
The goal of this post is to describe the steps needed to implement SCCM Internet-based client management. With the increasing client working from home, this solution would allow you to manage your client on the internet. The other option would be to install a cloud management gateway (CMG)
Download the step-by-step guide in the download section or directly here. For now on, this blog post won’t be updated. Only the document will be.
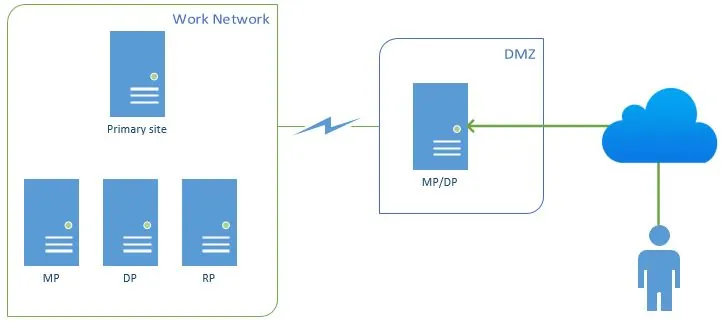
In this scenario, SCCM 2012 R2 is installed as a stand-alone primary site. For security reasons, a second site server will be installed in the DMZ to respond to internet clients’ requests. Internet clients are laptops and tablets that are sometimes on the intranet (work network) and some time on the internet.
Assumption :
- Your primary site server is up and running
- Site server is installed in the DMZ
- Site systems that support Internet-based client management must have connectivity to the Internet and must be in an Active Directory domain.
- The Internet fully qualified domain name (FQDN) of site systems that support Internet-based client management must be registered as host entries on public DNS servers
- Your organisation has a certificate server
- You have a client on the internet for testing purposes
Grab a cup of coffee and here we go !
High level steps :
- Create the needed cerificate
- Issue the certificate on the new machine
- GPO creation for client Auto-Enrollment
- Add the Management Point role and the distribution point role to the new machine
- Test the setup on an internet client
1.1. Overview
The following table lists the types of PKI certificates that is required for System Center 2012 Configuration Manager and describes how they are used.
|
Certificate Requirement |
Certificate Description |
|
Web server certificate for site systems that run IIS |
This certificate is used to encrypt data and authenticate the server to clients. It must be installed externally from Configuration Manager on site systems servers that run IIS and that are configured in Configuration Manager to use HTTPS. This certificate will be installed on any site servers with the Management Point and/or Distribution Point Roles. It is used to encrypt data and authenticate clients. Configure this in IIS. |
|
Client certificate for Windows computers |
This certificate is used to authenticate Configuration Manager client computers to site systems that are configured to use HTTPS. It can also be used for management points and state migration points to monitor their operational status when they are configured to use HTTPS. It must be installed externally from Configuration Manager on computers. |
|
Client certificate for distribution points |
This certificate has two purposes: The certificate is used to authenticate the distribution point to an HTTPS-enabled management point before the distribution point sends status messages. When the Enable PXE support for clients’ distribution point option is selected, the certificate is sent to computers that PXE boot so that they can connect to a HTTPS-enabled management point during the deployment of the operating system. |
1.2. Certificate Creation
WEB SERVER (IIS) CERTIFICATE
This procedure creates a certificate template for Configuration Manager 2012 site systems
To create and issue the Web server certificate template on the certification authority
- Ensure that you have a security group that contains the member servers to install Configuration Manager 2012 site systems that will run IIS. (SCCM_SiteServers)
- RDP to an Intermediate CA
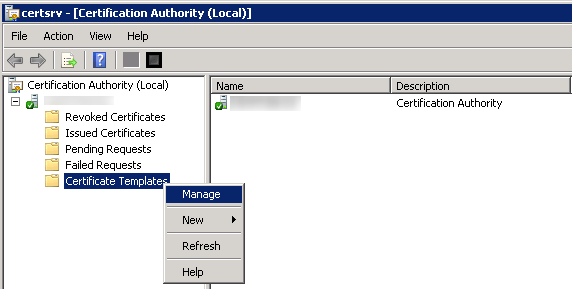
- Open Certification Authority console, right-click Certificate Templates and click Manage
 Right click Web Server and click Duplicate Template.
