

This blog post will explain how to move all users from the Native Mail app to the Outlook app with Intune. (Intune iOS Mail to Outlook app). Nowadays, the smartphone takes up a lot of room in our personal and professional lives. Being able to receive your work emails directly on a mobile device is becoming popular. Based on the latest numbers provided by Brad Anderson from Microsoft, companies are more willing to use mobile device management solutions like Microsoft Intune and let users access company data from outside the corporate network. Some companies shared beautiful stories of using Microsoft’s EMS solution, like Pepsi Cola and much more.
Companies benefit greatly from letting their employees access corporate data from everywhere, especially emails. Several mail applications are available in the App Store or Google Play Store for Android, but the iOS native mail and Outlook apps are the most popular for iOS platforms. Which one do you prefer?
Some users will gain more productivity with the iOS native mail app, while others will choose the Outlook app for preference and security. The good thing about the Outlook app with Intune is that it supports the MAM policy that protects data in the application.
Using a non-Microsoft mail app exposes you to the risk of getting minimum support. For example, a few months ago, Apple modified how iOS Mail native works; some users were affected by the new version and couldn’t synchronize with Office 365. If your MDM is Microsoft Intune and you want to secure your mobile devices, we highly recommend that you enforce the use of Outlook App without exception.
It’s not something hard to do as long as you follow a guideline if your goal is to do it smoothly. This blog post will explain how to move all users from the Native Mail app to the Outlook app with Intune.
Intune iOS Mail Outlook app – Better Together
The learning curve with a new application may seem obvious and accessible, but for some, it’s not. Each person manages emails differently and uses different options. Migrating to Outlook means changing how they work and learning the new app. There are good chances that you create a shock wave in your company if you coordinate to block the iOS mail native app and the installation of the Microsoft Outlook App simultaneously.
What about using both apps during a grace period? Users can test the Outlook App, report technical issues or request features. A kind of inside technical preview! Doing it this way won’t affect productivity.
Deploying Microsoft Outlook App
With Intune, you can configure a required deployment of the Microsoft Outlook app for iOS and target a group or all users. This ensures that all enrolled devices in Intune receive the Microsoft Outlook app.
- To deploy an application with Microsoft Intune, open your browser and navigate to https://portal.azure.com/#blade/Microsoft_Intune_Apps/MainMenu/1/selectedMenuItem/Overview
- Click on Add and select App Type iOS.
- Click on Search the App Store and type Outlook in the search field.
- Once you find Microsoft Outlook, select the app and click Select at the bottom.

- Review the information provided automatically by clicking on the App information.
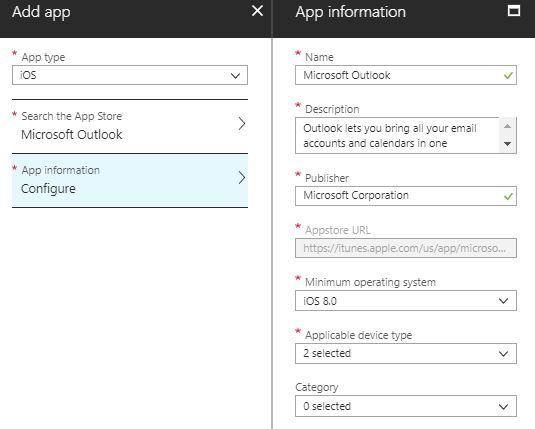
- Once you’re ready, click on Add at the bottom.
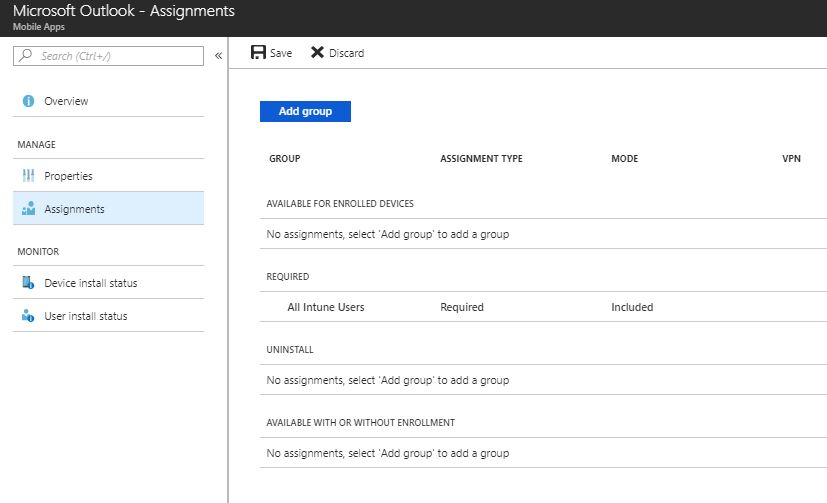
- The application has been created but not assigned yet. To assign the application to a group, click on the Assignments blade and Add the group.
