
Top 5 Security Features in Intune
By 2019, when you plan to deploy modern device management solutions in your company, security must be a priority. The cloud is accessible from anywhere, and mobility allows users to connect from anywhere. Also, our society is changing, and our lifestyle habits are as well. Users who have access to corporate data without being forced to connect to the corporate network are much more convenient.
Before registering devices in Microsoft Intune, setting up the Intune portal safely is essential. Moreover, the different operating system platforms and the types of devices that connect to your network or cloud applications are also important.
Microsoft Intune is a leader in MDM solutions, and it contains strong security capabilities you can’t miss, like role-based administrative control (RBAC), enrollment restrictions, compliance policy and a couple more.
On several occasions, we have noticed that companies do not use proper security features with Microsoft 365. Are you planning to use Microsoft Intune in the future, or do you already use it?
Some settings are pretty easy to configure; others will require a little testing to ensure it doesn’t negatively affect productivity. We highly recommend that you take the time to evaluate those settings.
In this post, I will explain my top 5 no-brainer features in Microsoft Intune that must be configured in your organization.
1. Administrative Roles (RBAC)
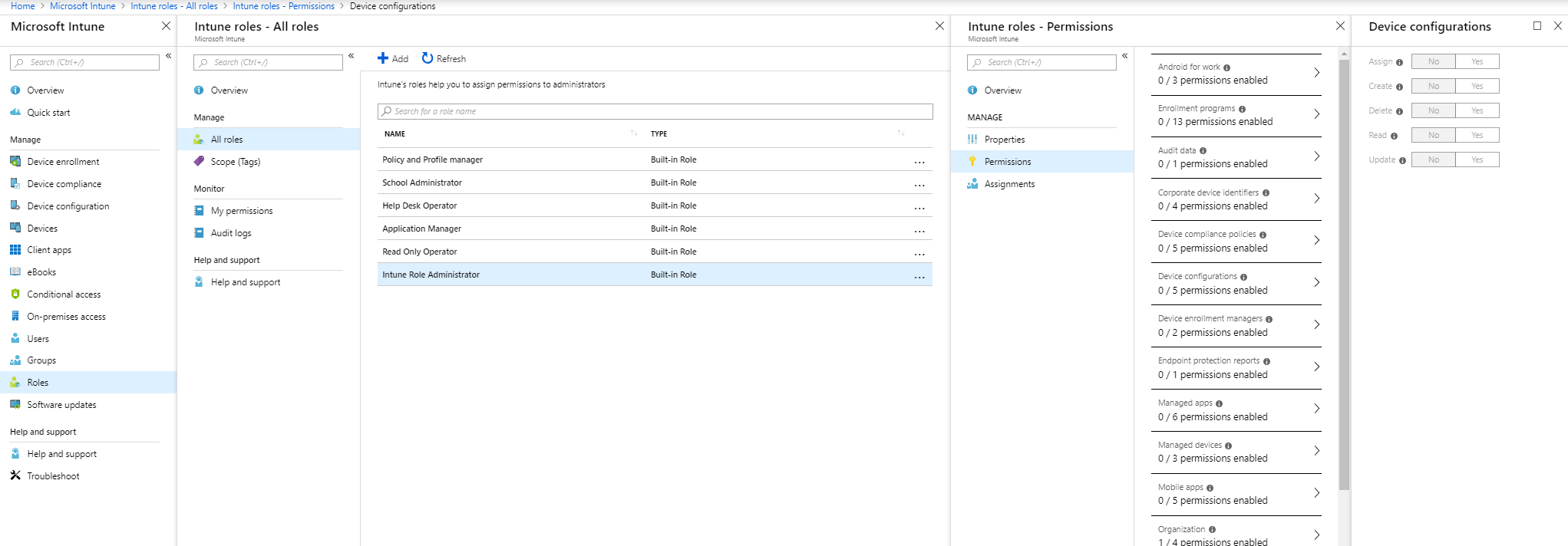
First, you must secure the Intune admin portal so that no unwanted users manage your service or modify your settings without realizing it. Role-based administration control (RBAC) in Intune helps you control who can or can’t perform various tasks. Thus, it’s not a new concept for SCCM admins. RBAC has been in SCCM for a long time.