Right click Web Server and click Duplicate Template.- In the Duplicate Template dialog box, ensure that Windows 2003 Server, Enterprise Edition is selected, and then click OK.Do not select Windows 2008 Server, Enterprise Edition.
- In the Properties, name this “ConfigMgr 2012 IIS Certificate“
- Set the Validity Period to 5 years
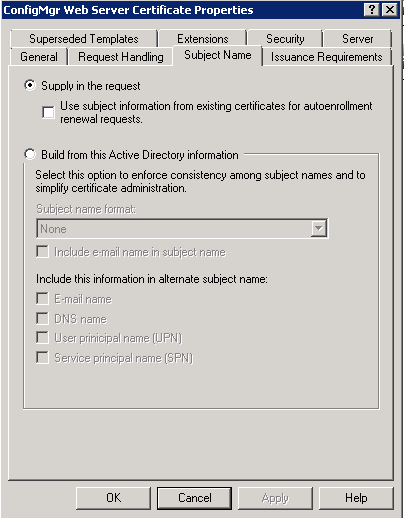
- Click the Subject Name tab, select the Supply in the request radio button.
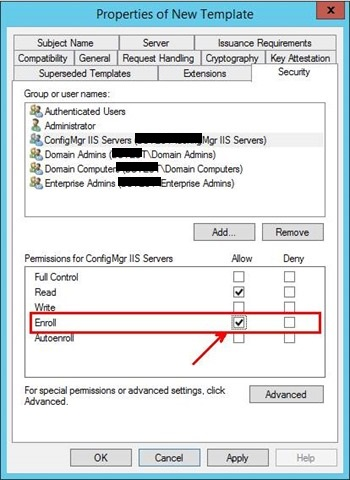
 Click the Security tab, and remove the Enroll permission from the security groups Domain Admins and Enterprise Admins.
Click the Security tab, and remove the Enroll permission from the security groups Domain Admins and Enterprise Admins.- Click Add, enter “SCCM_SiteServer” in the text box, and then click OK.
- Select the Enroll permission for this group, and do not clear the Read permission.
 Click OK, and close the Certificate Templates Console.
Click OK, and close the Certificate Templates Console.
DISTRIBUTION POINT SITE SERVER CERTIFICATE
This procedure creates a certificate template for Configuration Manager 2012 Distribution Points.
- Ensure that you have a security group that contains the member servers to install Configuration Manager 2012 site systems that will run IIS. (SCCM_SiteServers)
- RDP to an Intermediate CA
- Open Certification Authority console, right-click Certificate Templates and click Manage
 Right click Workstation Authentication and click Duplicate Template.
Right click Workstation Authentication and click Duplicate Template.- Rename the template “ConfigMgr 2012 Client Distribution Point Certificate“
- Set the Validity Period to 5 years
- On the Request Handling tab select Allow private key to be exported.
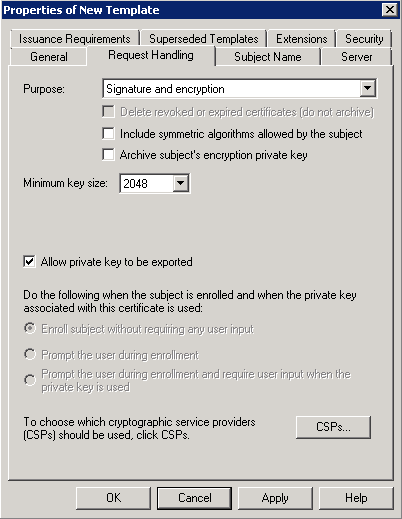 On the Security tab add the “SCCM_SiteServer” group, and give the server Enroll permission. Click Apply, then OK.
On the Security tab add the “SCCM_SiteServer” group, and give the server Enroll permission. Click Apply, then OK.- Now if you look at the Certificate Templates Console you will see our three new templates.
CLIENT CERTIFICATE
This procedure creates a certificate template for Configuration Manager 2012 clients
- RDP to an Intermediate CA
- Open Certification Authority console, right-click Certificate Templates and click Manage
 Right click Workstation Authentication and click Duplicate Template.