- Select Required at Assignment type to enforce the app on mobile devices
- Select Included Groups and choose which group you want to target or use both switches to deploy to all users or all devices. Once you configure the included assignment, click on Ok at the bottom
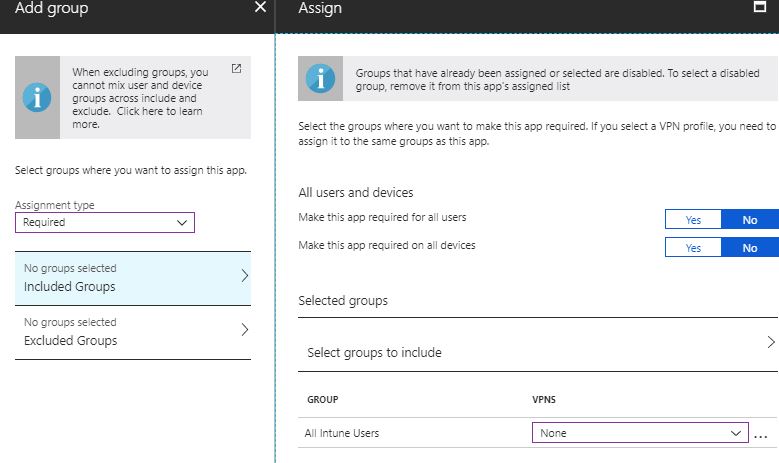
- If you want to exclude a specific group that doesn’t like to receive the app automatically, click on Excluded Groups and select the group
- To save the assignment, don’t forget to click on Save at the top of the assignments blade.
Intune iOS Mail Outlook app – Assign an App Protection Policy
Now that the application is currently being deployed to all your devices, you must secure your app data in the Microsoft Outlook App for iOS. This will make sure to containerize the content of your company data in the app and block copy-paste or save-in. MAM protects corporate data from managed apps to personal apps.
- To create an app protection policy, open your browser and navigate to https://portal.azure.com/#blade/Microsoft_Intune_Apps/MainMenu/14/selectedMenuItem/Overview
- Click on Add a policy and type a policy name
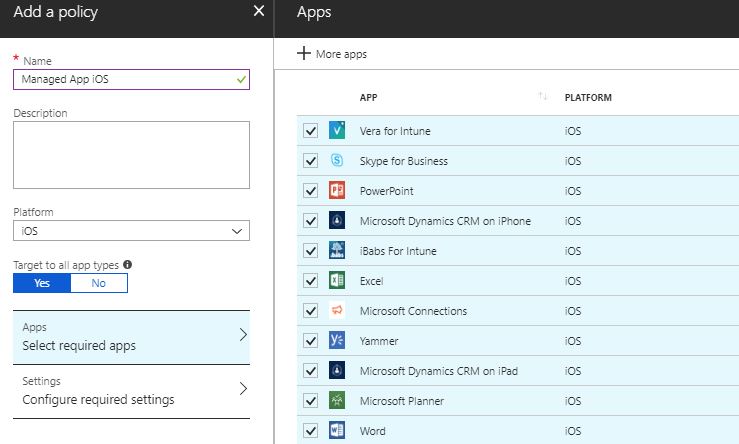
- Make sure the platform is iOS and click on Select required apps
- For a better user experience, check all apps and click Select at the bottom
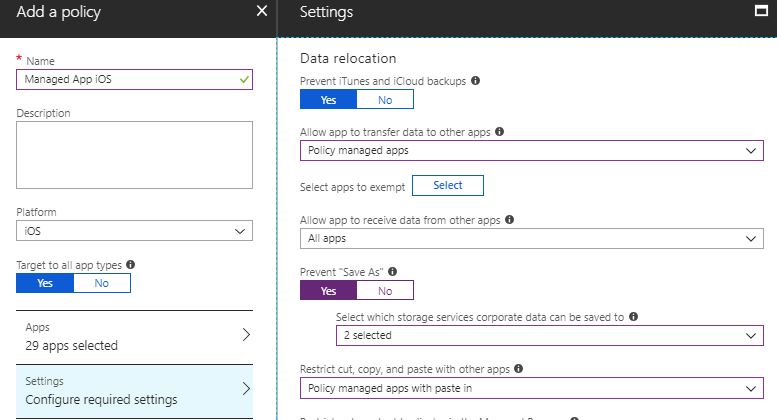
- Click on Configure required settings and change these settings
- Allow the app to transfer data to other apps
- Policy managed apps
- Prevent “Save As”
- Yes
- Select which storage services corporate data can be saved to
- OneDrive for Business
- Sharepoint
- Restrict cut, copy and paste with other apps
- Policy-managed apps with paste-in
- Allow the app to transfer data to other apps
- Click on OK at the bottom once you’re finished
- Click Create at the bottom to save the new policy
Now that the policy is created, we will assign it to the same group we used to deploy the Outlook app.