If you’re the only employee who manages Intune in your company, it’s okay to be an Intune administrator in your team. Also, this administrative role is a directory role in Azure AD.
Meanwhile, separating tasks and roles is normal for some companies with multiple IT departments. The level of knowledge can differ between colleagues, so you can ensure that you assign the proper access to your teammates by creating other admin profiles.
- To create an RBAC role, navigate to https://portal.azure.com and select Intune Blade.
- Go to Roles – All Roles; if you want to create a new custom role, click on Add.
- Select the built-in or custom role and click Assignments to assign a user to a role.
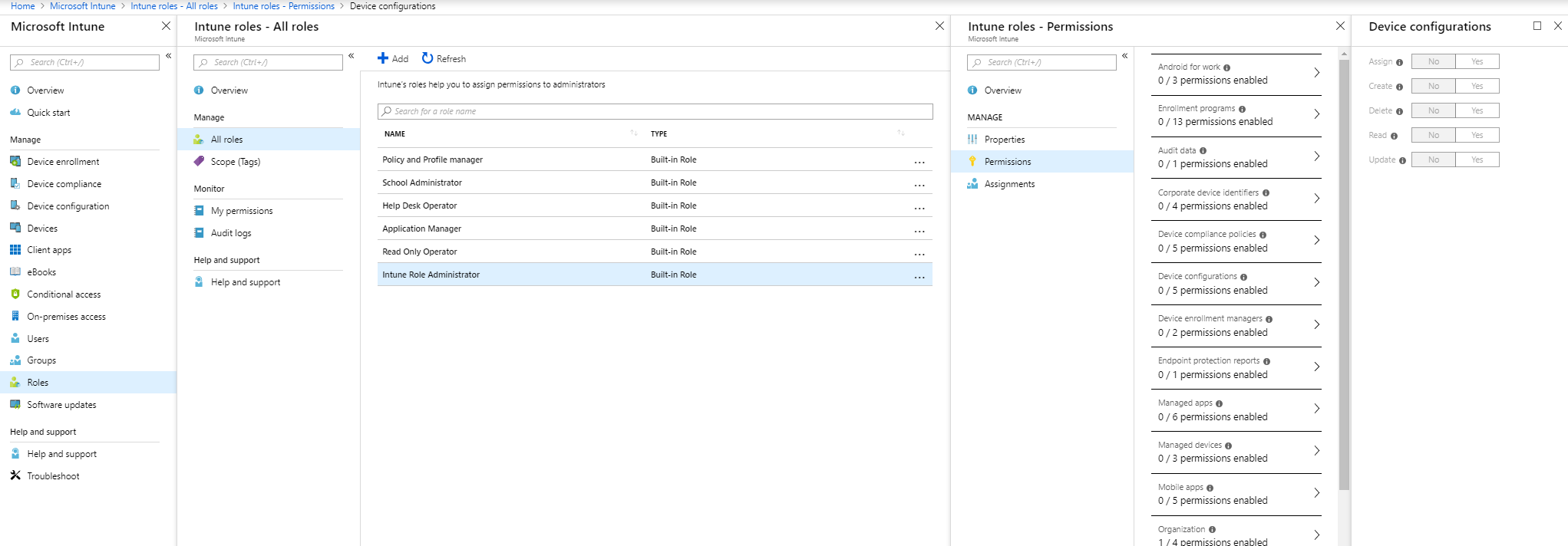
With a Scope or Tags, you can define the visibility of resources assigned to a specific role. Like in this example, you will likely want to use scope or tags for a team that only manages mobile devices or Windows 10.
