

As the expiration date of Windows 10 approaches quickly, It’s time to plan your journey to Windows 11. Starting from October 14th 2025, all Windows 10 editions except LTSB/LTSC will stop receiving updates and Microsoft won’t support the OS unless you pay for Extended support. The clock is ticking, and planning the upgrade to Windows 11 can be challenging given all the different options and challenges. This post aims to assist you in making the right choice for your environment to establish a SCCM Intune Windows 11 upgrade plan.
Windows 11 Compatibility
Windows 11 is a more secure operating system than Windows 10, but to achieve that, Microsoft had to put strict hardware requirements to leverage the enhanced security features. Therefore, your CPU may not be in the list of compatible processors:
Here’s a list of other hardware requirements for Windows 11:
- Processor
- It needs to be in the lists of supported CPUs above
- 1Ghz minimum frequency
- 2 cores minimum
- System Memory
- 4GB of RAM minimum
- System Storage
- 64GB Minimum
- Security
- UEFI with Secure Boot enabled
- TPM 2.0
- Display
- Must support a minimum resolution of 720p
- A graphics card that supports DirectX 12
- Network
- a Network adapter, either wired or wireless
- Connectors
- At least 1 USB port
To help identify which devices are compatible with Windows 11, there are multiple options available:
- Microsoft Configuration Manager (MCM/MECM/SCCM)
- Our Windows 11 Readiness Report
- Free Readiness MEMCM / SCCM Windows 11 Report
- This free report will give you a detailed view of all your non-Windows11 devices and their compatibility status.
- Our Windows 11 Readiness Report
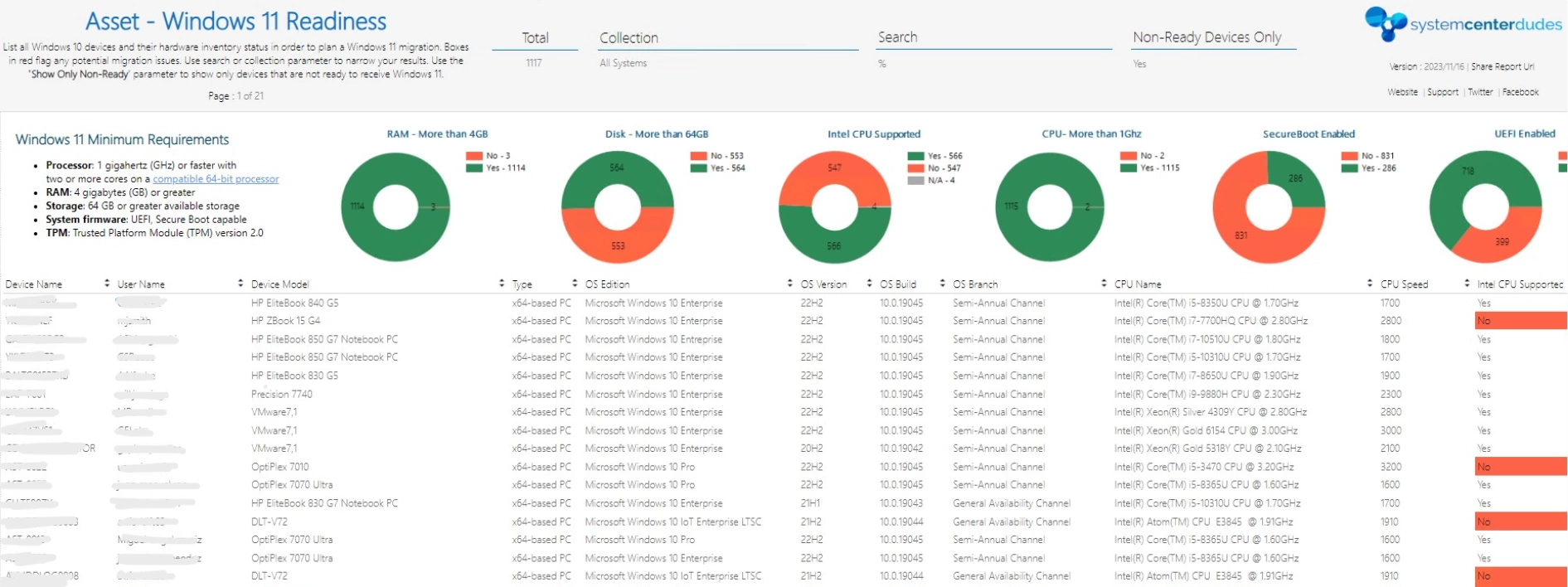
- Microsoft Configuration Manager (MCM/MECM/SCCM)
- With versions 2309 and later, you can use the built-in dashboard under Software Library \ Windows 11 Upgrade Readiness
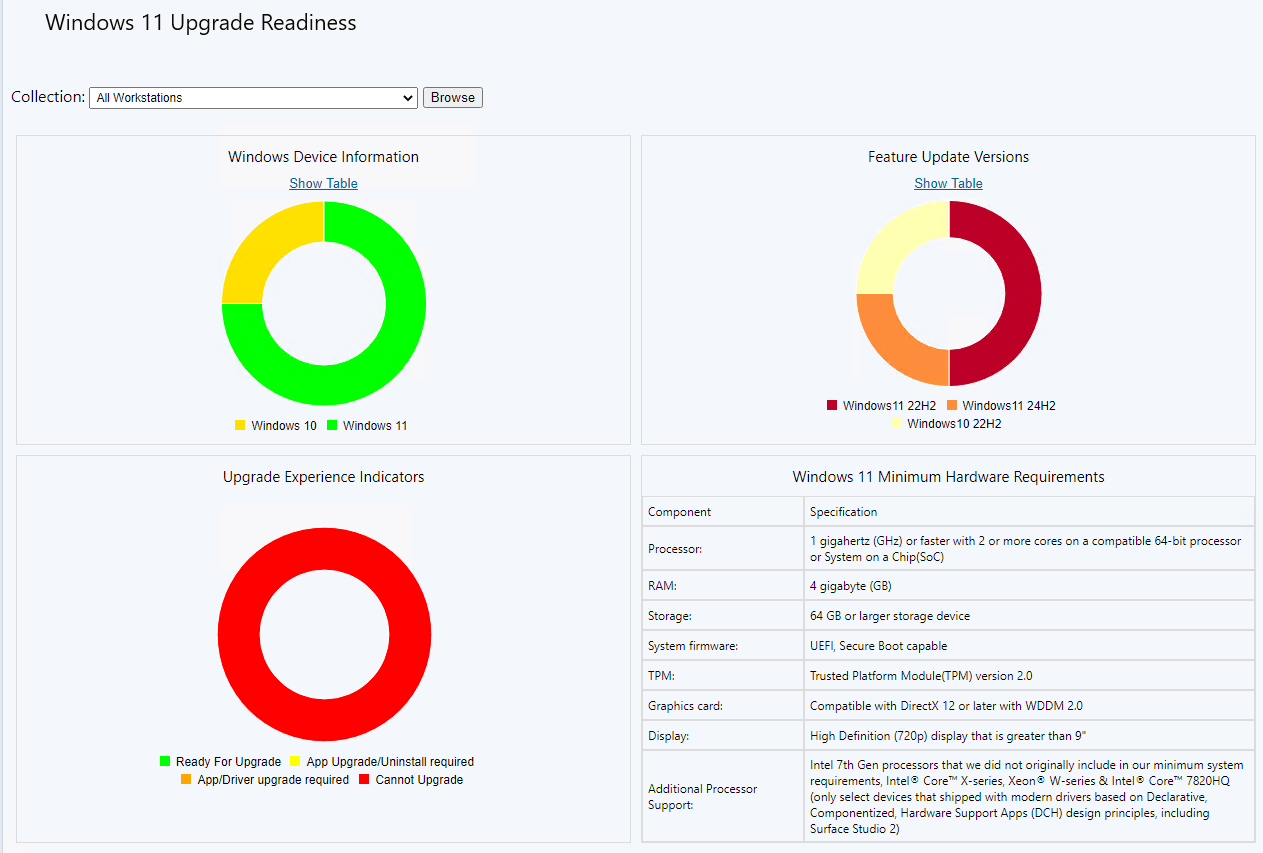
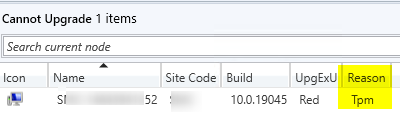
This dashboard will give you a list of incompatible devices if you clock on the red part of the bottom-left circle for “Cannot Upgrade” citing all the reasons why a device cannot upgrade:
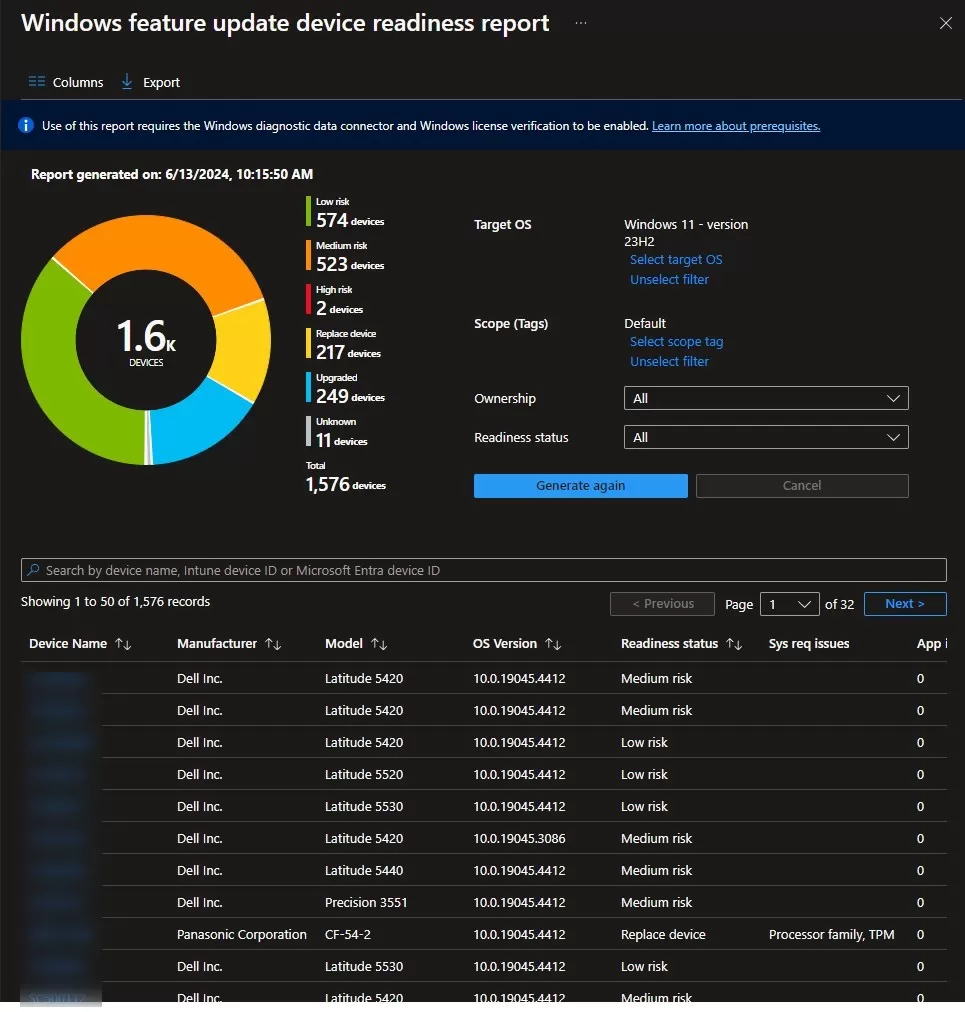
- Intune Report
- For devices that Intune or Co-Managed manages, you can use Intune’s built-in report. See our detailed post here on how to configure and use it: How to evaluate Windows 11 Readiness with Intune
SCCM Intune Windows 11 upgrade plan | Choosing your Upgrade Path
Now that you know which devices are compatible and which ones aren’t, it’s time to plan for an upgrade path. Here’s an overview of the different options that exist:
- Microsoft Configuration Manager (MCM/MECM/SCCM)
- Servicing plans
- devices must have their updates managed by Configuration Manager, not Intune or Windows Updates for Business
- quite easy to implement
- no customizations possible
- Requires connectivity to the SCCM Software Update Point to receive the update
- Update can be downloaded from the closest Distribution Point, CMG (not recommended) or directly from Windows Update/Delivery Optimization
- deployment compliance and reports using the build number will confirm if a device is upgraded
- Upgrade Task Sequence
- devices must be managed by Configuration Manager or be Co-Managed
- implementation can be easy using the template, but can become more complex as you customize it
- allows for infinite customization of pre-flight, in-flight and post-flight customizations.