- Click on your new policy and then click Assignments
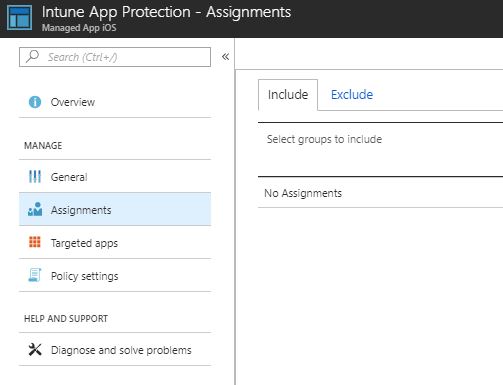
- Click on Select Groups to Include, choose the same group previously selected for the Outlook app assignment and click Select
From now on, users who have already installed the Outlook app will start to get this popup on their iPhone

Blocking Mail Native App with Conditional Access
The Outlook app is now deployed, and users can use it securely. Users will start to use the application side by side with the iOS mail app. Consequently, users will use this time to learn functionalities and become familiar with the new app.
By experience, try to educate your users with videos or step-by-step guides. Explain to them the use of Microsoft support directly in the Outlook app. User Voice is also available to see which features are coming soon.
Suppose some users don’t want to use the iOS mail app anymore and you are deploying an email profile with Intune. In that case, you can disable the mail synchronization on the mobile device by going to Settings – Accounts & Passwords.
- Click on your account and deactivate Mail.
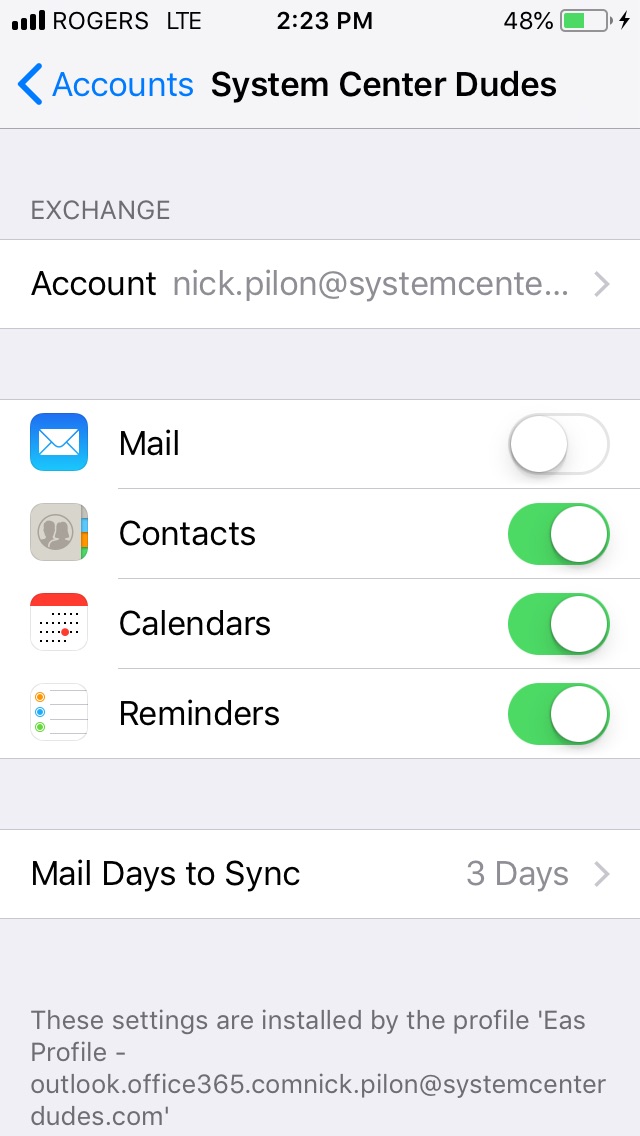
If you deploy an email profile with your MDM, the email profile won’t be removed once you remove the profile deployment. Only a new enrollment will remove the email profile on your iOS devices.
Before going to the next step, wait 2 weeks to 2 months based on the user’s expectations or CSO requirements. It’s a balance between productivity and security. Try to educate yourself the most you can your users before going further.
Are you now ready to block the Mail native app? Follow this step-by-step guide by using conditional access.
- Open your browser and navigate to conditional access blade https://portal.azure.com/#blade/Microsoft_AAD_IAM/ConditionalAccessBlade/Policies
- Click on New and type a policy name like Mail Native Block
- In the Assignments section, click on Users and Groups and within the Include section, choose Select Users and Groups, which is the same group you have been using till the beginning.
- Once you’re finished, click Done at the bottom.
