
Windows Autopatch is a cloud-based solution that automates the update process for Windows, Microsoft 365 Apps, Microsoft Edge, and Microsoft Teams. This service ensures that systems are always up-to-date with the latest features and security patches, reducing the workload on IT teams and minimizing disruptions. Microsoft recently reviewed the integration of Windows Autopatch within Intune to clarify the behaviors.
Depending on the current patch management state, it is definitely worth taking a look. Businesses already using Windows Update for Business can evaluate Windows Autopatch, but the gain will be less noticeable compared to other patching solutions, like Configuration Manager (SCCM), WSUS, or simply not managing updates at all.
In this blog post, we’ll go over the requirements and configurations to get going with Windows Autopatch in Microsoft Intune.
Windows Autopatch vs Windows Update for Business
At a very high level, both are achieving the same. Defining how updates and feature updates are delivered to Ring, when, and what type of user impact to deal with.
Autopatch will even simply create equivalent policies to Windows Update for business, looking at the same settings, just created automatically in the majority.
The key differences are :
- Autopatch will automatically split devices in the number of ring defined, based on a percentage of the total device.
- Autopatch can manage patching behavior for Windows, Microsoft 365 Apps, Edge, Teams, and Drivers.
- In comparison, Windows update for business only manage Windows and Drivers
- Windows Autopatch requires Windows 10/11 Enterprise.
- With Windows Autopatch, Microsoft will manage to cancel problematic quality/feature update deployment using Telemetry. WUfB would requires for an admin to pause the updates.
If you have the required license and aren’t already using WUfB, it’s a nice shortcut to get going with patching out of classic patching solutions like Configuration Manager (SCCM) or WSUS.
If you already have WUfB configured, and are happy with your patching process, it is a bit harder to justify the move to Autopatch, other than offloading the management completely.
 |
|---|
Prerequisites
- Windows 10/11 Enterprise
- Any E3/F3 or E5 licenses that enable Windows 10/11 to be Enterprise is authorized.
- Hybrid Entra Joined or Entra joined devices.
- Domain-only devices are not supported.
- Internet access for devices to reach Microsoft services
- See the URL list from Microsoft Learn.
- Global Administrators’ rights to enable the feature activation
- Intune Administrator will provide access to configure Windows Autopatch.
Limited features for Windows Autopatch are available for Windows Business Premium and Education licenses. See Feature Entitlement for details.
For more details about Windows Autopatch requirements, see Microsoft Learn.
Enable Intune Windows Autopatch
The first step is to enable the feature of Windows Autopatch in the Intune portal. Ensure to have the Global Administrator rights.
- In the Intune portal
- Browse to Tenant Administration / Windows Autopatch / Feature Activate
If you do not see the Windows Autopatch section, it means that the licensing isn’t one of the above mentioned in the requirements.

- Check the box to enable Windows Autopatch and click Activate

- Once enabled, review the Tenant Management under Tenant Administration / Windows Autopatch

- Address and fix potential issues. This will differ from one environment to another. In this case, some access needed to be restored to default.

- Under Tenant Administration / Windows Autopatch / Admin Contacts, add IT admin contacts for Microsoft to send out issues and status updates about your environment.


These email includes:
- Status about the Autopatch service
- A patching Update schedule at the beginning of the month
- An update summary at the end of the month
Email example:
Quality Update Schedule
Windows Autopatch
When will this happen
The August 2024 Windows quality update (2024.08 B) will be deployed on the following schedule to all Windows Autopatch devices:
| Deployment Ring | First Deployment | Goal Completion Date |
|---|---|---|
| Test | August 13, 2024 | August 13, 2024 |
| Ring1 | August 14, 2024 | August 16, 2024 |
| Ring2 | August 19, 2024 | August 21, 2024 |
| Ring3 | August 22, 2024 | August 27, 2024 |
| Last | August 24, 2024 | August 27, 2024 |
Create Windows Autopatch Groups
The main configuration for Windows Autopatch is the Group creation. This is the root of all the various configurations that will be generated upon it. A Windows Autopatch group is a logical grouping of all rings of a given list of devices. Most enterprises will have a single group, which will define multiple Rings of Windows Update policy that will handle all their devices. Don’t get confused, this is NOT an EntraID group, it’s a completely separate concept.
A scenario for multiple Windows Autopatch groups could be for large companies with different regions that are managed by different teams, like NCSA, EMAE, and APAC.
- To create the Windows Autopatch group, browse to Tenant Administration / Windows Autopatch / Autopatch Group, and select Create

- Input the name of the group. This is usually the Company name, so it makes sense later.