Right click Workstation Authentication and click Duplicate Template.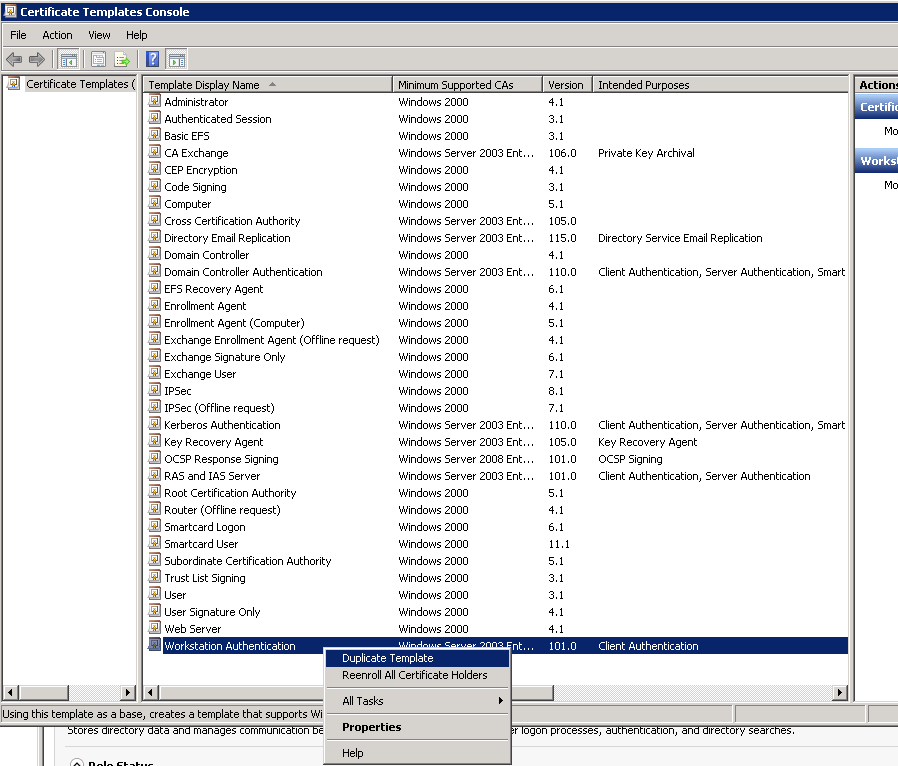 Make sure to use Server 2003, not 2008
Make sure to use Server 2003, not 2008- In the Properties, name this “ConfigMgr 2012 Client Certificate“.
- Set the Validity Period to 5 years
- Click on the Security tab, select the Domain Computers group and add the permissions of Read and Autoenroll, do not clear Enroll. Then click OK.
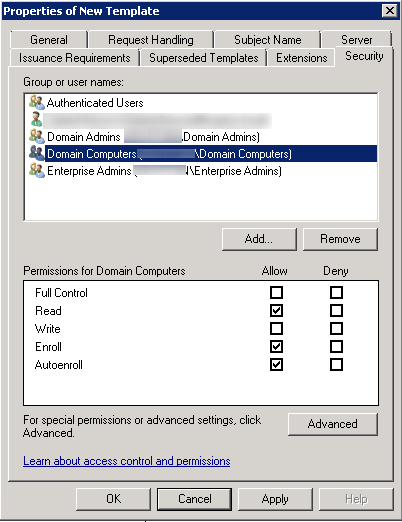 When you refresh your console, you will see that the new template is there.
When you refresh your console, you will see that the new template is there.
1.3. Issuing the 3 certificates
- In the Certification Authority console, right-click Certificate Templates, click New, and then click Certificate Template to Issue.