- Can be used to overcome software blocks that other upgrade methods cannot get around or will ignore
- Upgrades with Task Sequence tend to take longer than the ones pushed by servicing or Windows Update.
- Requires connectivity to the SCCM Server and closest DP to download and launch the task sequence
- deployment compliance and reports using the build number will confirm if a device is upgraded
- A step-by-step progress is sent to the SCCM Server for progress tracking (when online)
- smsts.log can be used to troubleshoot failures or misbehaviors
- OSD Task Sequence
- Same as above, but instead of upgrading the existing Operating System, this would wipe the OS and install a fresh Windows 11
- Can be preferred if looking to move all your Windows 11 devices as Entra ID Joined instead of Hybrid
- Useful when your currently installed OS is unstable and you’d rather start fresh
- you may use USMT or similar solutions to keep your user’s profiles after the wipe
- if doing domain join within the task sequence, the device must be in the office to run this upgrade scenario
- Very complex and will require extensive testing before going to production
- *Unsupported* This is a way to bypass the hardware requirements of Windows 11, but you must be aware that some features won’t work post-upgrade, you may be missing drivers for some devices, have performance/stability issues, and you may be blocked from further feature upgrades (example, Win11 23H2 to 24H2). This should only be acceptable for Labs, testing and last resort as a temporary measure until an imminent hardware refresh.
- Servicing plans
- Intune
- Windows Update for Business; Feature Upgrade
- devices must have their updates managed by Intune: Intune managed devices or co-managed with the workload managed by intune
- very easy to configure and plan phased rollouts
- no customizations possible
- can take time before the computer receive and process the upgrade (from a few minutes to a few days)
- can run from the internet without VPN as policies are cloud-based and content is downloaded from Windows Update/Delivery Optimization
- Intune reports will eventually show the device as running Windows 11, but information may take a few hours/days to be accurate
- a side option to Windows Update for Business is to use Windows Autopatch, which eases adopting Windows Update for business rollout strategy
- Win32 App
- You may bundle the Windows 11 ISO as a Win32 App, and execute the upgrade using command lines
- This method is probably the most complex of all those listed here
- can run from the internet without VPN as policies are cloud-based and content is downloaded from Windows Update/Delivery Optimization
- Allows customizations, either through home made script that launches the upgrade process (install command line of the win32 app) or using setup.exe’s custom actions parameters, pointing to batch files to run at different staged of the upgrade
- you may use custom scripts and scheduled tasks to manage the offering with toast notifications pointing to the win32 upgrade app in the company portal, manage postpones and deadlines
- This is your best option for maximum flexibility if you don’t have configuration manager in your environment and need to customize your upgrade process through the cloud
- Windows Update for Business; Feature Upgrade
- Group Policies
- Windows Update for Business
- nowhere near as elaborate as the Intune Feature Update, but allows basic level of upgrade management
- can be confusing to configure correctly
- no customizations possible
- requires the device to receive the group policy at least once, then can be upgraded from the internet later
- Reporting limited to OS Build info stored in the AD object and how you query it
- Requires the computer to talk to Active Directory to update the information, which can take several days if users don’t frequently come to the office or connect to the VPN
- you’ll need to build some kind of report manually as there is nothing that exists natively within Active Directory
- Windows Update for Business
- Anything else
- in IT, sometimes you need to be creative when your hands are tied and you have limited options. Here are some other solutions you could look into of none of the above suit your needs
- MDT (deprecated)
- PSDT (Community PS-Based version of MDT)