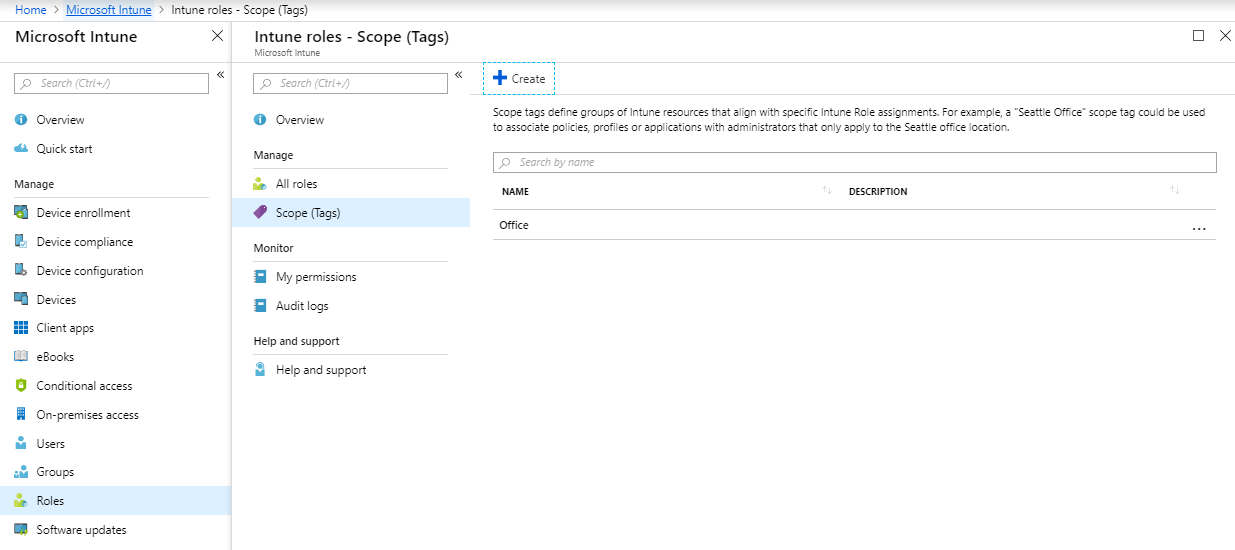
2. Enrollment Restrictions
Secondly, you configure the admin portal, and it’s now time to configure the platforms you want to accept in Intune. Do you want only to accept iOS and company devices in your organization? How many devices can a user enroll devices with the same identity?
You will configure those restrictions in the Enrollment Restrictions blade in Intune.
- In Microsoft Intune, under Device Enrollment, there’s a blade named Enrollment Restrictions.
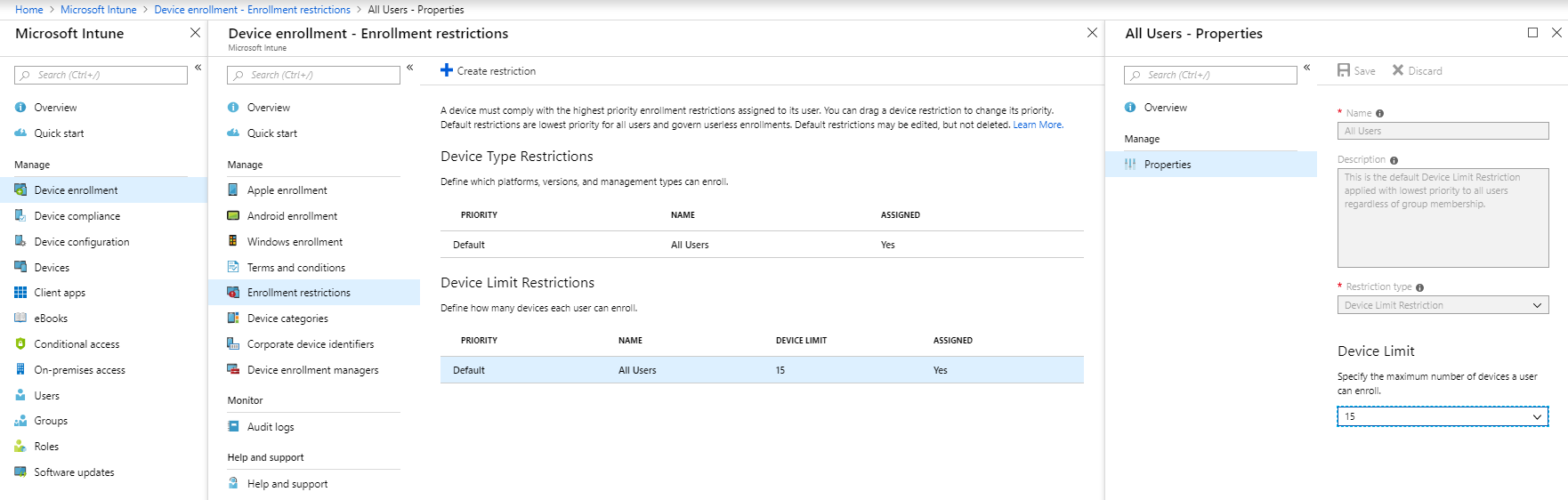
For this purpose, we suggest blocking all the platforms you don’t want to support in your organization to improve the chances of not having unwanted enrollments. Does your company allow employees to enroll in their devices? Block them via Enrollment Restrictions.
