
Since my user has access to the console on another machine, this is clearly not my issue here but I double-check to be sure.
- In the SCCM console go to Administration \ Security \ Administrative Users
- Check that the affected user is a member of a security role that grants access to the server
- My user is a member of the Full Administrator group and should have access to the SCCM console
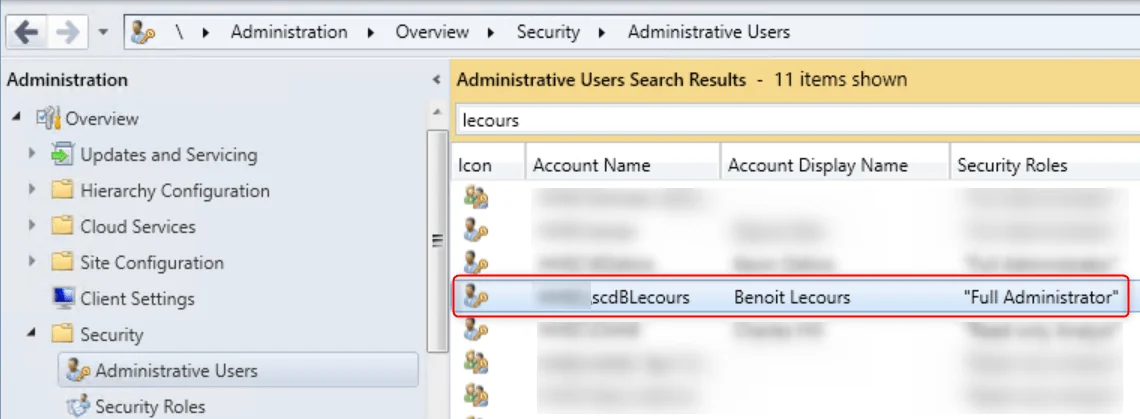
Step 4 – Verify DCOM permission
The second step was to verify the DCOM permission on the SCCM server :
- From a Run command, type Dcomcnfg
- Go to My Computer and Properties
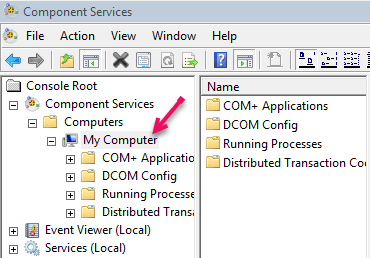
- Ensure that Enable Distributed COM on this computer is checked in the Default properties pane
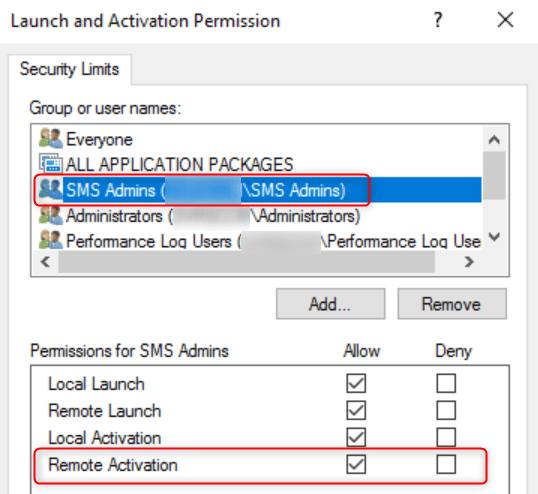
- In the COM Security tab, click Edit Limit under the Launch and Activation Permissions section
- In the Launch and Activation Permissions window, ensure that the SMS Admins group is listed
- In the Permissions for SMS Admins section, ensure that the Allow column for the Remote Activation row is checked
SCCM Console Access Denied – Other possibilities
In my case, SCCM permission and DCOM permission were fine. Some solutions found on other blog posts were pointing to reinstalling the MSDCT service on the SCCM server and rebooting the server.
- Run MSDTC –uninstall
- Run MSDTC –Install
- Reboot
It didn’t fix the issue… so I’ve checked any other external causes:
- Firewall port needed for the console
- Anti-Virus exclusion
Still not working. What could make a machine connect and not another using the same user to connect?
So I started to compare machines and found differences in Windows patches.
KB5004442 – Manage changes for Windows DCOM Server Security Feature Bypass
I started to read about this KB5004442 patch that changes the default behavior of DCOM communication.