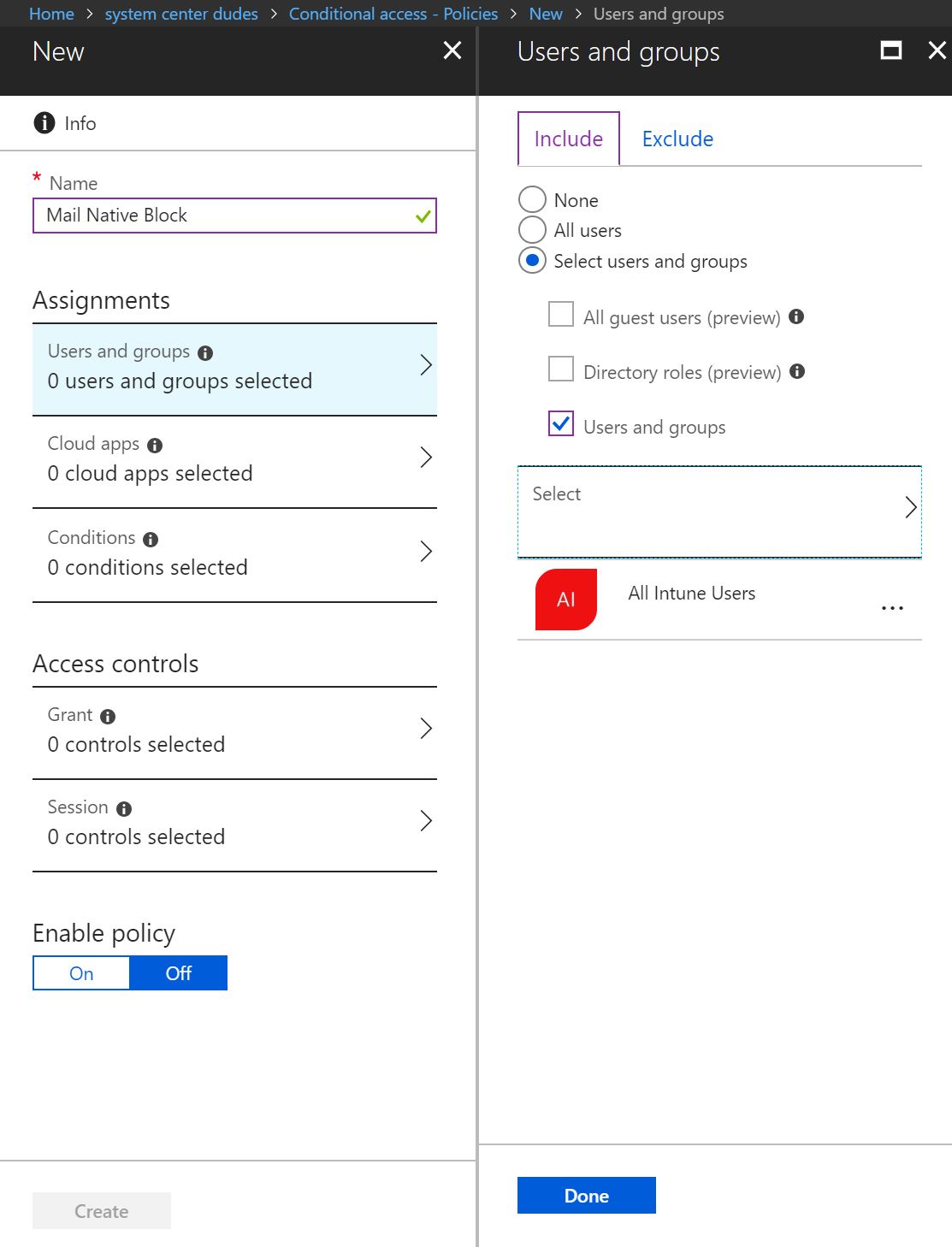
- Click on Cloud apps, select Office 365 Exchange Online to target email service and select Done at the bottom.
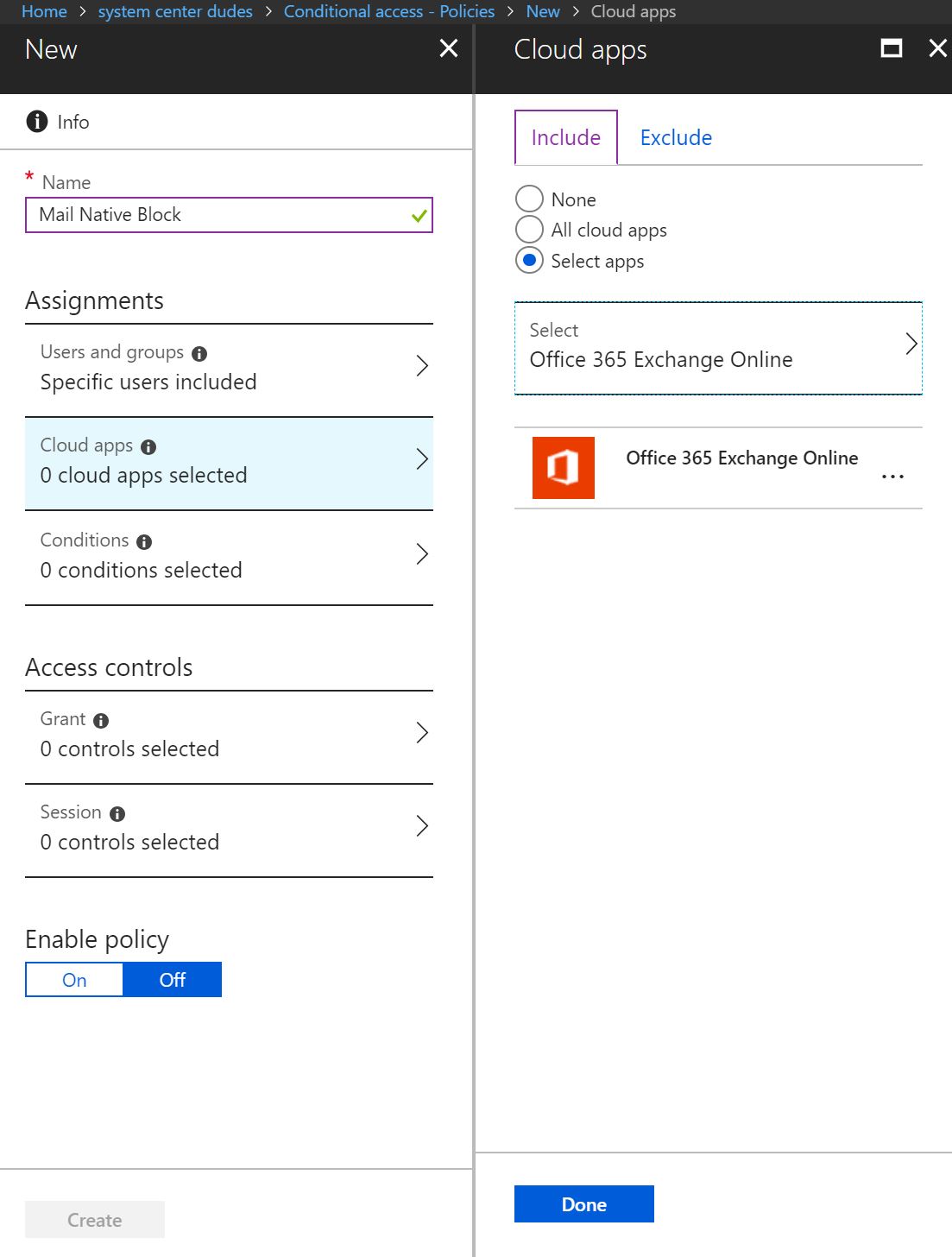
- Click on Conditions blade, and select Device Platforms
- Configure the conditions by clicking Yes, click on