- ISO (initiating the upgrade from the ISO)
- WinRM (Powershell script that would talk to endpoints, copy the files on their machines and execute the update)
- Community tools
- etc…
- in IT, sometimes you need to be creative when your hands are tied and you have limited options. Here are some other solutions you could look into of none of the above suit your needs
Windows 11 Dynamic Update
A key component of the Windows 11 upgrade process is Dynamic Update. Windows Setup contacts a Microsoft endpoint to fetch Dynamic Update packages and then applies those updates to your operating system installation media. The update packages include the following kinds of updates:
- Updates to Setup.exe binaries or other files that Setup uses for feature updates
- Updates for the “safe operating system” (SafeOS) that is used for the Windows recovery environment
- Updates to the servicing stack necessary to complete the feature update
- The latest cumulative (quality) update
- Updates to applicable drivers already published by manufacturers specifically intended for Dynamic Update
- Dynamic Update preserves language pack and Features on Demand packages by reacquiring them.
Devices must be able to connect to the internet to obtain Dynamic Updates. In some environments, it’s not an option to obtain Dynamic Updates.
When upgrading to Windows 11 from Intune, SCCM Servicing or Windows Update, Dynamic Update doesn’t apply.
Using the ISO with either scripts or Win32 app method mentioned above, Dynamic Update is natively used without any further configurations needed.
If upgrading using SCCM, you must ensure that Dynamic Update is enabled in your task sequence’s Upgrade Operating System step. If upgrading from a Windows 10 1803 and earlier, you also need to ensure you get the Dynamic Update packages in your SUP/WSUS. With Windows 10 1809 and Later, it will reach out to the internet to get the DU content.
In some cases, Dynamic Update may be causing issues and prevent the upgrade from happening. If DU is causing you headaches, then you should try disabling it and see if this improves your upgrade experience.
Customizing your Upgrade Experience
As you probably know, some methods mentioned above support customizations. What exactly can be customized? Pretty much anything you can script. Here are a few examples of thing we typically see:
- Pre-Flight actions to remediate soft blocks
- If you’ve tried upgrading from the ISO or Windows update and got blocking errors about an application or configuration that isn’t supported for Windows 11, you may remove these blocks just before running the upgrade
- Enable Secure Boot
- While at this point most of your devices should already be in UEFI mode, Secure Boot may not be enabled. If that’s the case, then you’ll want to enable it before upgrading to Windows 11. This is usually done with tools provided by the hardware vendor in a task sequence, or by using WMI functions.
- Custom UI
- You may want to provide a custom update experience using splash screens to prevent your users from working while the update is preparing or provide toast notifications to let your users know what’s happening and let them know when the update is complete and they can use their computer again.
- Custom Start menu / taskbar layout
- The layout used by Windows 10 is not compatible with Windows 11, so you’ll need to go through that customization process again and make a new config to push to standardize your user’s taskbar.
- Just keep in mind that this may remove the user’s pinned apps from both the Start menu and Taskbar
- Remove unwanted modern apps
- a little PowerShell script can be run to remove the modern apps that come with Windows 11 if you don’t want them.
- Update Drivers
- Although Windows 10 and Windows 11 share the same 10.0 core, there are many layers added on top of it for Windows 11, requiring Windows 11 specific drivers to keep your devices running to their full potential.
- Refresh Applications
- Some of your apps may need an updated version to be compatible with Windows 11
- While implementing a change as big as an OS Upgrade, it may be a good time to squeeze in other minor changes at the same time, like replacing an application with another one in Windows 11, such a new default PDF reader, default browser or VPN Solution.