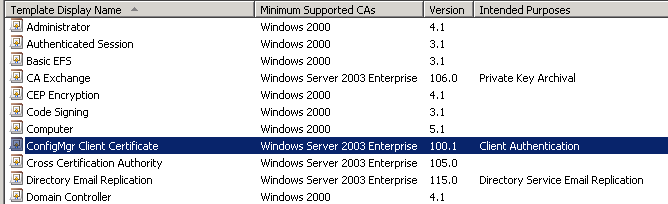
- In the Enable Certificate Templates dialog box, select the 3 new template you have just created :
- ConfigMgr 2012 Client Certificate
- ConfigMgr 2012 IIS Certificate
- ConfigMgr 2012 Client Distribution Point Certificate
- Click OK
- They will then show up in the Certificate Templates listing
- Close Certification Authority.
1.4. Auto-Enroll GPO
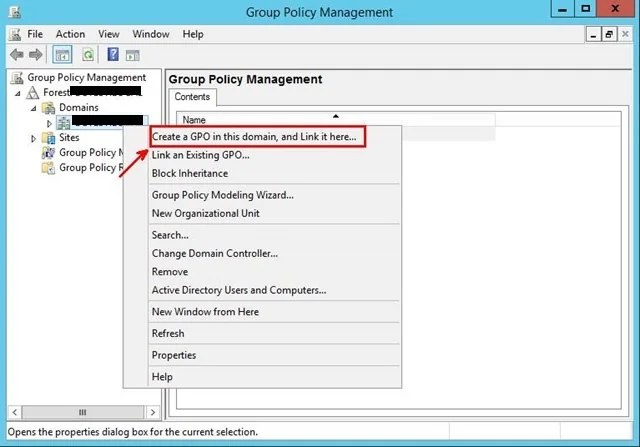
- Launch Group Policy Management on your Domain (Start – Administrative Tools – Group Policy Management).
- Right-click your Laptop OU and select “Create a GPO in this domain, and Link it here…“
- Name your GPO I named my policy “AutoEnroll ConfigMgr Client Cert“, then click OK.
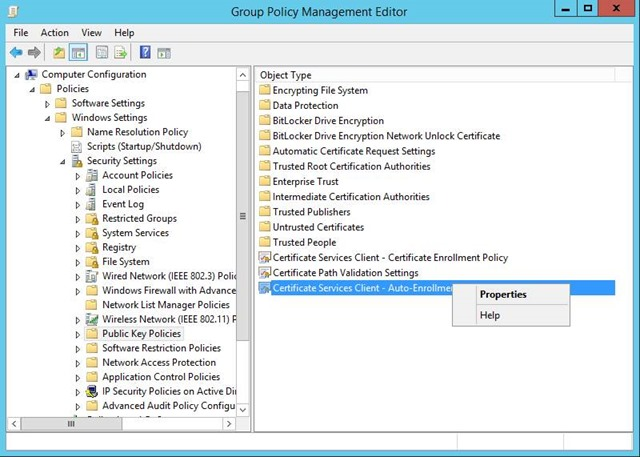
- Edit your newly created GPO. Navigate to: Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies. Right-click on Certificate Services Client – Auto-Enrollment and then click Properties.
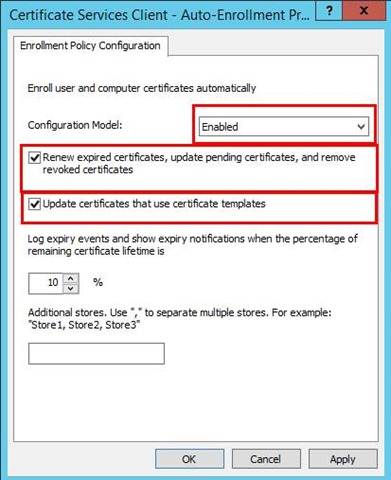
Change the Configuration Model: to Enabled, check the Update certificates that use certificate templates and select Renew expired certificates, update pending certificates. Then click Apply and OK.
Reboot a workstation and when you run a “gpupdate /force” or in 15 minutes when GP is re-applied, any machine on the domain communicating with the DC will request and receive a client certificate automatically that will be place in the Local Computer Personal Certificate Store.
1.5. Distribution Point
REQUEST DISTRIBUTION POINT CERTIFICATE
The same certificate can be used on all DPs. So you only need to do the following steps on the internet facing DP.
- Reboot your SCCM Site server.
- This is so that it will pick up the permissions change that will allow it to register for the Web Server Certificate.