Include, select iOS platform and click Done at the bottom
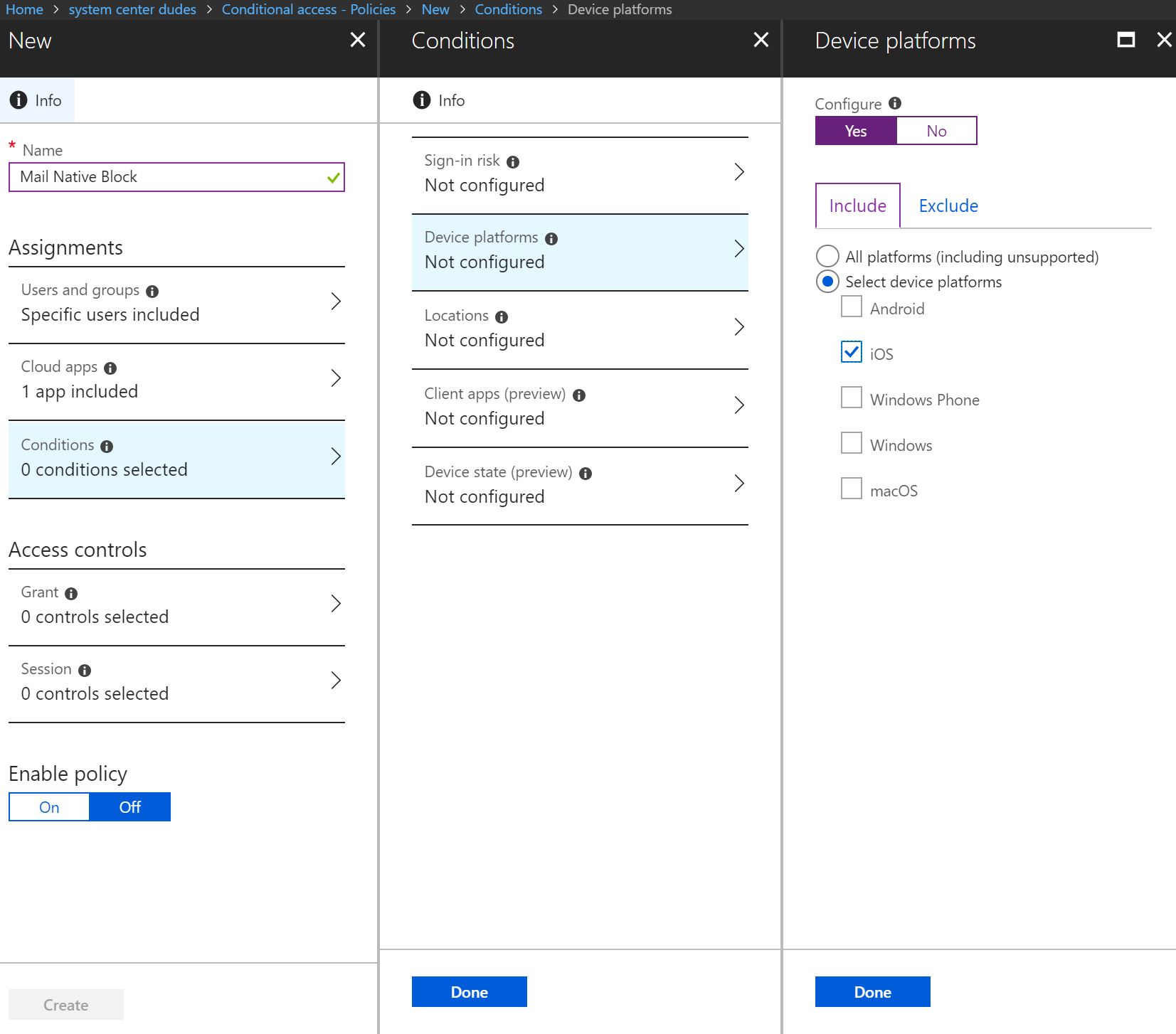
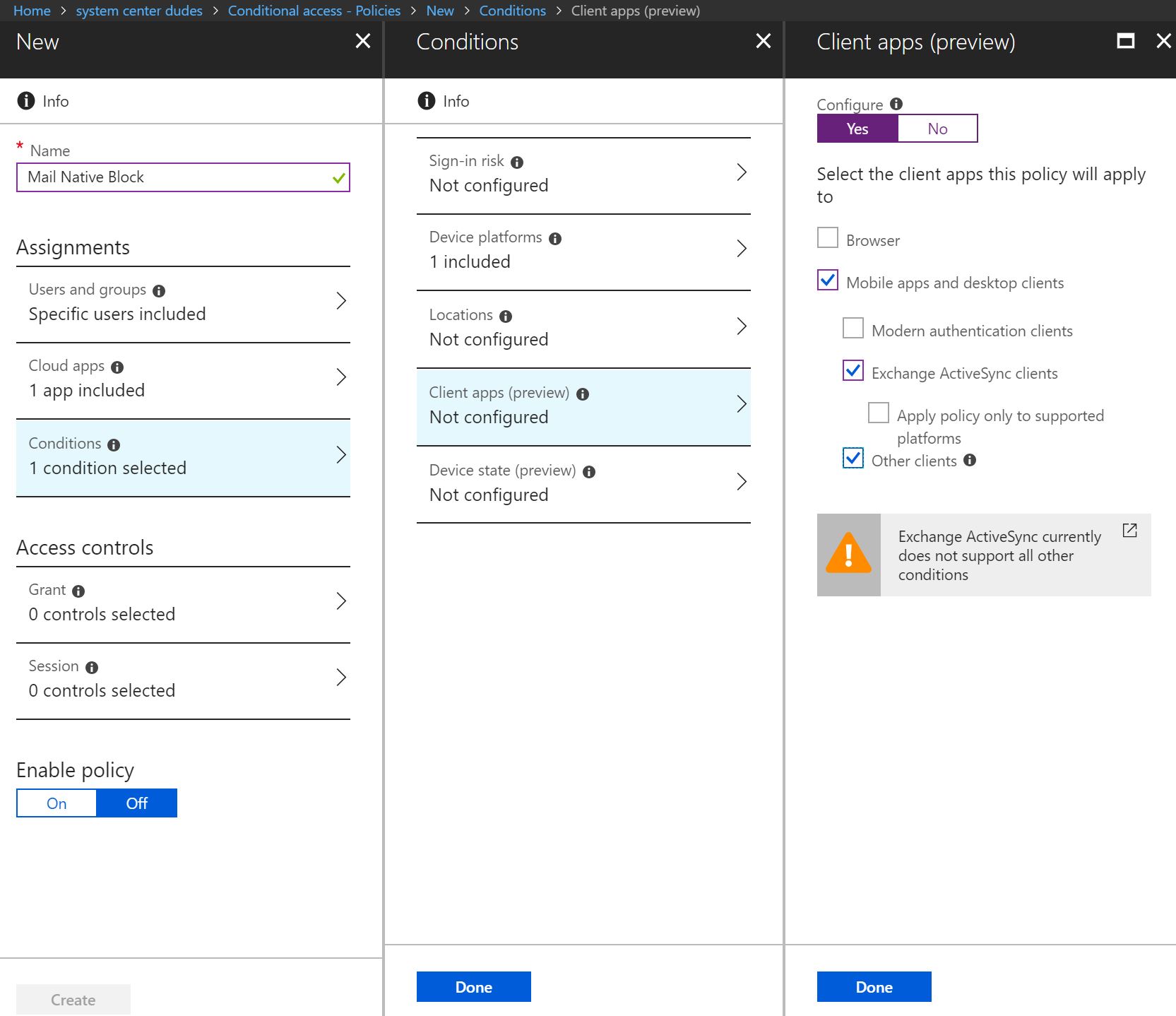
- Select Client apps (preview) and enable by selecting Yes
- Enable these checkboxes
- Mobile apps and desktop clients
- Exchange ActiveSync clients
- Other clients