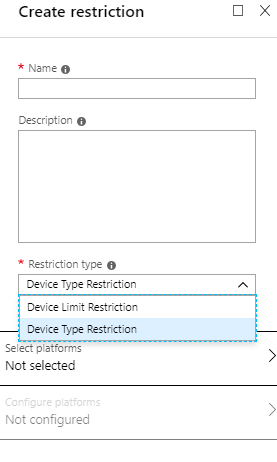
In brief, the limit restriction is the number of devices you accept per user. The number is 15 by default, but you can lower it between 1 and 5 depending on your company device’s reality.
The number of devices has a small impact on security unless you set the limit to 1. There are other security mechanisms such as conditional access and MFA that can block a hacker from enrolling a device.
3. Compliance Policy
Thirdly, let’s talk about compliance policy. This feature defines the rules and settings a user or device must meet to comply. Consequently, the conditional access consumes that compliant state, giving you access to corporate data. What will happen if you don’t configure a compliance policy?
These kinds of devices will be able to connect to your environment:
- Rooted or jailbroken
- Devices with old OS versions
- Devices with a high threat level
- Devices with weak passcode
- Devices with unwanted apps
Accordingly, all enrolled devices in Azure are compliant, even if there’s no assigned policy. Furthermore, the status became more important if you don’t mark devices with no compliance policy assigned as compliant.
- To configure this setting, navigate to Microsoft Intune, Device Compliance and Compliance policy settings.
- Select Not Compliant at Mark devices with no compliance policy assigned as
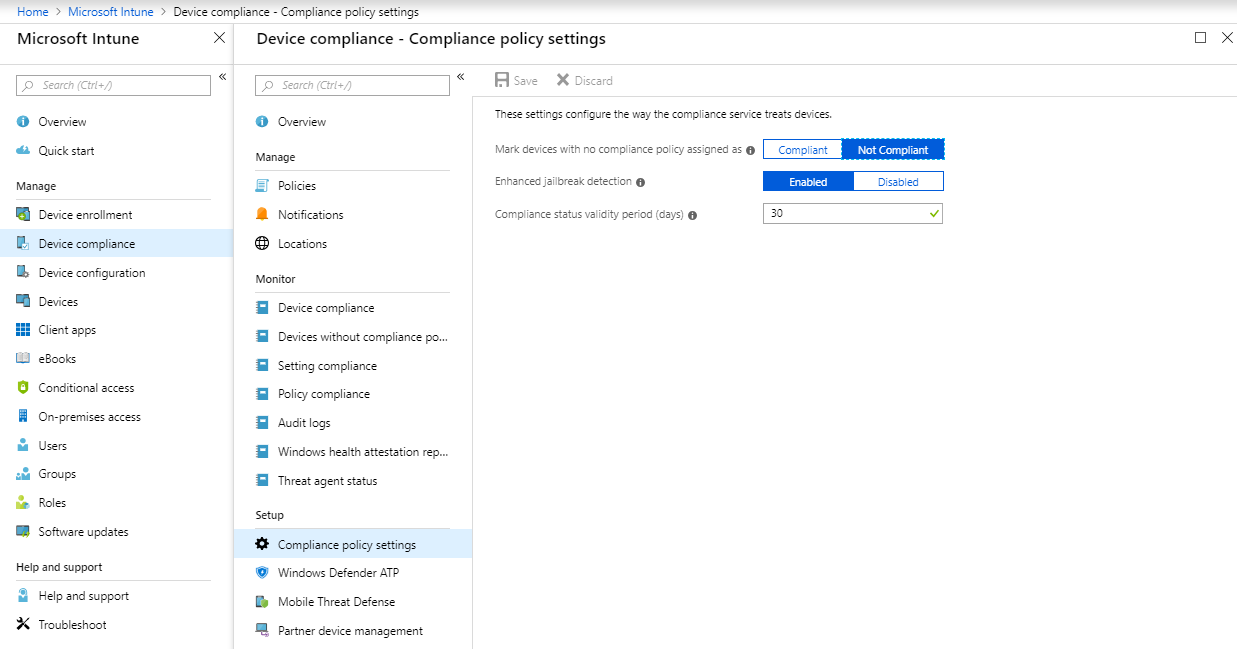
If you leave default setting at Compliant, you enable all devices to access your corporate data from any devices. We highly suggest that you change it to Not Compliant and configure at least a compliance policy.
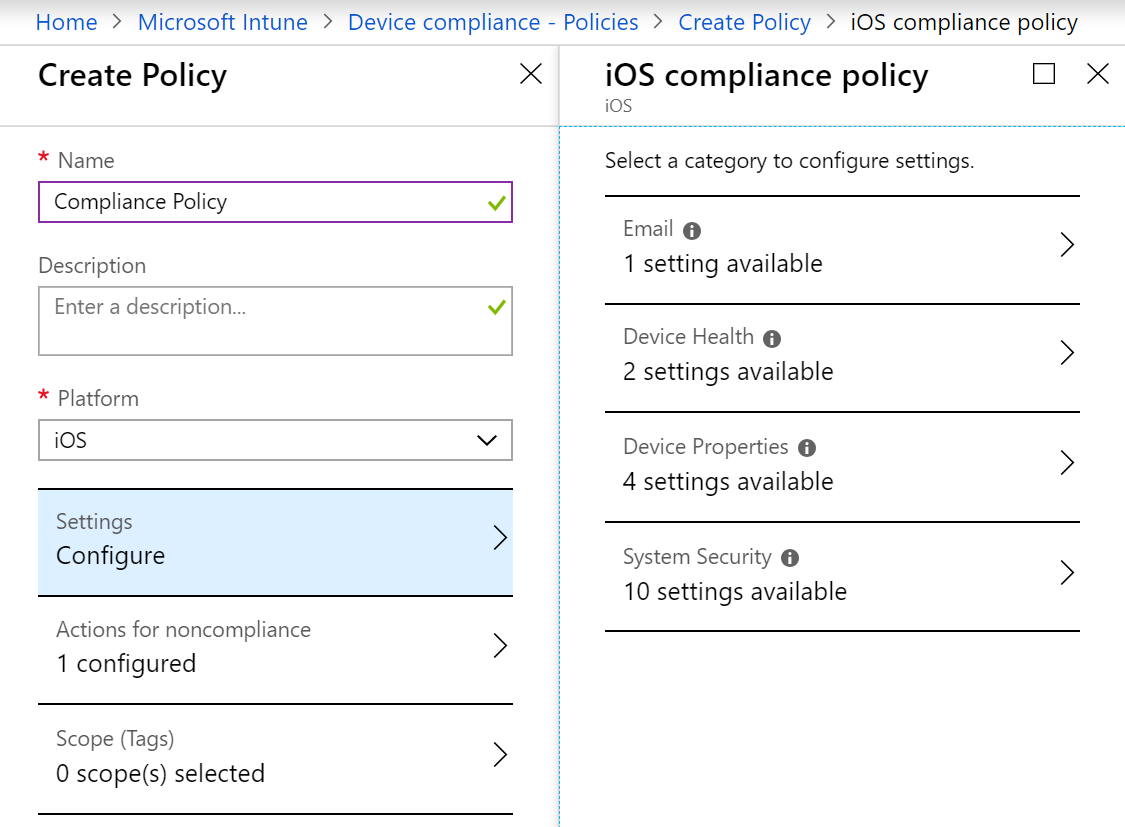
- To create a Compliance Policy, navigate to Microsoft Intune, Device Compliance and Policies.