- Once the reboot completes, RDP to your DP server
- Start > Run. Type mmc.exe and click OK
- Click File > Add/Remove Snap-In… Choose Certificates and click Add
- Choose Computer Account, click Next, Choose Local Computer, click Finish
- Click OK, and then expand the Certificates tree to the Personal > Certificates folder.
- Click All Tasks > Request New Certificate…
- You are presented with the Certificate Enrollment wizard.
- Click Next.
- Leave the default here, and click Next
- At the Request Certificates part of the wizard, check the ConfigMgr Client Distribution Point Certificate.
- Click Enroll and then finish once the enrollment is successful.
- Now we need to export the Client Distribution Point Certificate while we are in the Certificates Management console.
- Right-click the certificate and select All Tasks > Export
- Click Next at the Welcome Screen of the export wizard. Then on the Export Private Key page change this to YES then click Next.
- Next, select Personal Information Exchange – PKCS #12 (.PFX) and then click Next.
- Set a password (15 car.) and document it
- Save the file as SCCM DP Certificate to a network location
- The reason for this export is that we will later be importing this certificate into SCCM DP and we need to do so in pkcs12 format, with a password protected private key included.
1.6. Management Point
REQUEST CM2012 IIS CERTIFICATE
This shall be done on the Management point that will handle internet client requests.
- Start > Run. Type mmc.exe and click OK
- Click File > Add/Remove Snap-In… Choose Certificates and click Add
- Choose Computer Account, click Next, Choose Local Computer, click Finish
- Click OK, and then expand the Certificates tree to the Personal > Certificates folder.
- Click All Tasks > Request New Certificate…
- You are presented with the Certificate Enrollment wizard.
- Click Next.
- Leave the default here, and click Next
- At the Request Certificates part of the wizard, check the ConfigMgr 2012 IIS Certificate.
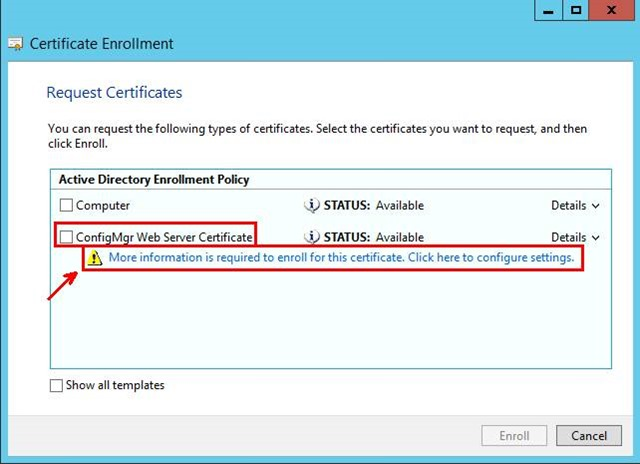 You will notice that under the Web cert, a prompt that says, “More information is required to enroll for this certificate. Click here to configure settings”
You will notice that under the Web cert, a prompt that says, “More information is required to enroll for this certificate. Click here to configure settings”- Click the link and setup your Certificate Properties.
- For Subject name, select Common name and use the server name as the common name.
- For Alternative name, select DNS and use the server name as well as its FQDN as DNS.
- In General tab, use the server name as the friendly name.
- In Certification Authority tab, select only your regional CA.
- Click Add and then OK.
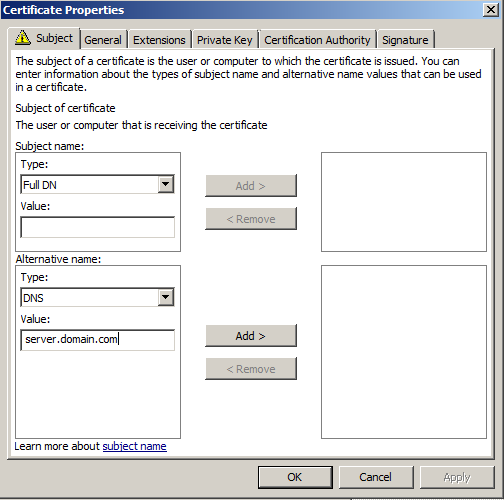 Then the warning field will disappear from the Request Certificates screen of the Certificate Enrollment wizard
Then the warning field will disappear from the Request Certificates screen of the Certificate Enrollment wizard- Click Enroll and then finish once the enrollment is successful.