- Defining the Deployment rings is likely the most complex step of all Autopatch configuration.
- by default, 2 Rings exist. These will be assigned to groups matching the name, and are expected to have administrators define the devices to be assigned to each of these groups.
- The Test ring is to assign the first devices to be affected by Windows Update.
The Microsoft recommended number of devices in this ring, based upon your environment size, is as follows:
- 0-500 devices: minimum one device.
- 500-5000 devices: minimum five devices.
- 5000+ devices: minimum 50 devices.
Devices in this group are intended for your IT Administrators and testers since changes are released here first. This release schedule provides your organization the opportunity to validate updates before reaching production users.
- the Last ring is to assign the VIP/DND kind of devices. They will still get patched but will be last.

- Click on Add Deployment Ring to add one or many additional rings.
- These new rings will consist of Microsoft creating groups and automatically assigning devices to each of those, and comply with the percentage of devices defined.
- These rings are to be considered from Pilot to Production

- To populate these groups automatically, we need to define a source group (Dynamic group Distribution).
- Without this, impossible to configure the device distribution percentage for each ring.
- The Dynamic group Distribution essentially consists of an EntraID group, that contains all devices wished to be managed by Windows Autopatch.
- This will enroll devices in the service.
- This will split all devices in the various Rings automatically.
Note This Dynamic Group distribution is NOT required to be an Entra dynamic group. It can be an Assigned group to begin with. Using an Entra dynamic group will make sense once the service is in production, so all devices end up managed by Windows Autopatch.

- Once assigned, the percentage per ring must be defined and add up to 100% total.
- If you don’t specify any percentage, the default value are :
- The Windows Autopatch deployment ring calculation occurs during the device registration process:
- If the Windows Autopatch tenant’s existing managed device size is ≤ 200, the deployment ring assignment is First (5%), Fast (15%), remaining devices go to the Broad ring (80%).
- If the Windows Autopatch tenant’s existing managed device size is >200, the deployment ring assignment is First (1%), Fast (9%), remaining devices go to the Broad ring (90%).

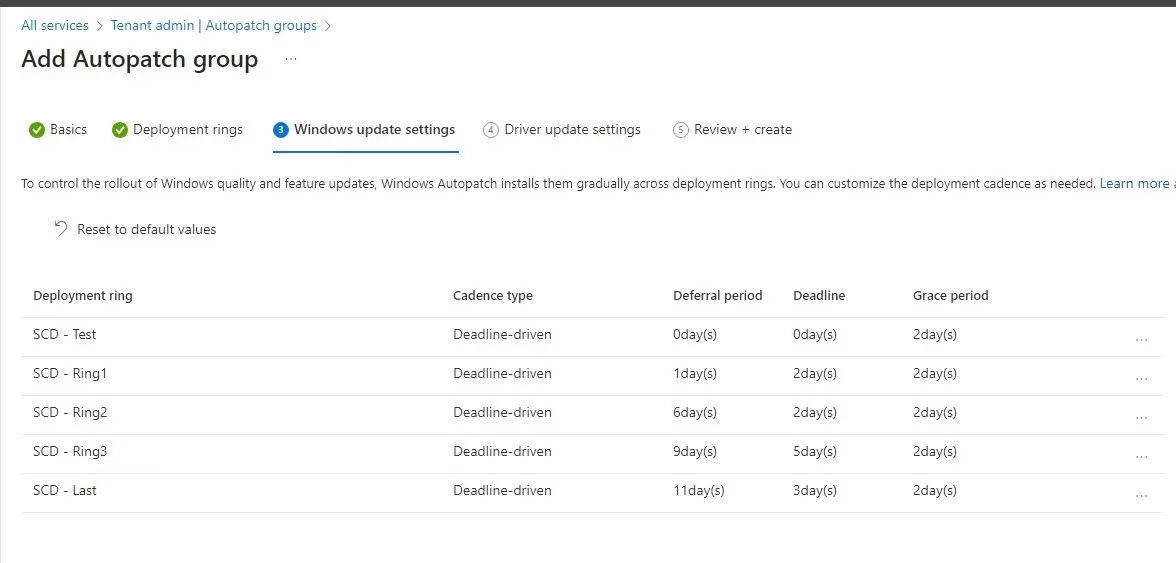
- By default the Windows Update settings are set per Rings.

- It is possible to modify these Deferral, deadline, and grace periods, as well as the notifications.
- Defaults are usually fine for most environments.
- Deferrals
Deferral policies delay the time the update is offered to the device by a specific number of days. The “offer” date for Windows quality updates is equal to the number of days specified in the deferral policy after the second Tuesday of each month. - Deadlines
Before the deadline, users can schedule restarts or automatically schedule outside of active hours. After the deadline passes, restarts will occur regardless of active hours, and users won’t be able to reschedule. The deadline for a specific device is set to be the specified number of days after the update is offered to the device. - Grace periods
This policy specifies a minimum number of days after an update is downloaded until the device is automatically restarted. This policy overrides the deadline policy so that if a user comes back from vacation, it prevents the device from forcing a restart to complete the update as soon as it comes online.