- Once you’re finished, click on Done twice at the bottom
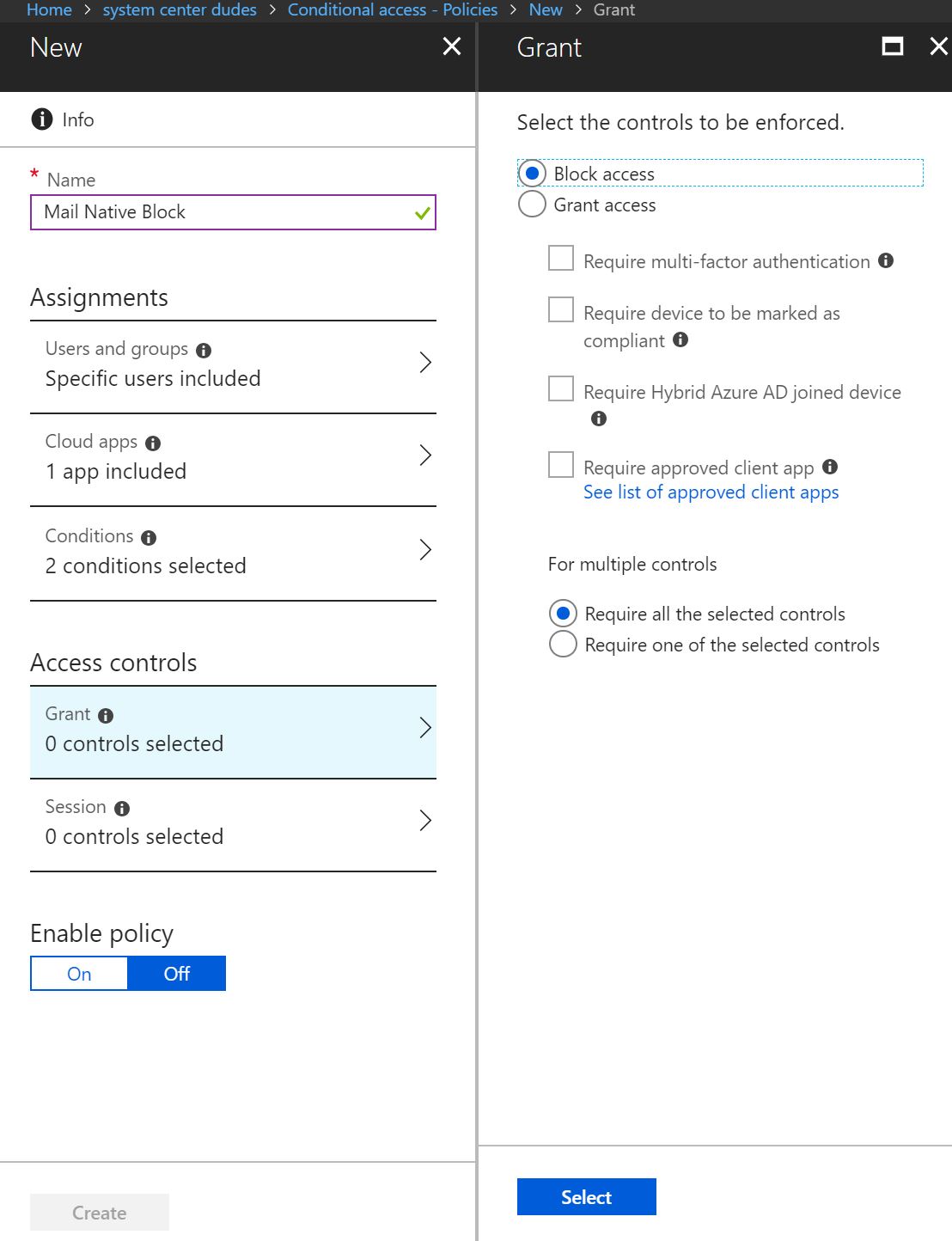
- In the Access controls section, click on Grant blade
- Select Block access in the Grant section, then click Select at the bottom
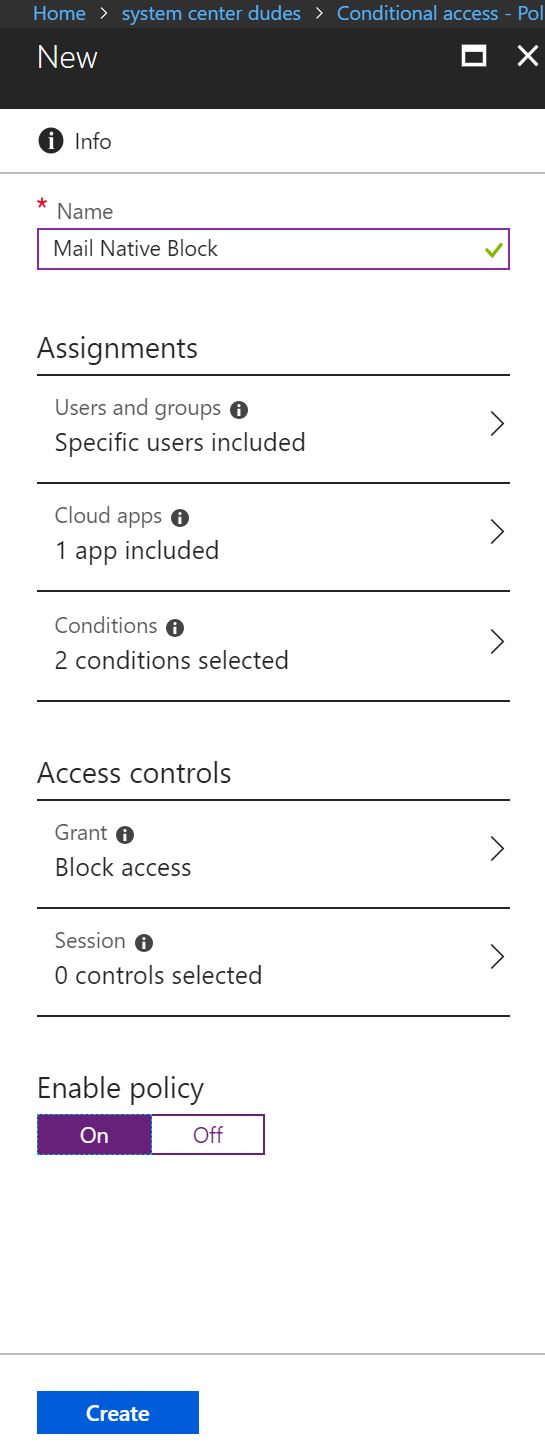