- Remove obsolete applications that should no longer be used in your environment
Policies applied to Windows 11 only
While you’re implementing a change as big as a major OS upgrade, might as well enable some features you’ve been wanting to implement for a while. Here are some policies we recommend enabling via policies/GPO using a Filter for Windows 11 only:
- Wi-Fi profile changes
- Windows 11 doesn’t support PEAP automatic sign-on without a certificate anymore, you’ll get a prompt asking if you’re sure you want to connect to the untrusted network
- Specifying your Trusted Root certificate as well as your authentication server should get you around this annoyance
- It may be a good opportunity to switch to EAP-TLS (Certificate) Authentication instead of PEAP (username and password)
- Windows Hello for Business
- If this was not yet enabled in your environment, you should certainly consider enabling it for your Windows 11 devices
- Windows Hello is more secure than password authentication if well configured, and adds convenience as you’ll be able to login with biometrics, like face recognition and fingerprint on compatible devices.
- Security baselines
- Microsoft’s Security Baselines offer strong security settings that will help improve your secure score in Microsoft Defender for Endpoint (MDE).
- As always, enabling Security features may break or alter user functionality, so be sure to thoroughly review the proposed changes in the baseline, test, and if needed, document any settings you’ve changed from the baseline
- Credential Guard with Virtualization-Based Security (VBS)
- As UEFI and SecureBoot are required for Windows 11 and for VBS, might as well used this opportunity to enable this security feature.
- Be sure to enable it WITHOUT UEFI lock first, as if issues arise in the first few weeks after the deployment, you’ll be able to rollback the policy for affected devices. if you do enable UEFI lock, then you’re in for a ride if you want to remove the policy from these devices, so consider that when enabling UEFI Lock, there’s no turning back.
- Attack Surface Reduction (ASR) rules
- ASR Rules are a great way to protect your devices by blocking commonly exploited backdoors, such as running processes from PDFs or Excel spreadsheets for example.
- Be careful when enabling the policy that’s blocking PSEXEC, as this will cause issues with SCCM; it’ll fail to run tasks as local system, such as installing applications and run PowerShell scripts.
- Windows LAPS
- I made a blog post about this when it was released about 2 years ago, but this is still relevant today. Windows LAPS will allow you to manage the built-in local administrator account’s password, or another local admin account that you defined. Each device will have its own password for the local admin account, and it’ll rotate based on your configured preferences
- If you’re still using the old LAPS using the MSI and GPOs, you should definitely consider the migration to the new LAPS, remove your old GPO and uninstall the MSI from your devices
- OneDrive and Known Folder Move (KFM)
- This one is a no-brainer honestly. If you haven’t implemented OneDrive in your environment yet and are licensed for it, know that all your user accounts are allocated 1TB of storage, and you can pay to extend them to 2TB if needed
- KFM will automatically redirect the user’s Documents, Desktop, Downloads, and Pictures folders to OneDrive if you select them in your policy. One this is done, you don’t need to worry about users losing documents ever again when re-imaging or wiping their devices.
- Tools are provided by Microsoft to migrate home/personal drives and many other sources to the user’s OneDrive as well
- Delivery Optimization (DO)
- This allows your computers to peer amongst each other any Microsoft cloud content, such as Windows updates, Definition updates, Office (MS365 apps) updates, Edge updates, and many more.
- Leveraging DO will allow you to switch automatic updates on for all Microsoft products without having to worry about killing your network connection every second Tuesday of the month.
SCCM and Intune Windows 11 upgrade plan – Conclusion
We were promised Windows 10 would be the last Windows Ever, it was “so good, we skipped a number” as Microsoft said, but here we are. Windows 10 is at its last mile and Windows 11 is upon us. Hopefully, this guide will help you plan your transition to Windows 11.
We have many blog posts at System Center Dudes that can help you implement some of the ideas presented in this post, and more will come. We understand this is a huge project, and we are here to help you in any way that we can, whether it be with blog posts or with our consulting services.














Geoff
02.20.2025 AT 05:13 PM