- Click on Create Policy and configure your policy
- Assign the policy to your users
4. App Protection Policies
After securing the administrative console, enrollment restrictions and compliance, it’s time to protect corporate data on the devices.
Is it acceptable for an employee to transfer a file from One Drive for Business to the DropBox app? Therefore, protecting corporate data is essential, and we suggest you decrease the chance of data leaks within your devices, even if it’s a corporate device.
Mobile Application Management (MAM) is the predecessor of the
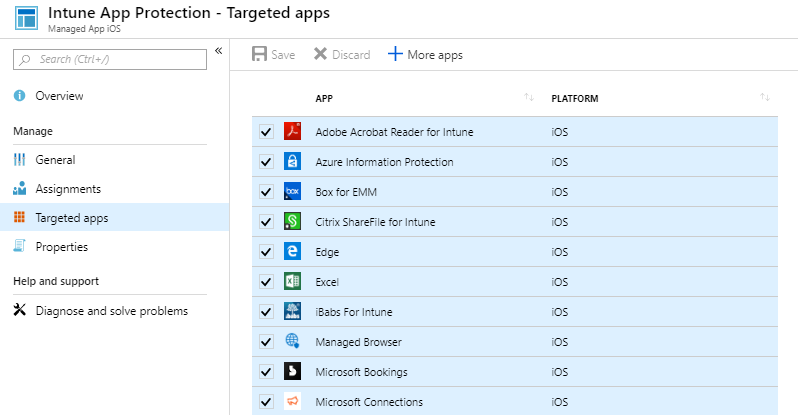
To achieve this goal, create an App Protection Policy by navigating to Microsoft Intune, Client Apps
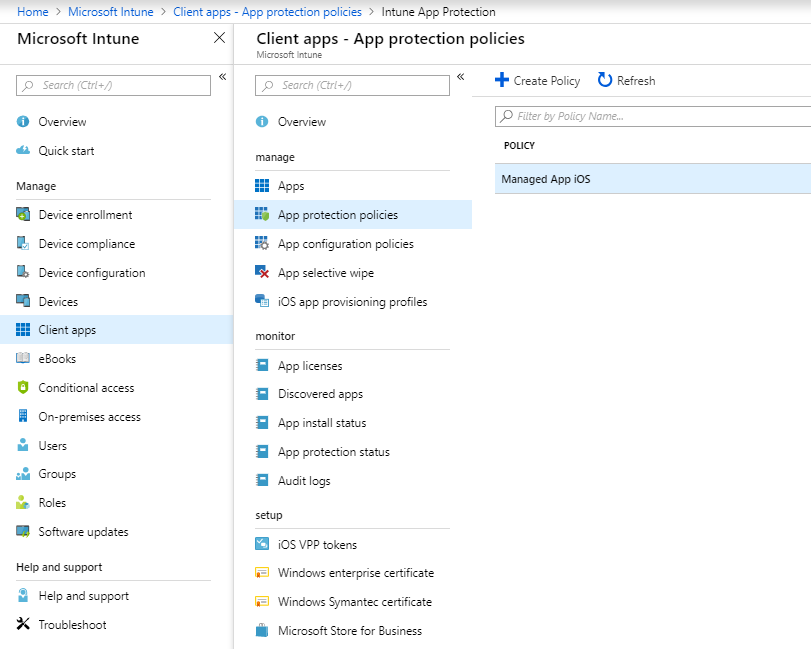
Especially if you plan to enforce app protection policies for mobile devices, ensure you execute the Outlook app for all users. Don’t forget that email is the most cloud app companies use, so make sure the Outlook app is implemented for better protection over your emails. Some companies use mail native, and an app protection policy is not supported.