- Decide whether or not to opt-in for the Driver updates, as well as Windows Updates.

- Complete the Windows Autopatch group creation.
Define the Autopatch Update settings
We will now select which product to manage with Windows AutoPatch. In our example, we are enabling M365 and Edge updates.
- Under Tenant Administration / Windows Autopatch /Windows Autopatch Groups, select the tab Update Settings.
- Enable Microsoft 365 Apps updates and Edge Updates.
- These will generate Device configuration profiles to manage those products’ update behavior.

What was created by Windows Autopatch group creation
By creating the Intune Windows Autopatch group, many configurations are created automatically in the environment.
- Entra groups. Do NOT modify those groups.
- Those groups are created by default with the Autopatch group name.
- Test and Last are those for default rings.
Test and Last Group – Warning
Adding or importing devices directly into any of these built-in groups isn’t supported. Doing so might affect the Windows Autopatch service. To move devices between these groups, see Moving devices in between deployment rings.

- These are created based on the Autopatch group name and the number of custom rings selected.
- Again, do NOT modify those groups

- Under Devices / Windows Update / Rings, a set of Windows Update for Business policies are created and matches the Autopatch group configuration.

- Same appears under Feature Updates and Driver Updates, if enabled.


- Finally, multiple Device configurations under Devices / Configurations are also created and assigned to the groups automatically generated.

Assigning Windows Autopatch policies
While most of the configurations and assignments are fully automated, a minimum is needed to be done by an Intune administrator.

- This group is to enroll devices in Windows Autopatch AND to automatically distribute the devices according to the custom rings with percentage distribution.
- This should eventually be pointing to a Dynamic Entra group to include all devices.
- The deployment ring name is also the name of the assigned Entra group.
- Add devices that are considered your first group of test devices.
- Somewhere between 20 to 50 devices usually makes sense to include IT and some test devices.
- This will also enroll devices in Windows Autopatch, so no need to add those to the Dynamic group distribution (1)
- Assign a custom Assigned Entra group that have the devices identified as Test devices(first group to be patched)
- Based on the name, this is the last group. It is not mandatory to add any devices to it. in the above example, Ring3 includes all production devices. the Last group could include some VIP or to fit other needs to be last patched.
- Assign a custom Entra group that have the devices identified as Last devices
Device Group conflict in deployment rings within an Autopatch group
If a device is part of one deployment ring with Dynamic distribution (Ring3), and one deployment ring with Assigned distribution (Test), within the same Autopatch group, the deployment ring with Assigned distribution (Test) takes precedence over the one with the Dynamic distribution type (Ring3).
If a device is part of one deployment ring with Assigned distribution (Test), and in another deployment ring with Assigned distribution (Ring3) within the same Autopatch group, the deployment ring that comes later (Ring3) takes precedence over the deployment ring that comes earlier (Test) in the deployment ring order.
Change a deployment ring
If any devices fall into undesirable rings or you want to move it to another Ring, make sure that you understand the process correctly:
If the device needs to be moved to a static group (Test and Last), you need to use Entra ID group associated with these rings to move the devices.
If the device is in a dynamic group (Ring2, 3, 4), you need to use the Intune console:
- Go to Devices / Windows Updates / Monitor / Devices
- Ready
- Select your devices
- Click on Assign Ring


For more details about Windows Autopatch groups, see Microsoft Learn.
Windows Autopatch Feature Update profile
Windows Autopatch creates a single Feature Update policy that is automatically assigned to all Rings.
The goal of the policy is to set a baseline minimum for the Windows 10/11 build, which is the oldest supported version. Currently, this is Windows 10 22h2. Eventually, it will automatically change to Windows 11 23h2 as this is the next-in-line build to be the oldest supported.