- The conditional access rule is now ready and configured. Enable the policy by choosing Enable Policy at Yes.
Intune iOS Mail Outlook app – User Behavior
Ask your users to open the Mail native app, and if your rule works, you will see this warning email telling the user that the access has been blocked.
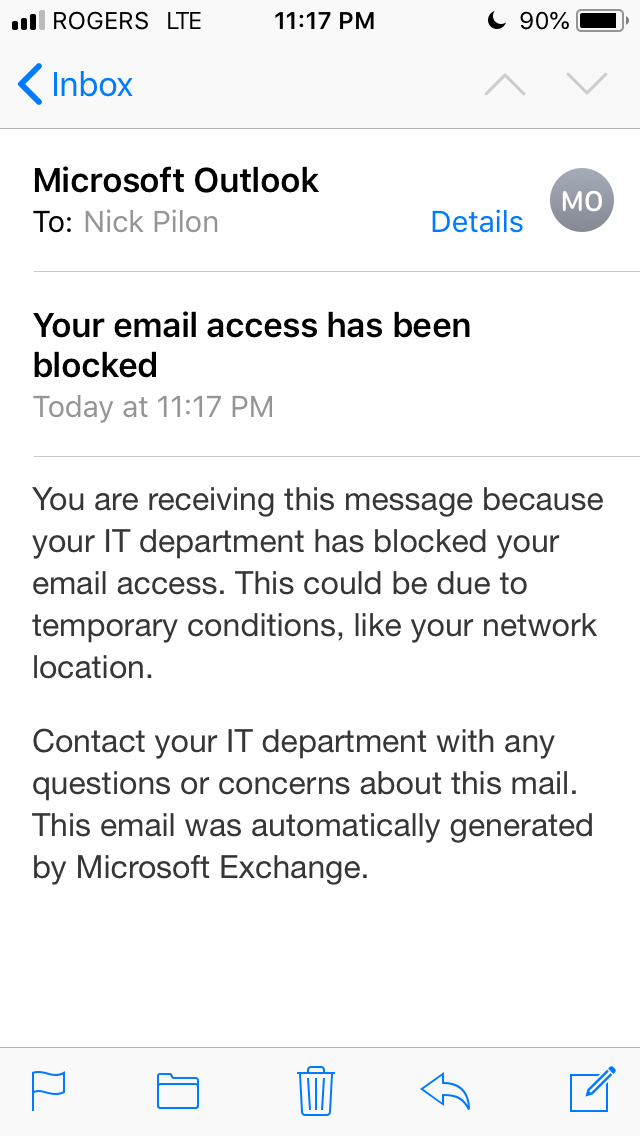
For now, users will need to use Microsoft Outlook app. 🙂
Happy migration!















Frewy
03.15.2020 AT 09:31 PMNicolas Pilon
04.02.2020 AT 10:53 AMVinayak Bhagwat
12.19.2018 AT 09:22 AMNicolas Pilon
04.02.2020 AT 10:55 AMJérémy
11.29.2018 AT 12:55 PMNicolas Pilon
11.29.2018 AT 04:41 PM