In conclusion, you can configure a few settings, like blocking printing, forcing a PIN to access the app or adding conditional launch like minimum OS version.
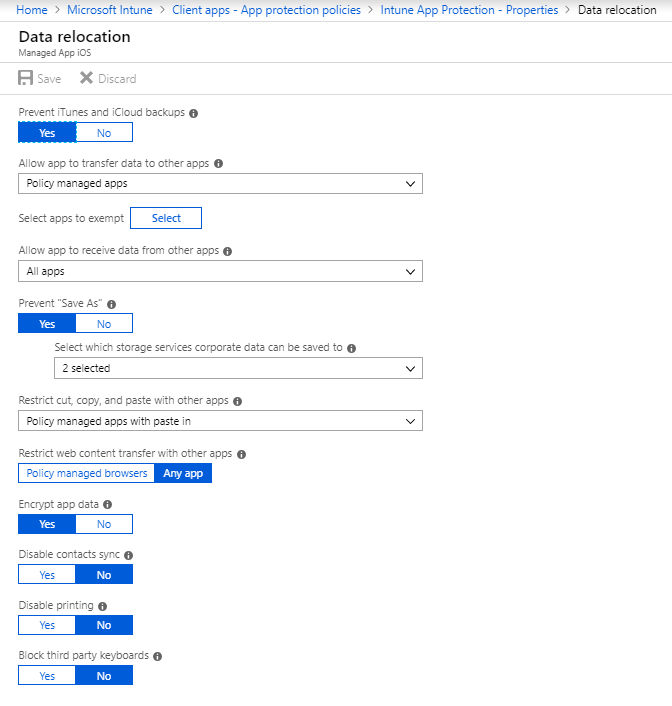
For more information about the Intune App Protection Policy, look to this Microsoft Docs.
5. Conditional Access
The last feature after securing applications is, for sure, conditional access. Why? It’s the control that allows or blocks access to cloud services. In particular, you can base your controls on user attributes, device state, app policy, network location or risk.
Since the beginning, conditional access must be automatic and part of all onboarding plans with Microsoft 365. It’s the least understood feature in business, and yet it’s the most important. In other words, not using conditional access is like removing the doorman in a bar so that everyone can enter your bar without verification.
There are some connectors with third-party solutions you can use as a source of information for your compliance policies and conditional access rules.
Of course, educate your users to embrace MFA so you can enforce multi-factor authentication with the Microsoft Authenticator App and raise the level of protection in your environment.
- To create a conditional access rule, navigate to Microsoft Intune, Conditional Access and click New Policy.
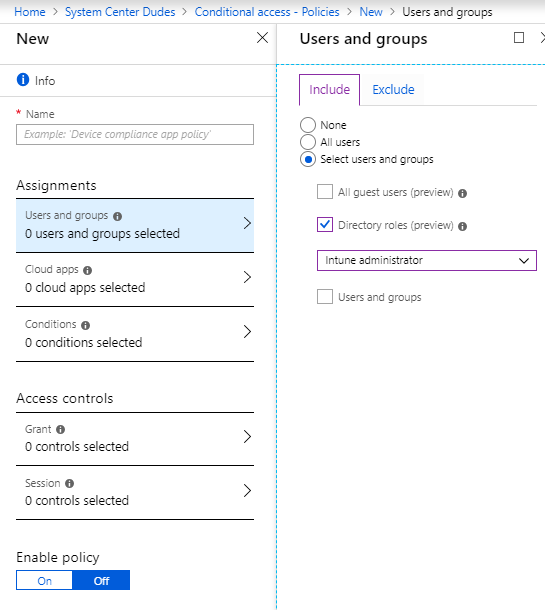
- To make it work, you need to select at least one app, a user or group, and one access control.