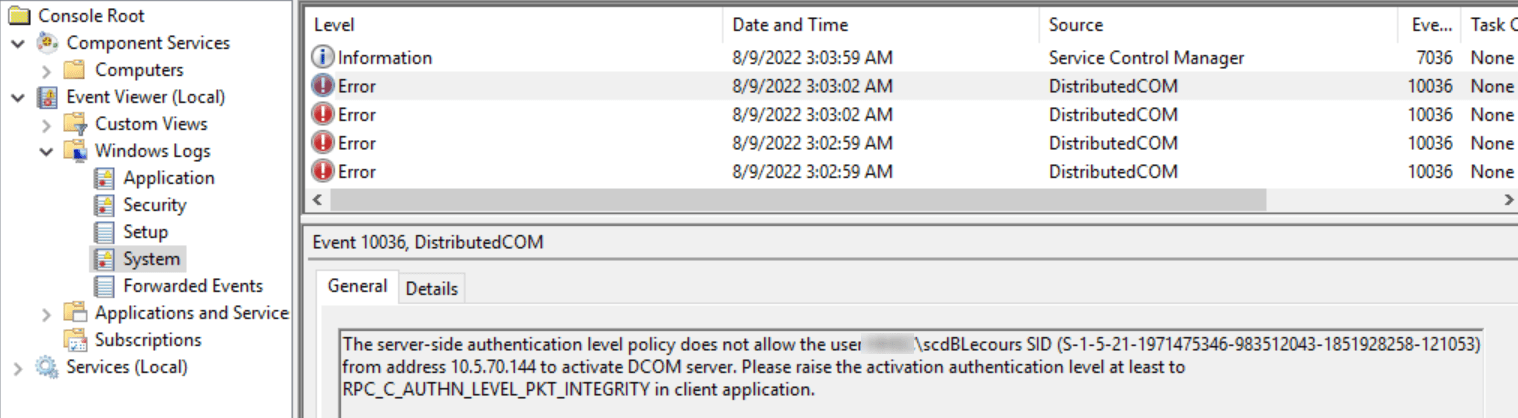
As stated in the article, my SCCM server was registering a new 10036 event in the Event viewer. The error clearly points in this direction.
The server-side authentication level policy does not allow the user from address to activate DCOM server. Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application.
Finally, I got some hope to resolve it.
So I’ve checked on the machine that refuses to connect and the patch is not installed and it’s installed on the SCCM Server. The DCOM hardening is enabled per default on the server and disabled on the client which causes the error.
The registry key method is only a workaround. Patching the affected server and client before March 14, 2023, is the best solution. After this date, Hardening changes will be enabled by default with no ability to disable them.
So I decided to try the proposed workaround and disable the Hardening changes on both the Server and client.
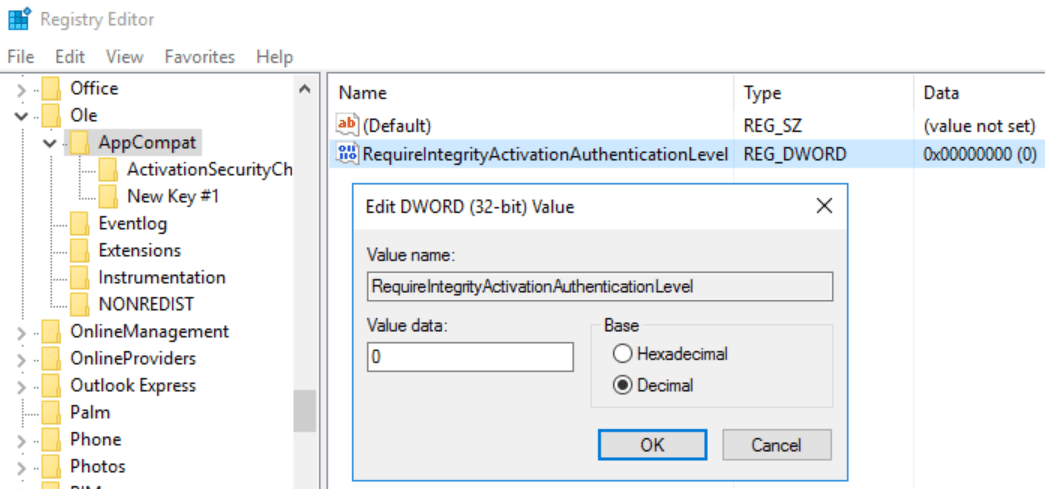
- In the registry editor, go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\AppCompat
- Create a new DWORD Value : RequireIntegrityActivationAuthenticationLevel
- Value : 0
- Reboot both machines
After the reboot, my SCCM Console was working fine and all SCCM Console Access Denied errors were gone.











Only authorized users can leave comments
Log In