This policy does not affect the ability to force a newer feature update by using a custom Feature Update policy, targeted to test devices or IT folks.
For more details about the Autopatch Feature Update, see Microsoft Learn.
Windows Autopatch device registration
Before managing devices with Autopatch, they need to be registered. The Windows Autopatch Discover Devices function runs discovery hourly.
To register devices, add members to the Microsoft Entra groups associated with the Autopatch groups. Those Microsoft Entra groups are the ones assigned in numbers 1, 2, and 3 from the Autopatch Groups (see screenshot below).
- #1 – Ring 1, 2, 3 will be automatically populated according to the percentage, based on all members of the group you specified (Dynamic group distribution).
- #2- Test group will use the members of the group you created earlier and assign to the group (in yellow)
- #3 – Last group will use the members of the group you created earlier and assign to the group (in yellow)

Once in the Autopatch group, it can take up to 1 hour to appear in the Intune console.
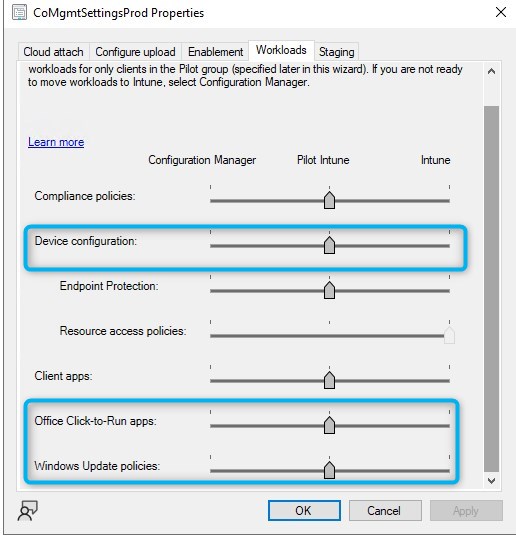
SCCM Comanaged devices
If you are using SCCM, the coManagement workloads for Windows Update for Business, Office Click-to-Run Apps, and Device Configuration must be set toward Intune for the devices to be managed by Autopatch. This is needed because Autopatch needs full control over our patch management settings.
Either Pilot or fully assigned to Intune will work. Adjusting the workload for devices can take some time.
For devices that are not managed by SCCM, this step is not needed.
Expect delays at this step if a device isn’t managed from Intune for those workloads. From experience, expect 24 to 48hours for workload switch to be effective, and device showing Ready in Autopatch.
For more details about Windows Autopatch device registration, see Microsoft Learn.
Windows Autopatch device registration status
Assuming all requirements were in place, devices will register just fine to Windows Autopatch, and receive the assigned policy. But since there are quite a few details, it is possible some devices won’t register correctly.
- To see the list of registered devices, go to Device / Manage Updates / Windows Updates / Monitor.

Not registered
Step one for devices is to register in Windows Autopatch. Failures will be displayed, as well as a list of potential fixes and identified problem

In this case, the device hasn’t processed yet the changes in the Workload to be managed toward Intune Windows Autopatch.

Not ready devices
The next step is to make sure that your devices are in the Ready state. Devices that detect a configuration problem will have the Need Attention state. To troubleshoot this, click on the Not Ready tab at the top and click on the device. It will show the related problem.
The most common sources of conflicting configurations include:
- Active Directory Group Policy (GPO)
- Configuration Manager Device client settings
- Windows Update for Business (WUfB) policies
- Manual registry updates
- Local Group Policy settings applied during imaging (LGPO)
Global Recommendation
If the computer has been added to the right SCCM collection, it should be registered correctly. Some devices needed more than 24h before being ready after being added to the registration group.
User experience
The enrollment is 100% transparent to end-users. The update behavior is evolving from one build to another.
Windows 24h2 will even support hot patch with less reboot overall.
It is an evolving solution, so changes are to be expected down the road for sure, hopefully for the best!
Notifications is one area with recent changes that isn’t crystal clear at the moment.
Strongly recommend testing such settings and review the CSP documentation about those. Keep an eye on it for changes in the doc as well.

Additional configurations recommended for Windows Autopatch
- Delivery Optimization is highly recommended to manage the traffic generated from Windows Update sources.
- The comanagement workload for Windows Update for Business, Office Click-to-Run Apps, and Device Configuration must be set toward Intune for the devices to be managed by Autopatch.
- Either Pilot or fully assigned to Intune will work.
- Enable Windows Data under Tenant Administration / Connectors and Token

Reports and monitoring for Windows Autopatch
On top of mail notifications that Microsoft will send to contacts defined, reports are also available.
- Under Reports / Windows Autopatch, two reports are available.


- The other reports under Reports / Device Management / Windows Updates can still be used and can be useful to validate the readiness of the devices for the newest Windows build.
- It is also recommended to configure the Windows Update for business reporting in the Azure portal.
- This will provide great reporting about Delivery Optimization, that isn’t available elsewhere.
- See our blog Configure Windows Update for Business Reporting
- At the moment, there are not built-in reports for Edge or Microsoft 365 Apps.
- Microsoft 365 Apps monitoring can be done from the Microsoft 365 Admin portal
For additional information about Windows Autopatch, see Microsoft Learn.
Keep an eye out for our Windows Autopatch Troubleshooting blog post coming out soon!














Only authorized users can leave comments
Log In