ASSIGN THE WEB (IIS) CERTIFICATE TO IIS
This shall be done on the Management point that will handle internet client requests.
- Launch IIS Manager
- Navigate to the Default Website
- Right-click it and select Edit Bindings
- Add https binding and click Edit
- Select the certificate with your server name, and then click OK.
1.7. Add the new site system in SCCM
Ensure that all your certificate actions are done before adding the roles.
PREREQUISITES
- RDP to your DMZ Site server
- Add the following prerequisites in Server Features
| Management Point |
.NET Framework 3.5 SP1 Default IIS with: ISAPI Extensions Windows Authentication IIS 6 Metabase Compatibility IIS 6 WMI Compatibility BITS Server Extensions |
|
Distribution Point |
Default IIS with: ISAPI Extensions Windows Authentication IIS 6 Metabase Compatibility IIS 6 WMI Compatibility BITS Server Extensions Remote Differential Compression |
ROLES INSTALLATION
- Open the SCCM console
- Administration / Servers and site system role
- Create site system server
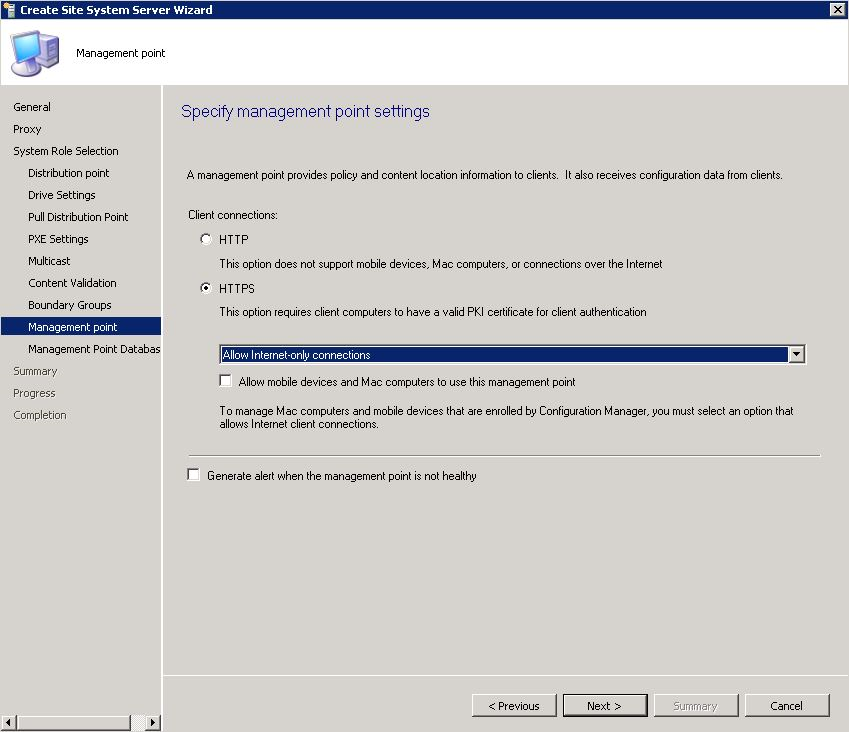
- Specify the new site server name and specify the internet FQDN
- Select the DP and MP role
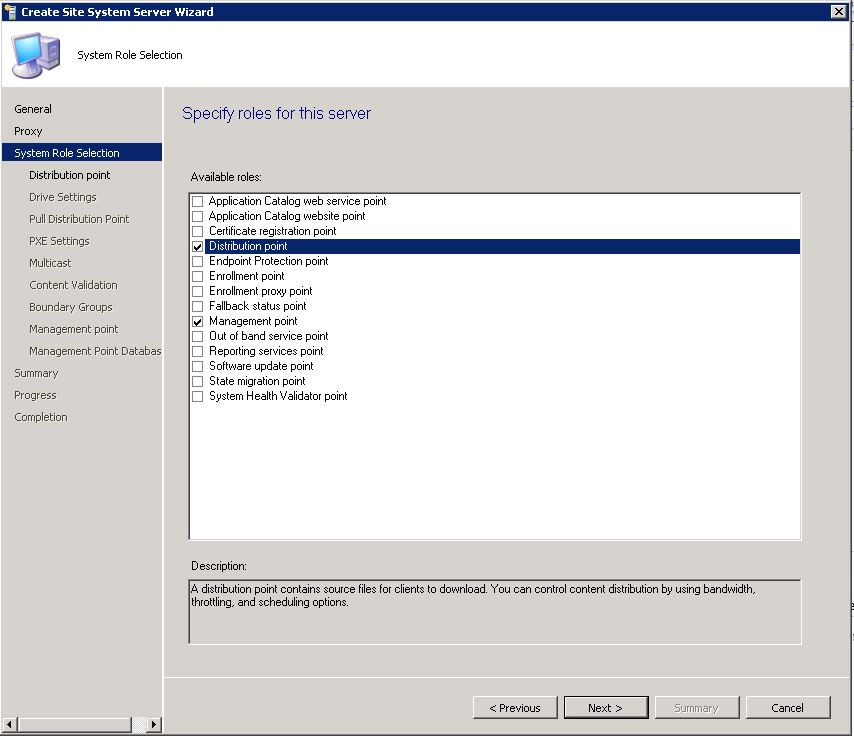
- Configure the ConfigMgr Client Distribution Point certificate (the .PFX created in previous section) supply the password and OK.
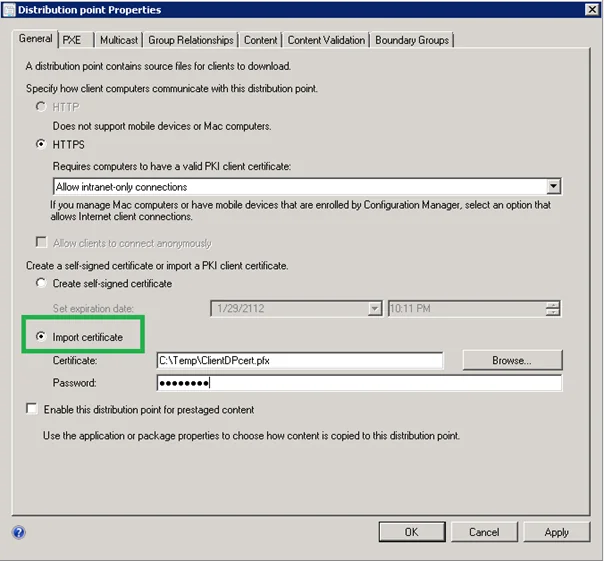 Choose HTTPS and “Allow Internet-Only connections”
Choose HTTPS and “Allow Internet-Only connections”
1.8. Change SCCM client communication settings
This shall be done on each of primary site server
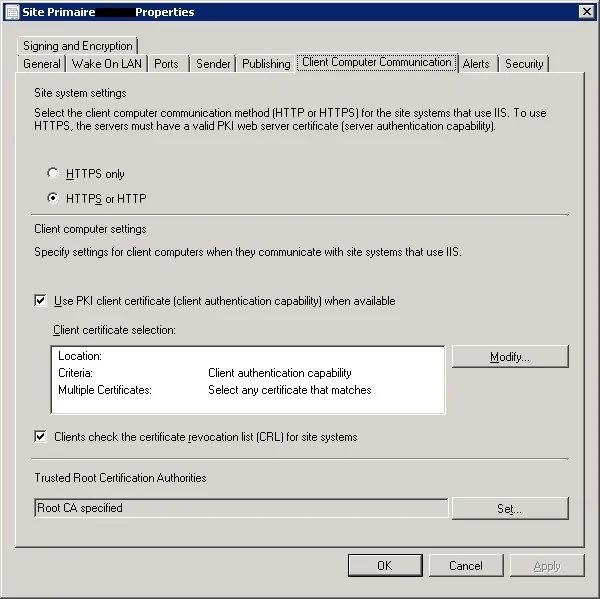
- Go to Administration –> Sites –> Right click and choose properties
- Go to client computer communication –> Choose use HTTPS or HTTP
- Check the “Use PKI client certificate when available” checkbox
- Import the Root CA certificate in the bottom menu
1.8.Client installation
Client push is not supported on the internet. The client must be installed on your network before it can go on the internet.