- Block access control wins with multiple policies applied to the same user
- Use Block access control with moderation.
- Avoid using all users, all apps and all device platforms
- What if the tool is your best friend
- Test your policy with a small group before going at large
- Do not over-use the amount of rules; keep it simple.
Make sure these situations are covered for a bulletproof:
- Devices enrolled in Intune are compliant.
- Windows devices are hybrid-joined
- Unknown devices, guest users and user-device risks are challenged.
- Unwanted platforms and legacy authentication are blocked
- Approved client apps are enforced
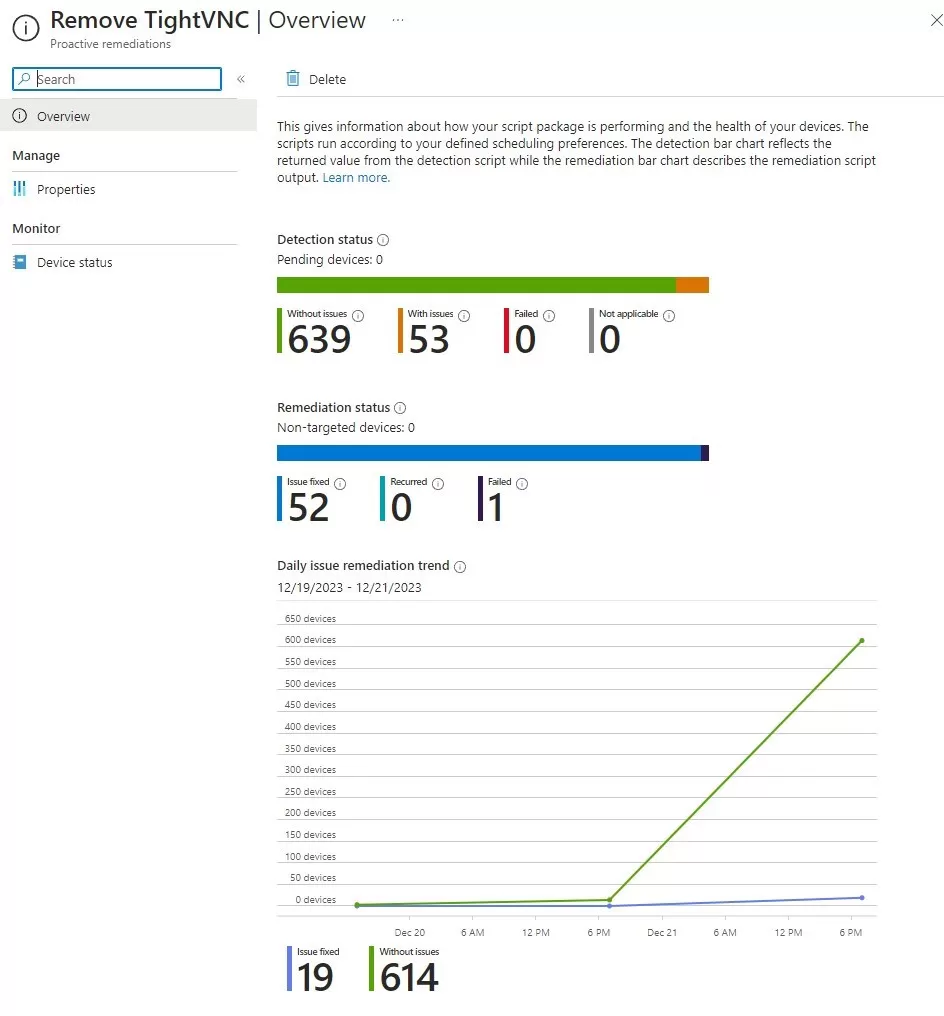
Security Features Microsoft Intune Overview
Finally, security on our devices is critical in 2023 and should not be taken lightly. Wearing a security hat should be part of every IT decision without affecting productivity.
I hope these top 5 no-brainers will help you better secure your devices with Microsoft Intune. What are your top security features?











Anthony LaMark
08.29.2019 AT 03:19 PM