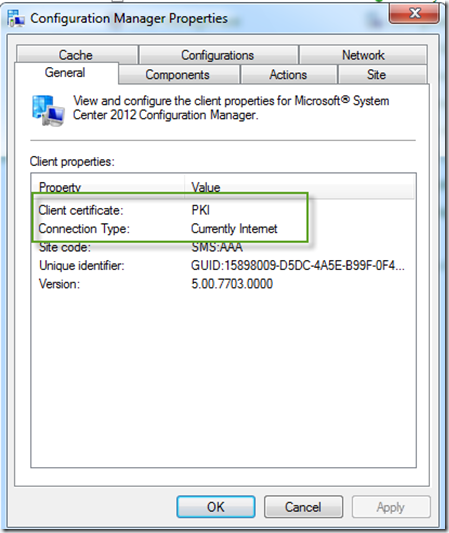
The logic behind this is that the client will first try to communicate with the intranet MP, if sucessful the client will show “Currently Intranet”. If it fail, it will try to reach the internet MP and shows “Currently Internet”. When the laptop will be back at the office, it will return to the intranet MP. The evaluation is done when the computer gets its IP address.
You have different option to do so :
- You can manually add the new MP FQDN in the “Network” tab of the client properties
- You can include the Client.msi property of CCMHOSTNAME=<Internet FQDN of the Internet-based management point> when you install the client, for example by using manual installation or client push. When you use this method, you must also directly assign the client to the site and cannot use automatic site assignment.
- Configure clients for Internet-based client management after client installation by using a script
——-start of script————–
on error resume next
‘ Create variables.
Dim newInternetBasedManagementPointFQDN
Dim client
newInternetBasedManagementPointFQDN = “mp.yourorganisation.com”
‘ Create the client COM object.
Set client = CreateObject (“Microsoft.SMS.Client”)
‘ Set the Internet-Based Management Point FQDN by calling the SetCurrentManagementPoint method.
client.SetInternetManagementPointFQDN newInternetBasedManagementPointFQDN
‘ Clear variables.
Set client = Nothing
Set internetBasedManagementPointFQDN = Nothing
——-end of script————–
***Replace mp.yourorganisation.com with the Internet FQDN of your Internet-based management point.
1.9 Test your clients
- After installing a client on internet make sure that you are using HTTPS by looking at the “Connection Type” is Internet
- You can also review the ClientLocation.log and datatransfer.log to ensure that your new MP is used
That was intense… Until next time !
See this Technet blog post to fix common issues : Here















Nagayya
09.20.2019 AT 12:36 AMtelekill rules of survival
11.23.2018 AT 08:20 PMCristhian Reyes
11.07.2018 AT 05:54 PMVishal
10.08.2018 AT 10:40 AMdcrescendo
08.31.2018 AT 03:00 PMChristopher Moriarty
08.15.2017 AT 01:52 PMBeau
07.07.2017 AT 11:12 AMChristopher Moriarty
06.16.2017 AT 03:13 PMThomas
06.13.2017 AT 05:08 PMMike
05.19.2017 AT 12:34 PMsometechstuff
05.11.2017 AT 08:39 AMAndrew
04.21.2017 AT 01:07 PMGlen
04.13.2017 AT 08:05 AMBenoit Lecours
04.13.2017 AT 08:12 AMShawn M
10.12.2017 AT 10:18 AMDamon B
01.24.2017 AT 11:22 AMTim
03.08.2017 AT 03:48 PMNick
12.14.2016 AT 04:47 PMAl Kongsjord
07.22.2016 AT 10:02 AMPeter
06.09.2016 AT 08:22 AMSimon Bond
05.05.2016 AT 07:07 AMShailendra Dev
03.03.2016 AT 02:03 PM